 | 1.php | Execution, Input | 91839a91eba0378d96673712343c20ca |
 | tokenbbvafncs3.zip | | 91db6a0c8dcbdf30e798619a3dc40f53 |
 | raw | Encoding, Files, Input | 91e2f2d857dae3404b09cb55f60fd827 |
 | %22><img src=x onerror=alert(1)%22>.jpg, %2fetc%2fpasswd, %31%3C%53%63%52%69%50%74%20%3E%72%45%59%6A%289229%29%3C%2F%73%43%72%69%70%54%3E, %c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c, ^(#$!@#$)(()))******, <%={{={@{#{${acx}}%>, 081226077336.test%22.png, 1%3C%53%63%52%3C%53%63%52%69%50%74%3E%49%70%54%3E%72%45%59%6A%28%39%34%37%31%29%3C%2F%73%43%72%3C%53%63%52%69%50%74%3E%49%70%54%, 1<svg ��
�, 1some_inexistent_file_with_long_name%00.jpg, acu7012%EF%BC%9Cs1%EF%B9%A5s2%CA%BAs3%CA%B9uca7012, acux4496%C0%BEz1%C0%BCz2a%90bcxuca4496, ALFA%20TEaM%20Shell.php, anubiskun.php?a=.xlsx, c99.txt?, C99madShell%20v.%202.0%20madnet%20edition.php, file#, fit.txt%3F.jpg, log.php?, mini.php3?, nz^xyu||a #|, passwd%00, passwd%00.jpg, payload.php%00.jpg, some_inexistent_file_with_long_name%3F.jpg, win.ini%00.jpg, zup.phP<?.jpg | Emails, Title, URLs | 91e38f54dc7aa44e2fc28ea427210cf5 |
 | file.txt | | 920e4a23cac78ba23555725fc6f42b68 |
 | Bypass_Uploader_V1.php | Environment, Files, Input | 9237ce996f6d64826f97c1219f2e21f0 |
 | awd.txt | | 923c47990e070f5a821362d9ccdfb7a5 |
 | csrf.html | URLs | 92618eda7ab79471f97cb06859959fa6 |
 | 1<img src=xyz OnErRor=rEYj(9170)> | | 9263a5a5fbf0fd517f8c9c64aca81e77 |
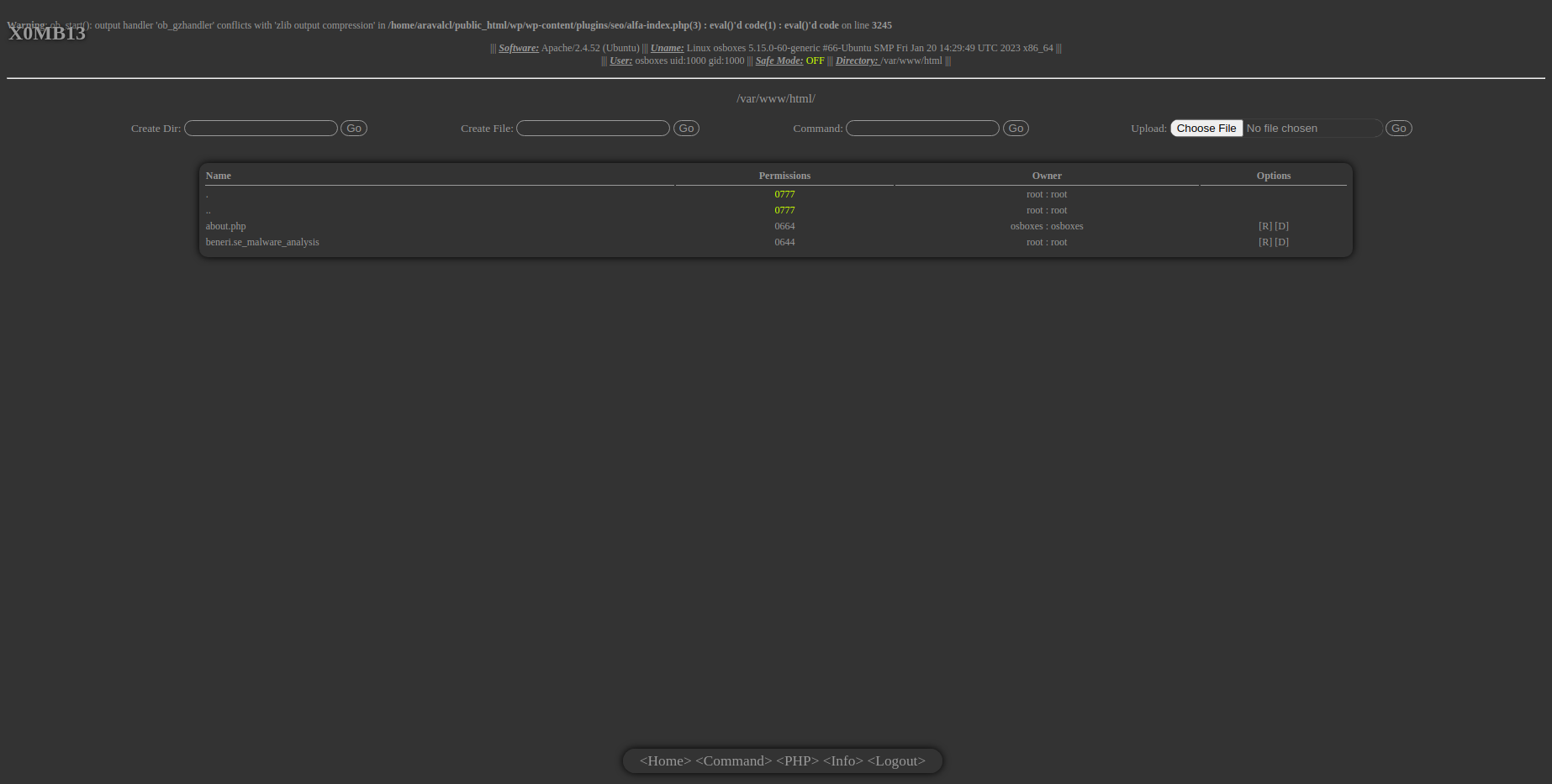 | about.php | Emails, Encoding, Environment, Execution, Files, Input, Title, URLs | 926d96088e029d700433a3082b9f432d |