Visualizing sketchy ad networks
Introduction This post will be an attempt at visualizing some of the strategies used by attackers...

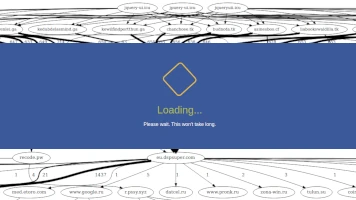
WhiteRabbit Hosting Hack
(Last edit: 2023-01-30 21:00, first version 2022-11-03 18:12) Summary of WhiteRabbit attack Ma...

FRA Challenge 2021-09
Finally back to a classic FRA challenge. This one turned out to be more of a programming/engineering...

FRA Challenge 2020-1 (Updated)
Updated: 2022-10-23. (I first wrote the intro back in 2020 when this was active but I didn't want to...
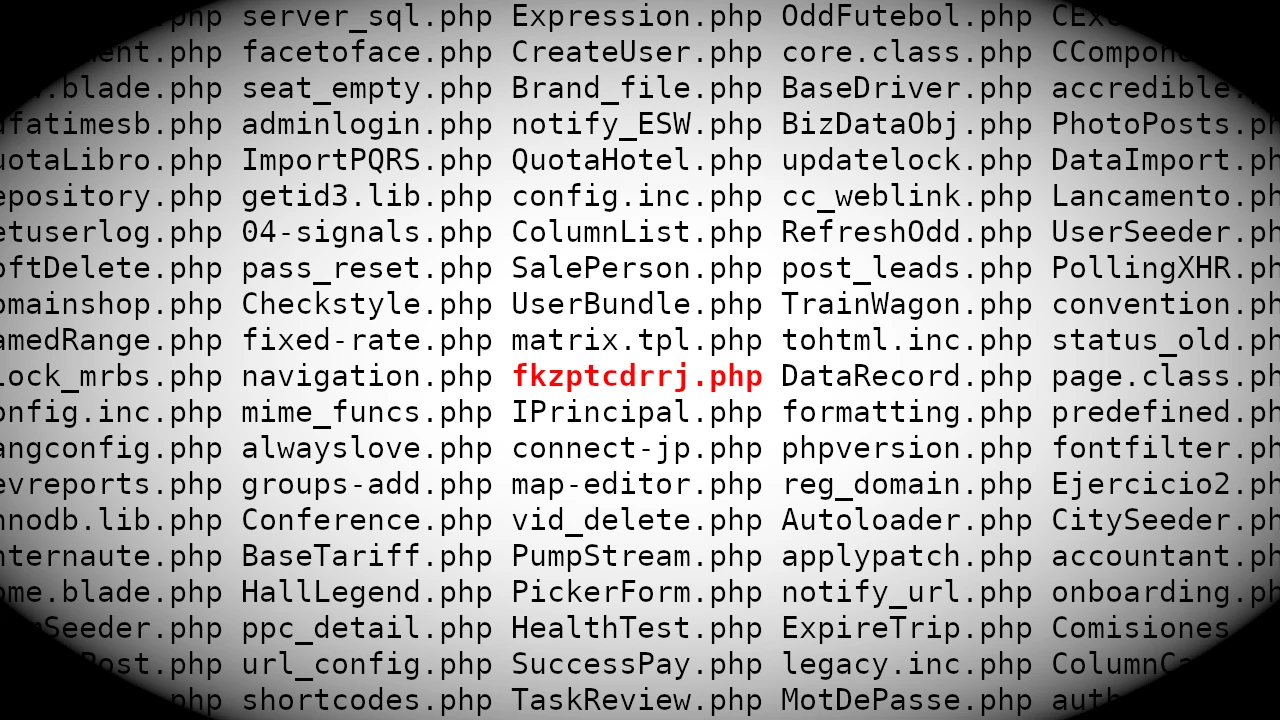
Searching for Random
As I was "casually" surfing the web I stumbled upon some PHP files with random names. It turns out t...

I waited 10 months for you
This is just a short story of how I set up a honeypot and waited 10 months for a single request. And...
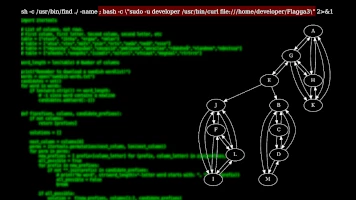
FRA-knäck Write-up
Intro This year our friends at FRA did something new and hosted a sort of Christmas crafts compet...
Updates!
I just wanted to share some updates here on my website! :) New real security challenges I've s...
Hash Game is back!
For more than 3 years "The famous HASH game" has been unavailable but now I'm happy to announce that...

Improving web shells with asymmetric encryption
You're out surfing the world wide web having a great time, then suddenly, you find a security vuln...
FRA Challenge 2019-2
In this post we continue on the topic of FRA challenges. This challengemirror is quite different f...

FRA Challenge 2019-1
It's the end of the year and a nice time to look at the security challenges posed by our Swedish S...
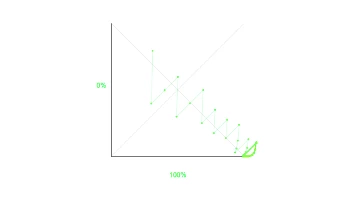
The Internet shouldn't work
Greed is good, or is it? Cue the Vsauce intro. Have you ever thought, "How does the Internet w...
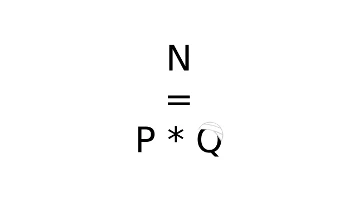
Backdooring RSA
You have probably heard about backdoors in different software, the dlink user-agent backdoor[1] ...

Self referential checksums
Checksums and hashes are great for detecting errors and modifications of data, but what if your data...

Reversing the reverser
Most apps on your phone can interact with the Internet. By analysing the details of these interactio...

Anonymous comments
Why is no one using anonymous comments anymore? Either you have to register for yet another site or ...

TS-Streams and Exercising
A few weeks ago my girlfriend showed me that the gym she goes to had started to upload instruct...

Optimal strategy for Fallout terminal hacking
Introduction If you've played the modern Fallout series you have without a doubt also tried to hack...